I guess at some point most of us just assume that people are siphoning off huge amounts of important data through the internet for nefarious purposes, and based on a report from Wired it appears as though something just like that has recently been uncovered.
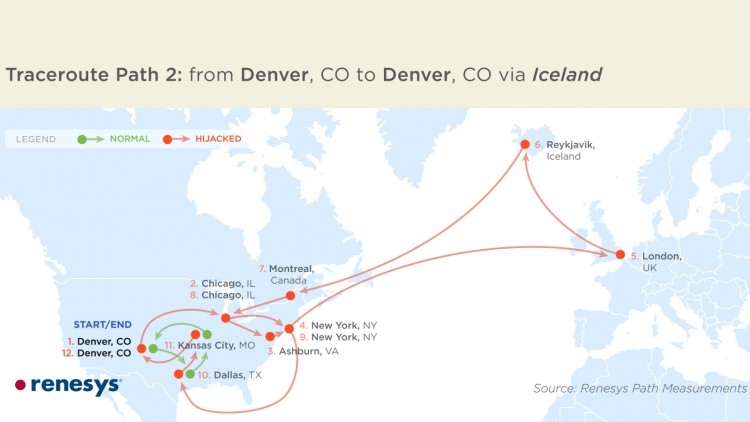
Supposedly in operation for quite some time unnoticed, someone is copying and redirecting massive amounts of important internet data traffic headed for American government agencies, corporations and others. As you can see in the image above the culprits are pulling data stateside and then siphoning it off and bouncing it around the globe, again very much like most of us would imagine it happens.
Wired says that, "The stakes are potentially enormous, since once data is hijacked, the perpetrator can copy and then comb through any unencrypted data freely --- reading email and spreadsheets, extracting credit card numbers, and capturing vast amounts of sensitive information." The publication went on to say that researchers suggest that those responsible for the cyber attacks initiated these kinds of bulk data grabs about 38 times from across 1500 different IP blocks. Sometimes the attackers would leech on for minutes and sometimes for as long as days. Another key point researchers are driving home is that these attacks could not have been a mistake of any kind.
It is unclear at this point why the attacks took place and what can be done about preventing them in the future. It looks as though most of the stolen data was headed for large financial institutes, which would initially make sense, but then data showed up that appeared to be heading to the foreign ministry and a "large VoIP provider in the U.S."
At this point, the large convoluted network the data is passing through, combined with what sounds like a very possible course of events, has made it quite difficult to figure out who is behind the attacks. Wired explains:
Tony Kapela [one of the researchers who discovered the breach] says the culprit... could actually be an outsider who simply seizes control of one of the systems and sends out the bogus announcement without the owner of the system knowing it. He imagines a scenario where an attacker gains physical access to a router belonging to one of the companies and installs a monitoring device to record data, then gains control of the router console to send out a bogus BGP announcement to redirect traffic through the router. If anyone discovers the redirect, the culprit would appear to be the company that owned the route