Update: Dell has been quick to react after yesterday's news that a certificate (eDellRoot), installed along Dell's Foundation Services application used in many of their PCs, unintentionally introduced a security vulnerability. The certificate was intended to provide the system service tag to Dell online support to quickly identify the computer model, making it easier to provide tech support service.
An automated removal tool has been made available for download, along with some quick instructions.
Dell assures the public that the certificate was never used or intended to collect personal customer information. Also, that once removed the certificate will not reinstall itself. Finally, a software update has been pushed today to Dell PCs which will check for the certificate and remove it if detected.
Nicely done, Dell.
Dell appears to have a security blunder on its hands not all that different from the Superfish fiasco that plagued Lenovo earlier this year.
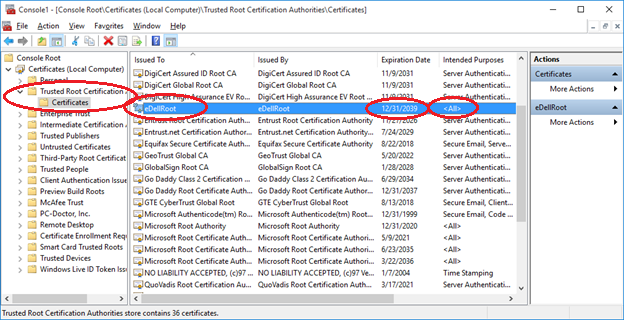
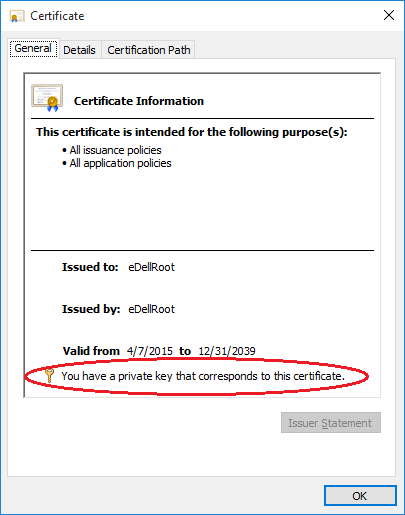
Programmer Joe Nord penned a blog post over the weekend in which he outlines finding a trusted root certificate pre-installed on his new Dell Inspiron 5000 series notebook. Named "eDellRoot," the self-signing certificate is intended for "all" purposes and has an expiration date of 2039. Worse yet, after a little more digging, Nord found that the private key to the certificate was stored locally.
The eDellRoot key has since been found on several other Dell models including the XPS 13 and XPS 15.
As The Register notes, an attacker could set up a malicious Wi-Fi hotspot, intercept connections from Dell computers and easily strip away the encryption. The result would be unabated access to usernames, passwords, session cookies and other sensitive information. Attackers could even use it to sign programs, thus dressing up malware as legitimate programs.
Dell's social media global support team over on Twitter (@DellCares) attempted to downplay the issue over the weekend by saying it doesn't cause any threat to systems. That post appears to have since been pulled from Dell's feed.
In a statement issued to multiple publications, Dell said customer security and privacy are a top concern and that they have a strict policy of minimizing the number of pre-load applications and assessing all applications for their security and usability. The PC maker added that it has a team investigating the current situation and will provide an update as soon as they have more information.
The issue is ongoing although the chief concern is, why does eDellRoot even exist? Is Dell responsible for its inclusion? If Dell is responsible, it shows incredibly poor judgment considering Lenovo's incident earlier this year.