
It’s been seven years since Stuxnet, the computer worm thought to have been built as an American-Israeli cyberweapon, infected Iran’s nuclear facilities and caused damage that set the country’s nuclear program back by two years. Now, a derivative of the malicious software has infected over one hundred banks and other financial institutions around the world.
Russian cybersecurity company and anti-virus group Kaspersky Lab first discovered the new malware, called Duqu 2.0, on its corporate network back in 2014. As it resides almost completely in the memory of the computers, it went undetected for six months or more, reports Ars Technica.
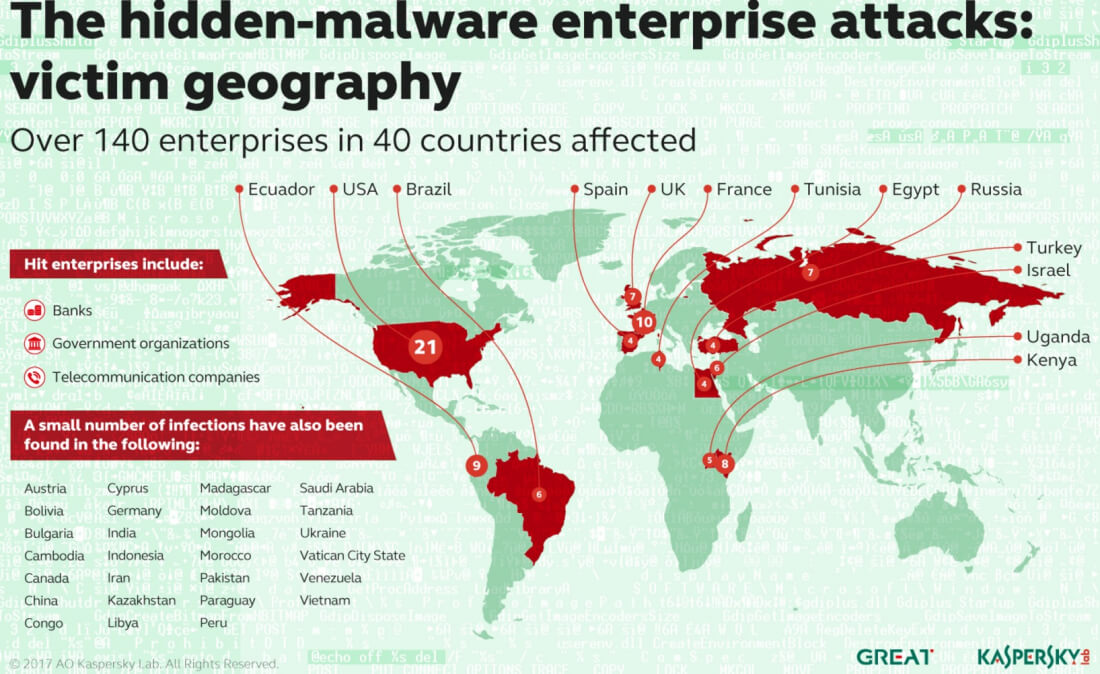
New research from Kaspersky claims the invisible, fileless malware has gone mainstream and is now found on networks in 40 countries belonging to at least 140 institutions, including banks, government organizations, and telecommunication companies. There have been 21 instances in the US, though the actual number could be much higher, given how hard it is to detect.
Once an infected computer is rebooted, the malware renames itself, making it difficult for digital forensic experts to find any traces of the malware. It was only discovered by a bank’s security team after it found a copy of Meterpreter—an in-memory component of Metasploit—inside the physical memory of a Microsoft domain controller. Researchers found that the Meterpreter code was downloaded and injected into memory using PowerShell commands.
"We're looking at the common denominator across all of these incidents, which happens to be this odd use in embedding PowerShell into the registry in order to download Meterpretor and then carry out actions from there with native Windows utilities and system administrative tools," Kaspersky Lab expert Kurt Baumgartner told Ars.
To what extent the malware's presence could affect consumers who use the infected financial institutions is unclear. Kaspersky Labs said it will provide further details of the attacks and their objectives at the Security Analyst Summit in April.
https://www.techspot.com/news/68098-type-fileless-malware-related-stuxnet-has-infected-over.html