Update: Skype has posted an update on its blog saying that the vulnerability has now been fixed and that it is reaching out to "a small number of users" who may have been impacted to assist as necessary – original story below.
Reports have emerged about a security hole in Skype's password recovery mechanism that allowed any account to be hijacked knowing only the username and email address. The Next Web first reported the issue and was able to reproduce the attack following step-by-step instructions posted on a Russian forum two months ago.
The whole process is so straightforward that it's surprising how the company could have missed such a glaring security hole within its system. Apparently, it's possible to create a new Skype account with an email address that's already in use by another person, effectively associating a single email to two different users.
From there an attacker can request a password reset for the targeted account and a token will be sent to the associated email address, which normally wouldn't be a problem but surprisingly it is also displayed on the Skype interface. Armed with that token it is possible to reset the password for the original and the dummy account, since both are associated to the same email and Skype will simply ask which one you want reset.
The Next Web says that the flaw had been previously reported to Microsoft but it wasn't until it became public that they decided to take action. Skype has since pulled its password reset page as it investigates the problem. Below is a short statement posted this morning on the Skype blog:
We have had reports of a new security vulnerability issue. As a precautionary step we have temporarily disabled password reset as we continue to investigate the issue further. We apologize for the inconvenience but user experience and safety is our first priority.
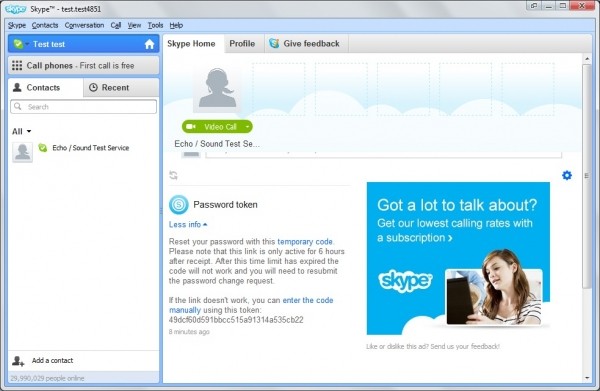
Image via Ghacks
