NSA whistleblower Edward Snowden has released classified documents that reveal the government agency, along with its British counterpart GCHQ, have had little success in trying to crack the Tor anonymizing protocol. It's all a bit ironic when you consider Tor software is partially funded and promoted by the US government itself.
One of the documents titled "Tor Stinks" says they will never be able de-anonymize all Tor users all the time. With manual analysis, however, they can de-anonymize a small fraction of users but they aren't able to de-anonymize a specific user in response to a specific request.
Despite the fact that the NSA hasn't been able to crack Tor, they have had a little bit of success in de-anonymizing a very small fraction of Tor users by first identifying them then attacking vulnerable software on their computers.
One such method used a vulnerability in the Firefox browser used with Tor according to the NSA documents. This allowed the agency to gain full control over a target computer with access to files, keystrokes and all online activity.
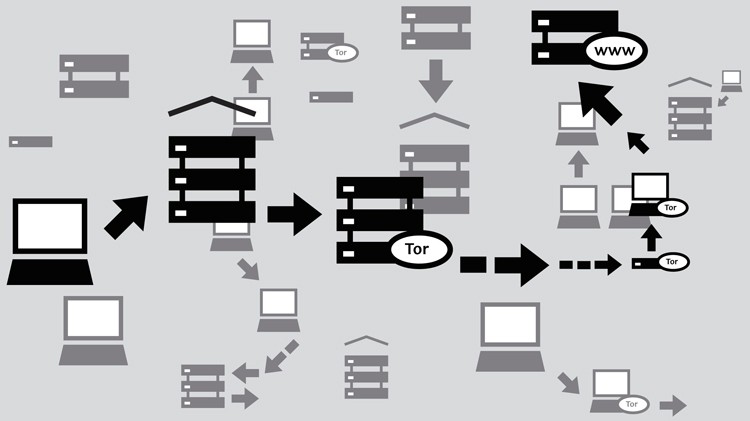
If you aren't familiar, Tor - short for The Onion Router - is an open-source network of sorts that routers users' Internet traffic through multiple computers to avoid censorship tools and guarantee anonymous Internet usage. It is used by a number of journalists, campaigners and activists but law enforcement officials also say it is utilized by those engaging in terrorism as well as people interested in child porn and online drug dealing.