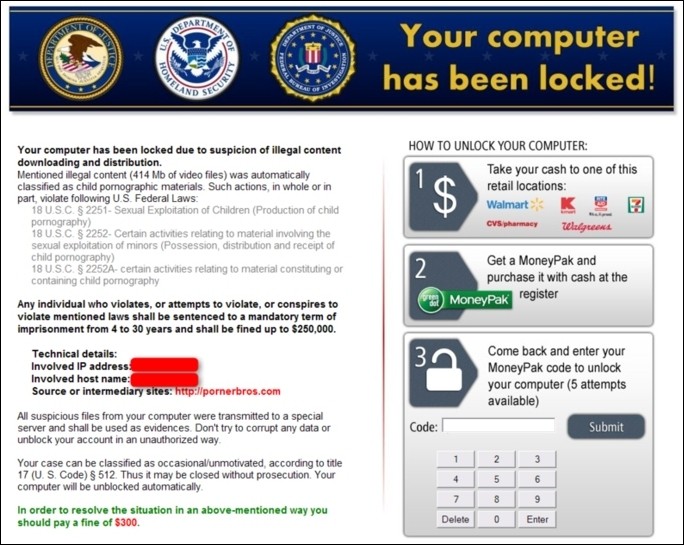
Ransomware is something you’ll hopefully never have to deal with but should your system somehow become infected, there’s now a new tool that may be able to unlock it without having to fork over any money.
For those unfamiliar, Ransomware is the general term given to a category of malware that prevents users from accessing certain types of files on their computer. Some instances even lock down the entire PC, using scare tactics (and pure frustration) to convince users to hand over money to have their system files unlocked.
The Dutch police’s National High Tech Crime Unit (NHTCU) recently happened upon a database of decryption keys on a CoinVault server. CoinVault is a piece of ransomware for Windows systems that has been circulating among nefarious hackers since last November.
The team commissioned Kaspersky Labs to build a decryption tool based on these keys that attempts to unlock ransomware-laden PCs. Given the nature of the tool and the limited decryption keys, this solution obviously won’t work for everyone but there’s no reason not to give it a try.
As authorities continue their investigation into the CoinVault ransomware, it’s possible that they could unearth even more decryption keys that could be added to Kaspersky’s tool.
As for the investigation itself, Dutch police haven’t arrested any suspects yet. That could happen soon, however, as authorities believe the individual(s) behind the CoinVault ransomware may be living in the Netherlands.
Thumbnail via ITPortal
https://www.techspot.com/news/60359-kaspersky-new-decryption-tool-can-unlock-select-ransomware.html