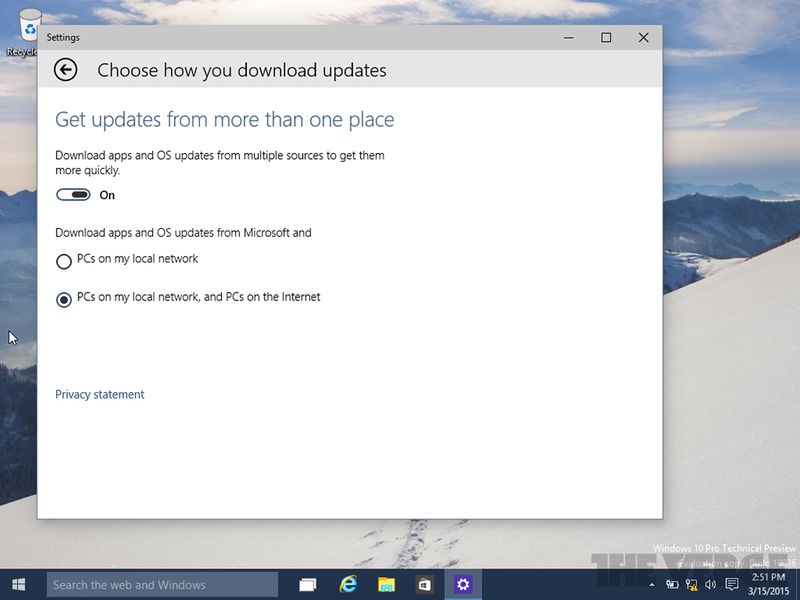
Microsoft is planning to revamp their update delivery method in Windows 10 by implementing peer-to-peer (P2P) technology. Traditionally Windows updates have been delivered through Microsoft's servers only, but by switching to P2P, the load on their servers can be decreased while simultaneously increasing download speeds.
The latest leaked build of Windows 10, build 10036, allows users to download updates from "multiple sources to get them more quickly". When this option is selected, updates will be downloaded in part from Microsoft's servers, as well as from PCs on your local network, and even PCs from the internet in general.
It's not clear exactly what type of P2P technology Microsoft has implemented, but it could be a variant of Pando Networks' P2P tech that shares similarities with BitTorrent. Microsoft acquired Pando Networks in 2013, so it makes sense that the company would use their technology.
This P2P update method is expected to be available to Windows 10 testers in the next preview build, which should become available shortly. How fast updates can be delivered through P2P versus a single server remains to be seen.
In the next preview build, we can also expect a range of other features leaked in build 10036, including UI changes that span the Start menu, wireless connectivity, and system-wide icons.
https://www.techspot.com/news/60061-windows-10-updates-delivered-using-p2p-technology.html