
During a recent hacker conference, forensic scientist and iPhone jailbreaking expert Jonathan Zdziarski outlined a number of undocumented high-value forensic services running on every iOS device. He also found suspicious design omissions in iOS that make data collection easier according to a report from ZDNet.
Zdziarski notes that while Apple has worked hard to make iOS devices reasonably secure against typical attackers, they've also put a lot of time and planning into making devices accessible on their end on behalf of law enforcement.

The hacker also found that screen-locking an iPhone doesn't encrypt its data. The only real way to do this is to shut down / power off the handset. What's more, some of the undocumented services are able to bypass backups and can be accessed using USB, Wi-Fi or perhaps even cellular.
Using commercially available forensics tools, for example, law enforcement could gain access to a device during a routine traffic stop or during an arrest before a suspect is able to power the phone off.
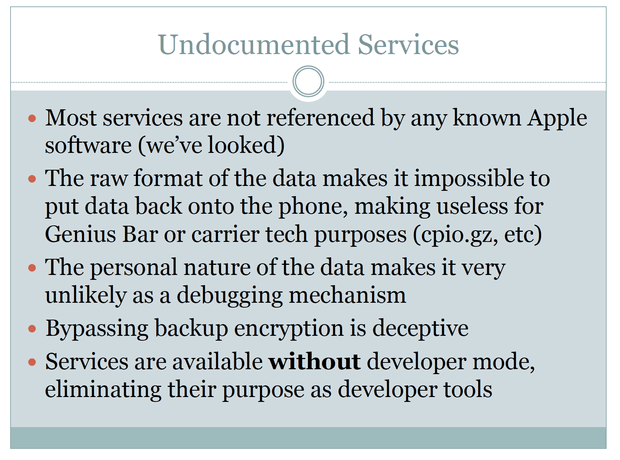
Zdziarski finds it suspicious that none of these services ("lockdownd," "pcapd" or "mobile.file_relay") are referenced in any Apple software. The data they collect is personal in nature thus unlikely to be used for debugging purposes and is stored in raw format to make it useless to wireless carriers or during a trip to a Genius Bar.
All said and done, Zdziarski is left with more questions than answers.