
Becoming infected with ransomware is often considered a death sentence. In most cases, you’re either forced to reformat and start fresh, reformat and load a backup or pay the ransom to get your data back like Hollywood Presbyterian Medical Center did back in February.
Last month, we learned of a new ransomware variant called Petya. What’s unique about Petya is the fact that it overwrites a hard drive’s master boot record (MBR) and destroys the file system. It was originally thought that the ransomware encrypted the entire hard drive but that’s not actually the case.
Nevertheless, Twitter user @leostone has managed to crack the ransomware. It’s not all that easy for novice computer users to pull off but it is possible.
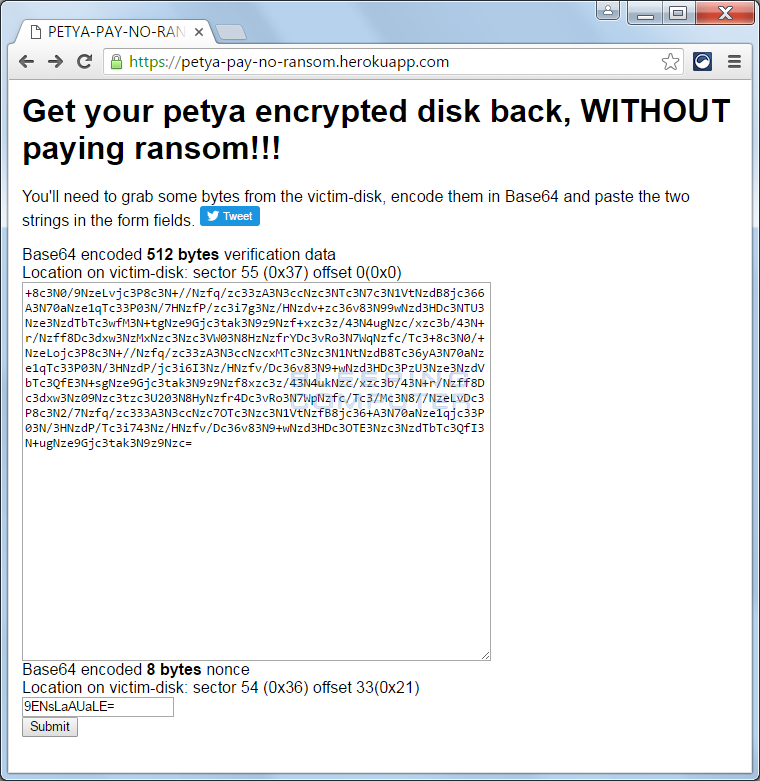
As Bleeping Computer highlights, you’ll need to remove the infected hard drive from the computer in question to extract specific data from it. The data needed is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the cracking site (mirrored here if the main site is down) to generate a decryption key.
Fortunately, there’s a relatively simply way of gathering the necessary data as another Twitter user, @fwosar, has created a tool to easily extract everything that’s needed although it still requires removing the hard drive and connecting it to a working Windows PC. This can either be done by connecting the infected drive internally or using an external hard drive dock like the Thermaltake BlacX (my go-to drive dock).
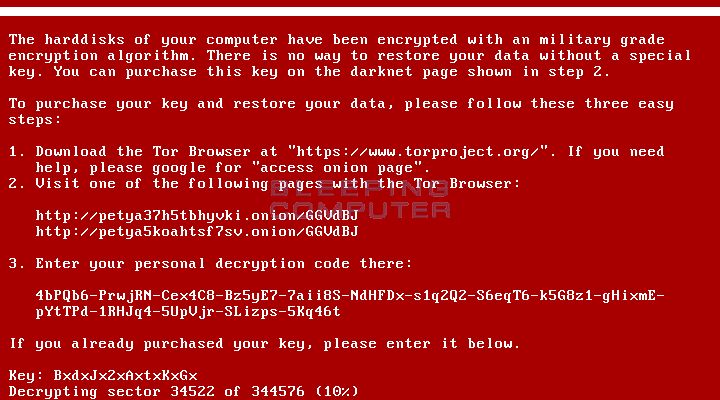
With the data from the tool in hand, simply enter it on @leostone’s site to generate a decryption key, take that key and enter it into the ransom page and boom, you’re good to go.
Bleeping Computer was able to verify the method works, generating a decryption key in just seven seconds. It’s a bit of a hassle but if you don’t have a master backup, it’s probably your best bet to regain access to your data.
https://www.techspot.com/news/64415-petya-ransomware-cracked-here-how-get-data-back.html