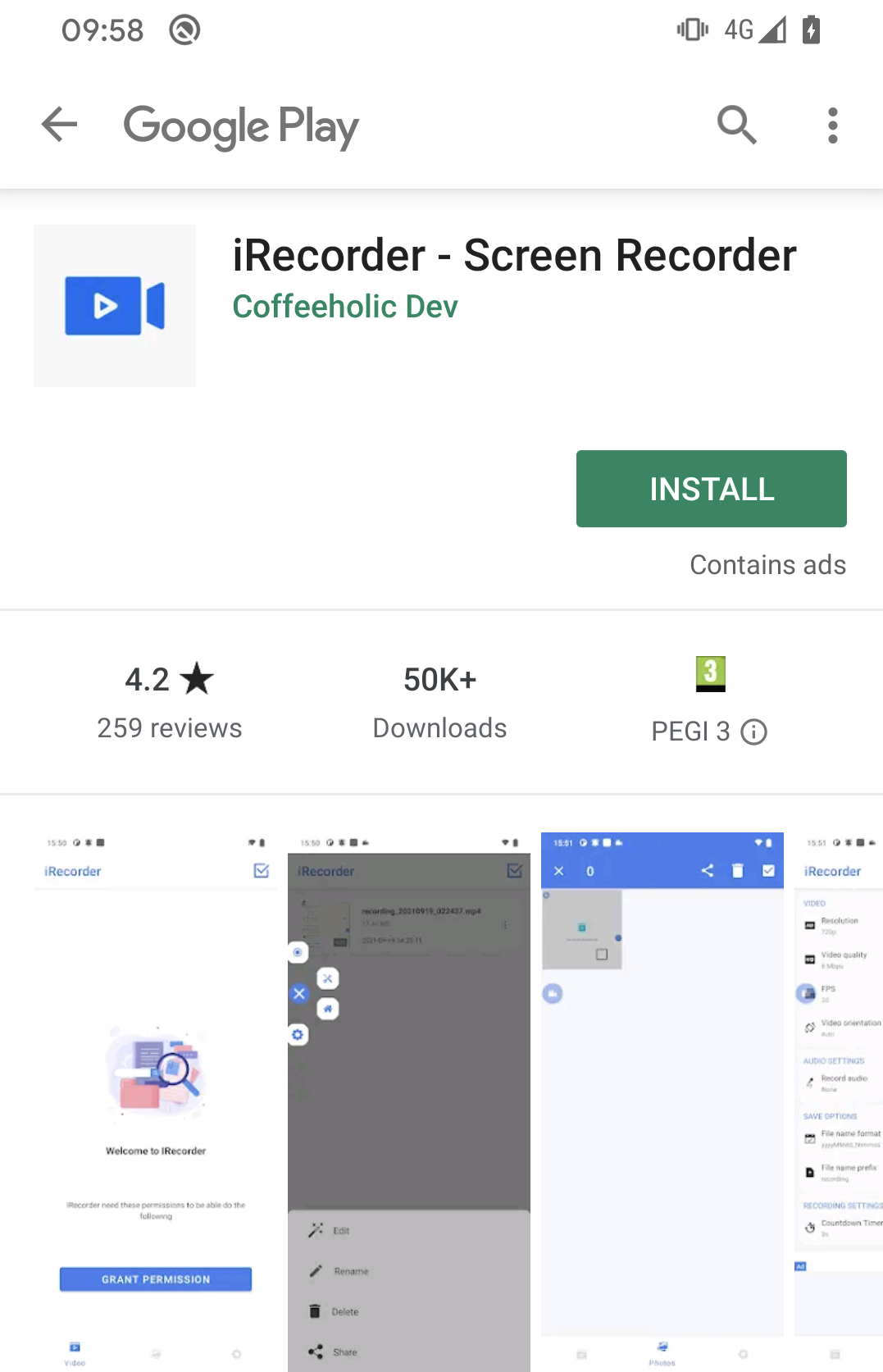
In brief: One effective way that a malicious Android app on the Play Store can avoid Google's detections is to arrive as a clean, legitimate program before the malware elements are implemented at a later date. That's what happened with iRecorder - Screen Recorder. The app, which was downloaded 50,000 times, was secretly making audio recordings with a device mic every 15 minutes and sending them to an attacker.
ESET researcher Lukas Stefanko discovered that iRecorder - Screen Recorder had become trojanized over the last year. The app first arrived on Google Play in September 2021, when it was free from any malicious elements, but that changed when the version 1.3.8 update came in August 2022.
The malicious code added to the app is based on the open-source AhMyth Android RAT (remote access trojan) malware that is able to steal data from devices, including contacts, SMS messages, call logs, browser histories, device location, and screenshots. But the developer's customized version, which ESET named AhRat, had limited functionality.
The insidious aspect of AhRat is its ability to record surrounding audio from the device's microphone every 15 minutes and upload it to the attacker's command and control (C&C) server.
Only six of the app's 18 capabilities had been implemented, suggesting AhRat was a work in progress that could have had some of the extra functionality found in AhMyth, such as keylogging, location tracking, and screen capturing, added at a later date.
Not only had the app been downloaded over 50,000 times, but it had a respectable 4.2-star rating on Google Play, likely a result of it being safe for so long. A low score with plenty of user criticism is often a red flag.
Being able to record and send audio at short intervals is an unusual trait. Stefanko suggests it could be part of an espionage campaign, especially as the open-source AhMyth had previously been used by Transparent Tribe, an espionage group known for targeting government and military organizations in South Asia. However, there is no evidence that AhRat is linked to that group, nor is it clear if the app was designed to eavesdrop on a specific group of people.
Coffeeholic Dev, the app's developer, did have other apps on the store that showed no signs of malware, but those elements could have been added at some point in the future, as was the case with iRecorder - Screen Recorder. We won't get to find out as all of their apps have now been removed by Google.