Bottom line: A misconfigured server recently exposed personal information from what is estimated to be north of 100,000 Razer customers. Just because no sensitive information was exposed doesn't mean it couldn't be damaging. Spammers use sources like this all the time to build up-to-date databases for spam and phishing campaigns.
Independent security researcher Volodymyr "Bob" Diachenko was the first to report on the matter. Diachenko said he immediately reached out to Razer's support channel but his message never found the right people inside the company. Instead, he said it was processed by non-tech support managers for more than three weeks before being resolved.
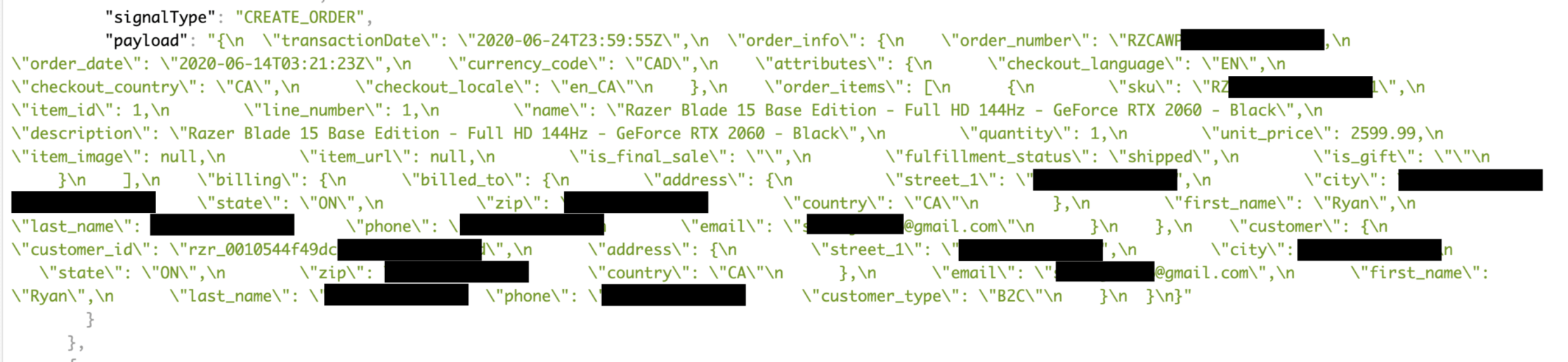
Exposed data reportedly included full names, e-mail addresses, phone numbers, order numbers and customer ID numbers as well as shipping and billing addresses. Diachenko said it was part of a large log chunk stored on an Elasticsearch cluster that had been misconfigured since August 18. Worse yet, it was being indexed by public search engines.
Razer in a statement to Diachenko noted that the misconfigured server was fixed on September 9, adding that sensitive data such as passwords or payment card numbers were not exposed.
The Verge said Razer confirmed the issue via e-mail, adding that anyone with concerns could reach out to customer support for more information.
Masthead credit: Sharaf Maksumov
