Back in June, security researchers from the Georgia Institute of Technology announced they were able install malware on an iOS device by plugging it into a custom-built charger. The charger itself will indeed replenish a phone's battery, but given it's built around a tiny Linux computer, which Apple devices will recognize it as a USB host, and as long as a victim's iPhone is unlocked (even for a second) it can receive a range of commands.
Demonstrating the attack at the Black Hat hacking convention this week, the trio showed a malicious Facebook app that replaced the original with a Trojan-infected version, which is then able to do things like taking screenshots whenever passwords are being entered or simulate key presses to dial phone numbers without any user intervention.
Ars Technica has more details on how the hack works and its limits if you are interested.
The group of researchers say real world criminals could use this as a spying tool. The chargers cost about $45 to buy and a week to design, and though it's not going to fit into a standard sized Apple charging unit, it could easily be installed into a docking station or external battery pack to trick unsuspecting iPhone or iPad owners.
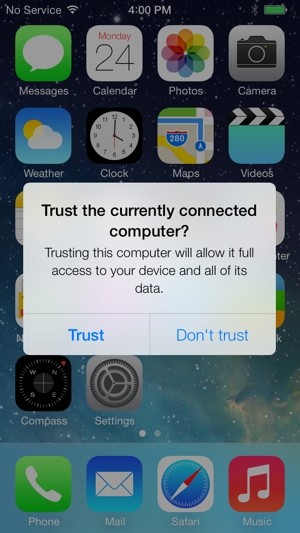
Apple has since responded to the threat by announcing a fix is coming to iOS 7. Starting with the latest beta out to developers, instead of trusting any USB host, iOS 7 will alert the user when they are connecting to a computer, not an ordinary charger, and ask them to manually grant or deny access to their iDevice.
The researchers also pointed out that devices running Google's Android operating system are not vulnerable to the same types of attack because they already warn users if they plug their phone or tablet into a computer.