PSA: Asustor NAS owners are being warned about a nasty ransomware, DeadBolt, that's attacking cloud-connected/online NAS and asking for 0.03 BTC to decrypt users’ content. If you’re running an Asustor device, you’ll want to disable the EZ Connect utility suspected of being vulnerable to the exploit and physically disconnect your NAS from the internet.

The DeadBolt ransomware, which has previously taken QNAP drives hostage, is now after Asustor devices and is encrypting files on internet-connected instances. NAS Compares reports how multiple owners have been affected by DeadBolt while the ransomware’s attack vector remains unknown.
The Asustor community forum is also populated with similar experiences, with users reporting high disk activity triggered by DeadBolt encrypting their files. Reddit user u/kabe0, who also fell victim to this attack, shared how other owners can detect the presence of this ransomware by logging into their NAS and searching for all files with the .deadbolt extension by typing this command:
sudo find / -type f -name "*.deadbolt"
Compromised NAS drives will also fail to function properly as DeadBolt is targeting both system and personal files. For affected users, the recommended course of action is to salvage unencrypted content and assess damage by plugging their NAS into another Linux instance and taking an external backup.
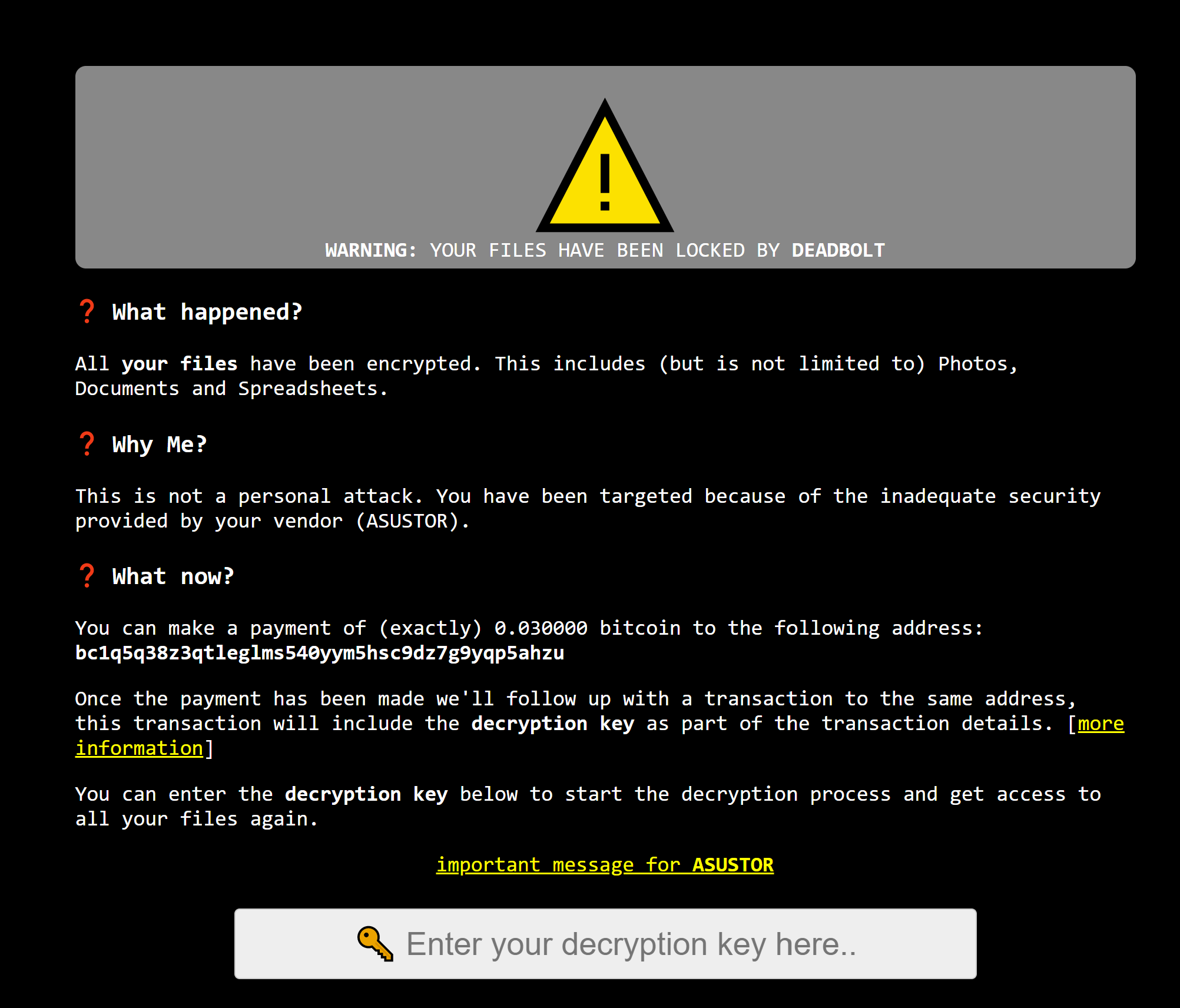
Unaffected owners, meanwhile, have been asked to disable Asustor’s EZ Connect remote access software, prevent unauthorized access by disabling SSH, turn off auto updates and configure their firewall to only allow LAN communication and block all incoming traffic from outside.
The latest attack serves as yet another reminder of the importance of offline backups and the risk that comes with the convenience of having your personal storage remotely accessible. Although not a victim of ransomware, some internet-connected WD drives caused similar headaches last year due to malicious software causing them to wipe all data and factory reset.
Asustor is yet to issue an advisory or respond with its own investigation of this attack to reveal details around the possible vulnerability, an upcoming software fix and/or a complete list of affected models.
https://www.techspot.com/news/93497-asustor-nas-reportedly-under-ransomware-attack-owners-asked.html