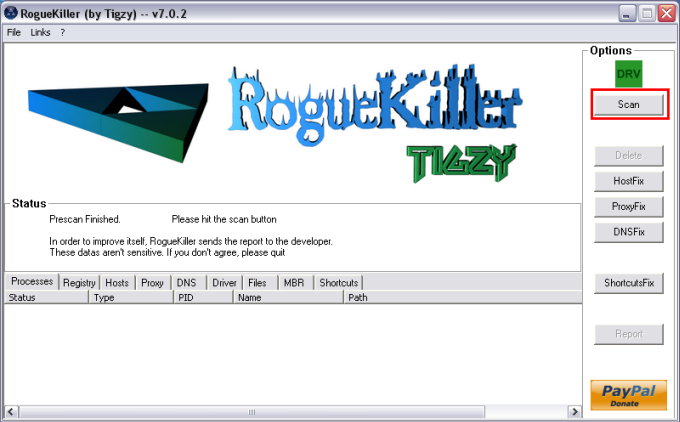
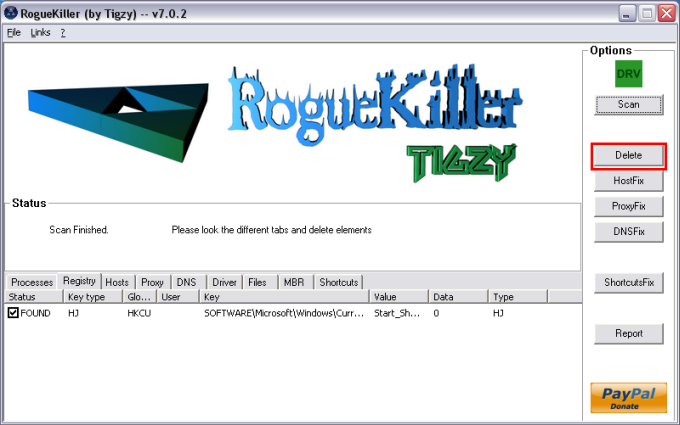
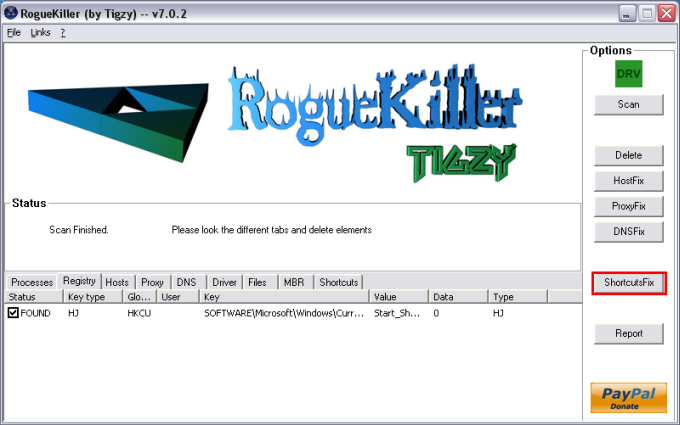
Here you are. I assume from the instructions that I do not need to report the outputs from the '5 steps'? Here is the output from frst64.exe....
Scan result of Farbar Recovery Scan Tool Version: 05-08-2012 03
Ran by SYSTEM at 07-08-2012 21:24:23
Running from K:\
Windows Vista (TM) Home Premium (X64) OS Language: English(US)
The current controlset is ControlSet001
========================== Registry (Whitelisted) =============
HKLM\...\Run: [RtHDVCpl] RAVCpl64.exe [x]
HKLM\...\Run: [Skytel] Skytel.exe [x]
HKLM\...\Run: [PMX Daemon] ICO.EXE [x]
HKLM\...\Run: [LogMeIn GUI] "P:\Program Files (x86)\LogMeIn\x64\LogMeInSystray.exe" [x]
HKLM\...\Run: [Kernel and Hardware Abstraction Layer] KHALMNPR.EXE [x]
HKLM\...\Run: [MSC] "C:\Program Files\Microsoft Security Client\msseces.exe" -hide -runkey [1271168 2012-03-26] (Microsoft Corporation)
HKLM-x32\...\Run: [] [x]
HKLM-x32\...\Run: [AgentMonitor] "C:\Program Files (x86)\VTech\DownloadManager\System\AgentMonitor.exe" [357800 2011-12-12] ()
HKLM-x32\...\Run: [Adobe ARM] "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [843712 2012-01-02] (Adobe Systems Incorporated)
HKU\Default\...\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem [1555968 2009-04-10] (Microsoft Corporation)
HKU\Default User\...\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem [1555968 2009-04-10] (Microsoft Corporation)
HKU\John\...\Run: [GoodSync] "p:\Program Files\Siber Systems\GoodSync\GoodSync.exe" /min [x]
HKU\John\...\Run: [ehTray.exe] C:\Windows\ehome\ehTray.exe [138240 2008-01-20] (Microsoft Corporation)
HKU\John\...\Run: [Google Update] "C:\Users\John\AppData\Local\Google\Update\GoogleUpdate.exe" /c [135664 2010-01-07] (Google Inc.)
HKU\John\...\Run: [chromium] C:\Users\John\AppData\Local\Google\Chrome\Application\chrome.exe --no-startup-window [1229848 2012-07-30] (Google Inc.)
Tcpip\Parameters: [DhcpNameServer] 71.243.0.12 68.237.161.12 192.168.1.1
Startup: C:\Users\All Users\Start Menu\Programs\Startup\APC UPS Status.lnk
ShortcutTarget: APC UPS Status.lnk -> C:\Program Files (x86)\APC\APC PowerChute Personal Edition\Display.exe (No File)
Startup: C:\Users\All Users\Start Menu\Programs\Startup\Conversion to PDF with ScanSnap Organizer.lnk
ShortcutTarget: Conversion to PDF with ScanSnap Organizer.lnk -> C:\Program Files (x86)\PFU\ScanSnap\Organizer\PfuSsOrgOcrChk.exe (PFU LIMITED)
Startup: C:\Users\All Users\Start Menu\Programs\Startup\ScanSnap Manager.lnk
ShortcutTarget: ScanSnap Manager.lnk -> C:\Program Files (x86)\PFU\ScanSnap\Driver\PfuSsMon.exe (PFU LIMITED)
Startup: C:\Users\All Users\Start Menu\Programs\Startup\Windows Home Server.lnk
ShortcutTarget: Windows Home Server.lnk -> C:\Windows\Installer\{21E49794-7C13-4E84-8659-55BD378267D5}\WHSTrayApp.exe (Microsoft Corporation)
Startup: C:\Users\John\Start Menu\Programs\Startup\Dropbox.lnk
ShortcutTarget: Dropbox.lnk -> (No File)
==================== Services (Whitelisted) ======
4 AcronisOSSReinstallSvc; "C:\Program Files (x86)\Common Files\Acronis\Acronis Disk Director\oss_reinstall_svc.exe" [2217416 2007-02-26] ()
4 AcrSch2Svc; "C:\Program Files (x86)\Common Files\Seagate\Schedule2\schedul2.exe" [571424 2007-04-19] (Acronis)
2 AERTFilters; C:\Windows\System32\AERTSr64.exe [86016 2008-07-18] (Andrea Electronics Corporation)
2 arXfrSvc; "C:\Program Files\Windows Home Server\Microsoft.HomeServer.Archive.TransferService.exe" [231280 2011-01-10] (Microsoft Corporation)
2 esClient; "C:\Program Files\Windows Home Server\esClient.exe" [109936 2011-01-10] (Microsoft Corporation)
2 HPMSSConnectorSvc; "C:\Program Files\Hewlett-Packard\HP MediaSmart Server\MSSConnectorService.exe" [20992 2009-10-05] (HP)
4 LBTServ; C:\Program Files\Common Files\Logitech\Bluetooth\LBTServ.exe [160272 2008-05-01] (Logitech, Inc.)
4 LoClntService; "C:\Program Files\Windows Home Server\LightsOutClientService.exe" [49152 2010-11-14] (AxoNet Software GmbH)
2 MediaCollectorService; "C:\Program Files\Hewlett-Packard\HP MediaSmart Server\MediaCollectorClient.exe" [81920 2009-10-05] (Hewlett-Packard Company)
2 MsMpSvc; "C:\Program Files\Microsoft Security Client\MsMpEng.exe" [12600 2012-03-26] (Microsoft Corporation)
3 NisSrv; "C:\Program Files\Microsoft Security Client\NisSrv.exe" [291696 2012-03-26] (Microsoft Corporation)
2 NovacomD; C:\Program Files\Palm, Inc\novacom\amd64\novacomd.exe [71168 2011-03-15] (Palm)
4 stllssvr; "C:\Program Files (x86)\Common Files\SureThing Shared\stllssvr.exe" [74384 2008-03-24] (MicroVision Development, Inc.)
2 TivoBeacon2; "C:\Program Files (x86)\Common Files\TiVo Shared\Beacon\TiVoBeacon.exe" /service [868864 2008-07-09] (TiVo Inc.)
2 vmware-converter-agent; "C:\Program Files (x86)\VMware\VMware vCenter Converter Standalone\vmware-converter-a.exe" -s "C:\ProgramData\VMware\VMware vCenter Converter Standalone\converter-agent.xml" [6285 2012-01-31] ()
2 vmware-converter-server; "C:\Program Files (x86)\VMware\VMware vCenter Converter Standalone\vmware-converter.exe" -s "C:\ProgramData\VMware\VMware vCenter Converter Standalone\converter-server.xml" [4291 2012-01-31] ()
2 vmware-converter-worker; "C:\Program Files (x86)\VMware\VMware vCenter Converter Standalone\vmware-converter.exe" -s "C:\ProgramData\VMware\VMware vCenter Converter Standalone\converter-worker.xml" [6897 2012-01-31] ()
2 WHSConnector; "C:\Program Files\Windows Home Server\WHSConnector.exe" [489840 2011-01-10] (Microsoft Corporation)
4 wltrysvc; C:\Windows\System32\WLTRYSVC.EXE C:\Windows\System32\bcmwltry.exe [1889792 2007-08-07] (Dell Inc.)
2 APC UPS Service; C:\Program Files (x86)\APC\APC PowerChute Personal Edition\mainserv.exe [x]
2 GsServer; C:\Program Files\Siber Systems\GoodSync\Gs-Server.exe /service [x]
3 hpqcxs08; C:\Program Files (x86)\HP\Digital Imaging\bin\hpqcxs08.dll [x]
2 hpqddsvc; C:\Program Files (x86)\HP\Digital Imaging\bin\hpqddsvc.dll [x]
2 HPSLPSVC; C:\Program Files (x86)\HP\Digital Imaging\bin\HPSLPSVC64.DLL [x]
2 LMIGuardianSvc; "C:\Program Files (x86)\LogMeIn\x64\LMIGuardianSvc.exe" [x]
2 LMIMaint; "C:\Program Files (x86)\LogMeIn\x64\RaMaint.exe" [x]
2 LogMeIn; "C:\Program Files (x86)\LogMeIn\x64\LogMeIn.exe" [x]
4 PD91Agent; "C:\Program Files\Raxco\PerfectDisk2008\PD91Agent.exe" [x]
4 PD91Engine; "C:\Program Files\Raxco\PerfectDisk2008\PD91Engine.exe" [x]
2 SessionLauncher; C:\Users\John\AppData\Local\Temp\DX9\SessionLauncher.exe [x]
2 SkypeUpdate; "C:\Program Files (x86)\Skype\Updater\Updater.exe" [x]
========================== Drivers (Whitelisted) =============
3 bmdrvr; C:\Windows\SysWow64\Drivers\bmdrvr.sys [74352 2011-03-14] (VMware, Inc.)
1 cbfs3; C:\Windows\System32\Drivers\cbfs3.sys [340880 2011-09-02] (EldoS Corporation)
3 libusb0; C:\Windows\System32\Drivers\libusb0.sys [43456 2011-09-22] (
http://libusb-win32.sourceforge.net)
3 lmimirr; C:\Windows\System32\Drivers\lmimirr.sys [11552 2008-07-24] (LogMeIn, Inc.)
2 LMIRfsDriver; C:\Windows\System32\Drivers\LMIRfsDriver.sys [72216 2008-07-24] (LogMeIn, Inc.)
3 LVPr2M64; C:\Windows\System32\Drivers\LVPr2M64.sys [30232 2009-04-30] ()
3 LVPr2Mon; C:\Windows\System32\DRIVERS\LVPr2M64.sys [30232 2009-04-30] ()
3 mr7910; C:\Windows\System32\Drivers\mr7910.sys [55808 2007-03-16] (Mars Semiconductor Corp.)
3 pmxmouse; C:\Windows\System32\Drivers\pmxmouse.sys [22016 2007-06-01] (Primax Electronics Ltd.)
3 pmxusblf; C:\Windows\System32\Drivers\pmxusblf.sys [24384 2007-05-24] (Primax Electronics Ltd.)
3 radpms; C:\Windows\System32\Drivers\radpms.sys [14944 2010-12-15] (LogMeIn, Inc.)
2 RtNdPt60; C:\Windows\System32\Drivers\RtNdPt60.sys [26624 2008-07-21] (Windows (R) Codename Longhorn DDK provider)
0 Si3531; C:\Windows\System32\Drivers\Si3531.sys [333864 2009-02-09] (Silicon Image, Inc)
0 SiFilter; C:\Windows\System32\DRIVERS\SiWinAcc.sys [22568 2009-02-09] (Silicon Image, Inc.)
0 SiRemFil; C:\Windows\System32\Drivers\SiRemFil.sys [16936 2009-02-09] (Silicon Image, Inc.)
0 snapman; C:\Windows\System32\Drivers\snapman.sys [276064 2011-05-04] (Acronis)
3 ViaUsbModemDriver; C:\Windows\System32\DRIVERS\VIA_USB_MODEM.sys [28160 2011-10-04] ()
3 VIA_USB_ETS; C:\Windows\System32\Drivers\VIA_USB_ETS.sys [21760 2011-10-04] (Via Telecom, Inc.)
2 {1E444BE9-B8EC-4ce6-8C2B-6536FB7F4FB7}; \??\C:\Program Files (x86)\CyberLink\PowerDVD DX\000.fcl [146928 2009-04-02] (CyberLink Corp.)
3 AtiHDAudioService; C:\Windows\System32\drivers\AtihdLH6.sys [x]
3 IpInIp; C:\Windows\System32\DRIVERS\ipinip.sys [x]
1 iynwbebw; \??\C:\Windows\system32\drivers\iynwbebw.sys [x]
1 lcayddei; \??\C:\Windows\system32\drivers\lcayddei.sys [x]
2 LMIInfo; \??\P:\Program Files (x86)\LogMeIn\x64\RaInfo.sys [x]
4 LMIRfsClientNP; [x]
3 NwlnkFlt; C:\Windows\System32\DRIVERS\nwlnkflt.sys [x]
3 NwlnkFwd; C:\Windows\System32\DRIVERS\nwlnkfwd.sys [x]
3 VBoxNetFlt; C:\Windows\System32\DRIVERS\VBoxNetFlt.sys [x]
========================== NetSvcs (Whitelisted) ===========
============ One Month Created Files and Folders ==============
2012-08-07 21:24 - 2012-08-07 21:24 - 00000000 ____D C:\FRST
2012-08-06 19:02 - 2012-08-06 19:02 - 00000950 ____A C:\Users\Public\Desktop\Malwarebytes Anti-Malware.lnk
2012-08-06 19:02 - 2012-08-06 19:02 - 00000000 ____D C:\Users\John\AppData\Roaming\Malwarebytes
2012-08-06 19:02 - 2012-08-06 19:02 - 00000000 ____D C:\Users\All Users\Malwarebytes
2012-08-06 19:02 - 2012-08-06 19:02 - 00000000 ____D C:\Program Files (x86)\Malwarebytes' Anti-Malware
2012-08-06 19:02 - 2012-07-03 09:46 - 00024904 ____A (Malwarebytes Corporation) C:\Windows\System32\Drivers\mbam.sys
2012-08-06 18:44 - 2012-08-06 18:44 - 00000000 ____D C:\Program Files\Microsoft Security Client
2012-08-06 18:44 - 2012-08-06 18:44 - 00000000 ____D C:\Program Files (x86)\Microsoft Security Client
============ 3 Months Modified Files ========================
2012-08-07 17:15 - 2009-06-18 05:37 - 00000012 ____A C:\Windows\bthservsdp.dat
2012-08-07 17:15 - 2006-11-02 07:42 - 00032586 ____A C:\Windows\Tasks\SCHEDLGU.TXT
2012-08-07 17:15 - 2006-11-02 07:42 - 00000006 ___AH C:\Windows\Tasks\SA.DAT
2012-08-07 17:15 - 2006-11-02 07:22 - 00003616 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-1.C7483456-A289-439d-8115-601632D005A0
2012-08-07 17:15 - 2006-11-02 07:22 - 00003616 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-0.C7483456-A289-439d-8115-601632D005A0
2012-08-07 17:02 - 2012-04-11 19:15 - 00000830 ____A C:\Windows\Tasks\Adobe Flash Player Updater.job
2012-08-07 16:56 - 2010-01-07 19:47 - 00000904 ____A C:\Windows\Tasks\GoogleUpdateTaskUserS-1-5-21-2351272357-4184536305-1135799588-1000UA.job
2012-08-07 16:56 - 2010-01-07 19:47 - 00000852 ____A C:\Windows\Tasks\GoogleUpdateTaskUserS-1-5-21-2351272357-4184536305-1135799588-1000Core.job
2012-08-07 16:45 - 2006-11-02 04:46 - 00710782 ____A C:\Windows\System32\PerfStringBackup.INI
2012-08-07 16:44 - 2008-11-04 07:00 - 01917853 ____A C:\Windows\WindowsUpdate.log
2012-08-07 16:38 - 2012-01-27 19:46 - 00023728 ____A C:\Windows\PFRO.log
2012-08-07 16:38 - 2011-10-06 08:16 - 00000890 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job
2012-08-07 16:38 - 2008-11-07 08:56 - 00000000 ____A C:\Windows\System32\Drivers\lvuvc.hs
2012-08-07 16:38 - 2008-11-04 12:14 - 00000288 ____A C:\Windows\Tasks\RtlNICDiagVistaStart.job
2012-08-07 16:33 - 2012-01-27 19:41 - 00020339 ____A C:\Windows\setupact.log
2012-08-07 15:34 - 2011-10-06 08:16 - 00000894 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job
2012-08-06 19:02 - 2012-08-06 19:02 - 00000950 ____A C:\Users\Public\Desktop\Malwarebytes Anti-Malware.lnk
2012-08-06 18:44 - 2011-02-06 13:11 - 00001945 ____A C:\Windows\epplauncher.mif
2012-08-06 18:44 - 2009-06-03 12:09 - 00725630 ____A C:\Windows\SysWOW64\PerfStringBackup.INI
2012-08-02 11:02 - 2012-04-11 19:15 - 00426184 ____A (Adobe Systems Incorporated) C:\Windows\SysWOW64\FlashPlayerApp.exe
2012-08-02 11:02 - 2011-06-18 06:50 - 00070344 ____A (Adobe Systems Incorporated) C:\Windows\SysWOW64\FlashPlayerCPLApp.cpl
2012-07-29 06:41 - 2008-11-07 10:01 - 00074240 ____A C:\Users\John\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
2012-07-12 11:53 - 2008-11-11 18:59 - 00087488 ____A (LogMeIn, Inc.) C:\Windows\System32\LMIRfsClientNP.dll
2012-07-12 11:53 - 2008-11-11 18:59 - 00080800 ____A (LogMeIn, Inc.) C:\Windows\System32\LMIinit.dll
2012-07-12 11:53 - 2008-11-11 18:59 - 00034720 ____A (LogMeIn, Inc.) C:\Windows\System32\LMIport.dll
2012-07-03 09:46 - 2012-08-06 19:02 - 00024904 ____A (Malwarebytes Corporation) C:\Windows\System32\Drivers\mbam.sys
2012-07-01 18:59 - 2012-07-01 18:59 - 00000888 ____A C:\Users\Public\Desktop\GoodSync Explorer.lnk
2012-07-01 18:59 - 2012-07-01 18:59 - 00000878 ____A C:\Users\Public\Desktop\GoodSync.lnk
2012-06-13 23:27 - 2006-11-02 07:21 - 00456976 ____A C:\Windows\System32\FNTCACHE.DAT
2012-06-13 23:04 - 2006-11-02 04:35 - 58957832 ____A (Microsoft Corporation) C:\Windows\System32\mrt.exe
2012-06-02 14:19 - 2012-06-19 00:14 - 02428952 ____A (Microsoft Corporation) C:\Windows\System32\wuaueng.dll
2012-06-02 14:19 - 2012-06-19 00:14 - 00701976 ____A (Microsoft Corporation) C:\Windows\System32\wuapi.dll
2012-06-02 14:19 - 2012-06-19 00:14 - 00577048 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wuapi.dll
2012-06-02 14:19 - 2012-06-19 00:14 - 00057880 ____A (Microsoft Corporation) C:\Windows\System32\wuauclt.exe
2012-06-02 14:19 - 2012-06-19 00:14 - 00044056 ____A (Microsoft Corporation) C:\Windows\System32\wups2.dll
2012-06-02 14:19 - 2012-06-19 00:14 - 00038424 ____A (Microsoft Corporation) C:\Windows\System32\wups.dll
2012-06-02 14:19 - 2012-06-19 00:14 - 00035864 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wups.dll
2012-06-02 14:15 - 2012-06-19 00:14 - 02622464 ____A (Microsoft Corporation) C:\Windows\System32\wucltux.dll
2012-06-02 14:15 - 2012-06-19 00:14 - 00099840 ____A (Microsoft Corporation) C:\Windows\System32\wudriver.dll
2012-06-02 14:12 - 2012-06-19 00:14 - 00088576 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wudriver.dll
2012-06-02 11:19 - 2012-06-19 00:14 - 00186752 ____A (Microsoft Corporation) C:\Windows\System32\wuwebv.dll
2012-06-02 11:19 - 2012-06-19 00:14 - 00171904 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wuwebv.dll
2012-06-02 11:15 - 2012-06-19 00:14 - 00036864 ____A (Microsoft Corporation) C:\Windows\System32\wuapp.exe
2012-06-02 11:12 - 2012-06-19 00:14 - 00033792 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wuapp.exe
2012-05-26 06:57 - 2012-05-26 06:57 - 00000904 ____A C:\Users\Public\Desktop\Flixster Collections.lnk
2012-05-21 07:24 - 2008-11-11 18:59 - 00087456 ____A (LogMeIn, Inc.) C:\Windows\System32\LMIRfsClientNP.dll.000.bak
2012-05-17 18:47 - 2012-06-13 23:08 - 17807360 ____A (Microsoft Corporation) C:\Windows\System32\mshtml.dll
2012-05-17 18:16 - 2012-06-13 23:08 - 10924032 ____A (Microsoft Corporation) C:\Windows\System32\ieframe.dll
2012-05-17 18:06 - 2012-06-13 23:08 - 02311680 ____A (Microsoft Corporation) C:\Windows\System32\jscript9.dll
2012-05-17 17:59 - 2012-06-13 23:08 - 01392128 ____A (Microsoft Corporation) C:\Windows\System32\wininet.dll
2012-05-17 17:59 - 2012-06-13 23:08 - 01346048 ____A (Microsoft Corporation) C:\Windows\System32\urlmon.dll
2012-05-17 17:58 - 2012-06-13 23:08 - 01494528 ____A (Microsoft Corporation) C:\Windows\System32\inetcpl.cpl
2012-05-17 17:58 - 2012-06-13 23:08 - 00237056 ____A (Microsoft Corporation) C:\Windows\System32\url.dll
2012-05-17 17:56 - 2012-06-13 23:08 - 00085504 ____A (Microsoft Corporation) C:\Windows\System32\jsproxy.dll
2012-05-17 17:55 - 2012-06-13 23:08 - 00818688 ____A (Microsoft Corporation) C:\Windows\System32\jscript.dll
2012-05-17 17:55 - 2012-06-13 23:08 - 00173056 ____A (Microsoft Corporation) C:\Windows\System32\ieUnatt.exe
2012-05-17 17:54 - 2012-06-13 23:08 - 02144768 ____A (Microsoft Corporation) C:\Windows\System32\iertutil.dll
2012-05-17 17:51 - 2012-06-13 23:08 - 02382848 ____A (Microsoft Corporation) C:\Windows\System32\mshtml.tlb
2012-05-17 17:51 - 2012-06-13 23:08 - 00096768 ____A (Microsoft Corporation) C:\Windows\System32\mshtmled.dll
2012-05-17 17:47 - 2012-06-13 23:08 - 00248320 ____A (Microsoft Corporation) C:\Windows\System32\ieui.dll
2012-05-17 15:11 - 2012-06-13 23:08 - 12314624 ____A (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.dll
2012-05-17 14:48 - 2012-06-13 23:08 - 09737728 ____A (Microsoft Corporation) C:\Windows\SysWOW64\ieframe.dll
2012-05-17 14:45 - 2012-06-13 23:08 - 01800192 ____A (Microsoft Corporation) C:\Windows\SysWOW64\jscript9.dll
2012-05-17 14:36 - 2012-06-13 23:08 - 01103872 ____A (Microsoft Corporation) C:\Windows\SysWOW64\urlmon.dll
2012-05-17 14:35 - 2012-06-13 23:08 - 01427968 ____A (Microsoft Corporation) C:\Windows\SysWOW64\inetcpl.cpl
2012-05-17 14:35 - 2012-06-13 23:08 - 01129472 ____A (Microsoft Corporation) C:\Windows\SysWOW64\wininet.dll
2012-05-17 14:33 - 2012-06-13 23:08 - 00231936 ____A (Microsoft Corporation) C:\Windows\SysWOW64\url.dll
2012-05-17 14:31 - 2012-06-13 23:08 - 00065024 ____A (Microsoft Corporation) C:\Windows\SysWOW64\jsproxy.dll
2012-05-17 14:29 - 2012-06-13 23:08 - 00716800 ____A (Microsoft Corporation) C:\Windows\SysWOW64\jscript.dll
2012-05-17 14:29 - 2012-06-13 23:08 - 00142848 ____A (Microsoft Corporation) C:\Windows\SysWOW64\ieUnatt.exe
2012-05-17 14:27 - 2012-06-13 23:08 - 01793024 ____A (Microsoft Corporation) C:\Windows\SysWOW64\iertutil.dll
2012-05-17 14:25 - 2012-06-13 23:08 - 00073216 ____A (Microsoft Corporation) C:\Windows\SysWOW64\mshtmled.dll
2012-05-17 14:24 - 2012-06-13 23:08 - 02382848 ____A (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.tlb
2012-05-17 14:20 - 2012-06-13 23:08 - 00176640 ____A (Microsoft Corporation) C:\Windows\SysWOW64\ieui.dll
2012-05-15 12:15 - 2012-06-13 04:19 - 02767360 ____A (Microsoft Corporation) C:\Windows\System32\win32k.sys
ZeroAccess:
C:\Windows\Installer\{4e253807-60b2-fed5-95a9-13e910f82962}
C:\Windows\Installer\{4e253807-60b2-fed5-95a9-13e910f82962}\@
C:\Windows\Installer\{4e253807-60b2-fed5-95a9-13e910f82962}\L
C:\Windows\Installer\{4e253807-60b2-fed5-95a9-13e910f82962}\U
C:\Windows\Installer\{4e253807-60b2-fed5-95a9-13e910f82962}\U\00000001.@
ZeroAccess:
C:\Users\John\AppData\Local\{4e253807-60b2-fed5-95a9-13e910f82962}
C:\Users\John\AppData\Local\{4e253807-60b2-fed5-95a9-13e910f82962}\@
C:\Users\John\AppData\Local\{4e253807-60b2-fed5-95a9-13e910f82962}\L
C:\Users\John\AppData\Local\{4e253807-60b2-fed5-95a9-13e910f82962}\U
========================= Known DLLs (Whitelisted) ============
========================= Bamital & volsnap Check ============
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\wininit.exe => MD5 is legit
C:\Windows\SysWOW64\wininit.exe => MD5 is legit
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\SysWOW64\explorer.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\SysWOW64\svchost.exe => MD5 is legit
C:\Windows\System32\services.exe => MD5 is legit
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\SysWOW64\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\SysWOW64\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
========================= Memory info ======================
Percentage of memory in use: 10%
Total physical RAM: 8191.18 MB
Available physical RAM: 7346.39 MB
Total Pagefile: 8189.33 MB
Available Pagefile: 7349.91 MB
Total Virtual: 8192 MB
Available Virtual: 8191.9 MB
======================= Partitions =========================
1 Drive c: (OS) (Fixed) (Total:58.59 GB) (Free:10.63 GB) NTFS ==>[System with boot components (obtained from reading drive)]
2 Drive d: () (Fixed) (Total:111.79 GB) (Free:67.11 GB) NTFS
3 Drive f: (Media_Local) (Fixed) (Total:1849.01 GB) (Free:141.93 GB) NTFS
4 Drive g: (Programs) (Fixed) (Total:34.18 GB) (Free:23.2 GB) NTFS
5 Drive h: (John_Active) (Fixed) (Total:78.12 GB) (Free:27.71 GB) NTFS
6 Drive I: (RECOVERY) (Fixed) (Total:15 GB) (Free:8 GB) NTFS
7 Drive j: (GRMCHPXFRER_EN_DVD) (CDROM) (Total:3 GB) (Free:0 GB) UDF
8 Drive k: () (Removable) (Total:14.9 GB) (Free:14.89 GB) FAT32
9 Drive x: (Boot) (Fixed) (Total:0.03 GB) (Free:0.03 GB) NTFS
10 Drive y: (Page_File2) (Fixed) (Total:14 GB) (Free:13.91 GB) NTFS
Disk ### Status Size Free Dyn Gpt
-------- ------------- ------- ------- --- ---
Disk 0 Online 1863 GB 1024 KB
Disk 1 Online 111 GB 0 B
Disk 2 Online 698 GB 512 GB
Disk 3 Online 14 GB 0 B
Partitions of Disk 0:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 14 GB 31 KB
Partition 0 Extended 1849 GB 14 GB
Partition 2 Logical 1849 GB 14 GB
==================================================================================
Disk: 0
Partition 1
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 1 Y Page_File2 NTFS Partition 14 GB Healthy
==================================================================================
Disk: 0
Partition 2
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 2 F Media_Local NTFS Partition 1849 GB Healthy
==================================================================================
Partitions of Disk 1:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 111 GB 1024 KB
==================================================================================
Disk: 1
Partition 1
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 3 D NTFS Partition 111 GB Healthy
==================================================================================
Partitions of Disk 2:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 OEM 62 MB 31 KB
Partition 2 Primary 15 GB 63 MB
Partition 3 Primary 58 GB 15 GB
Partition 0 Extended 624 GB 73 GB
Partition 4 Logical 34 GB 73 GB
Partition 5 Logical 78 GB 107 GB
==================================================================================
Disk: 2
Partition 1
Type : DE
Hidden: Yes
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 9 FAT Partition 62 MB Healthy Hidden
==================================================================================
Disk: 2
Partition 2
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 4 I RECOVERY NTFS Partition 15 GB Healthy
==================================================================================
Disk: 2
Partition 3
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 5 C OS NTFS Partition 58 GB Healthy
==================================================================================
Disk: 2
Partition 4
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 6 G Programs NTFS Partition 34 GB Healthy
==================================================================================
Disk: 2
Partition 5
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 7 H John_Active NTFS Partition 78 GB Healthy
==================================================================================
Partitions of Disk 3:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 14 GB 16 KB
==================================================================================
Disk: 3
Partition 1
Type : 0C
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 8 K FAT32 Removable 14 GB Healthy
==================================================================================
==========================================================
Last Boot: 2012-08-07 16:47
======================= End Of Log ==========================