Although a man recently made headlines for demonstrating that he could brute force an eight-character Windows password in less than six hours by harnessing the power of 25 GPUs, another savvy user has reminded us of a workaround that can bypass the security of virtually any Windows account in 10 minutes.
The trick has been around for years and involves replacing the login screen's Ease of Access Center software with a command prompt. To pull it off, all you need is a bootable System Recovery media or a bootable Windows 8 installation media (Jamal Naji offers instructions on both approaches, though little changes).
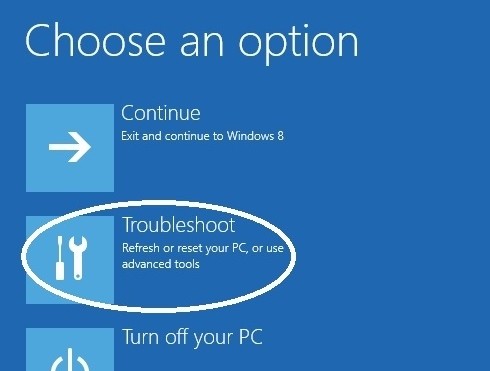
Once you've loaded into the System Recovery environment, you need to access the command prompt to get started. From there, you need to identify your Windows volume with DiskPart, navigate to the Windows\System32 directory, then delete utiliman.exe and rename cmd.exe as that file (backup both apps first).
After that's done, you can reboot and when you get to the Windows login screen, the Ease of Access Center icon should launch a command prompt. Now you can enter net user to get a list of Windows accounts, then net user USERNAME * to initiate a reset, which requires you to enter and confirm the new password.
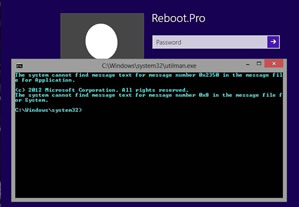
Naji notes that you'll probably want to reverse the changes you've made after the password is reset, which basically involves undoing the steps in paragraph three so utiliman.exe is restored. He offers a detailed breakdown of the entire procedure for Windows 8 if you need it, as well as specific instructions for Windows 7.