Dieter Holger
Posts: 39 +1

Hackers are uploading thousands of YouTube videos that show how to break into webcams with easily accessible software, says a report from Digital Citizen's Alliance. Despite these hacking tactics being illegal, 38 percent of the YouTube tutorials are approved for ads that bring in cash for the hackers and Google.
The videos -- which can be as short as 7-minutes -- demonstrate how to use "ratter" hacking programs, known formally as remote administrative software (RAT). Downloads to RAT software are linked in the description or video of the hacking tutorials. RAT software can be as cheap as $10, making it easy for the average Joe to become a hacker.
Some of the hacking video tutorials only go through the necessary steps, while others shamelessly include clips of female victims. One video shows a young woman in front of her webcam in pajamas, another shows a teenage girl yelling, "Mom, I think that camera is picking up creepy stuff. I think somebody hacked that camera!"
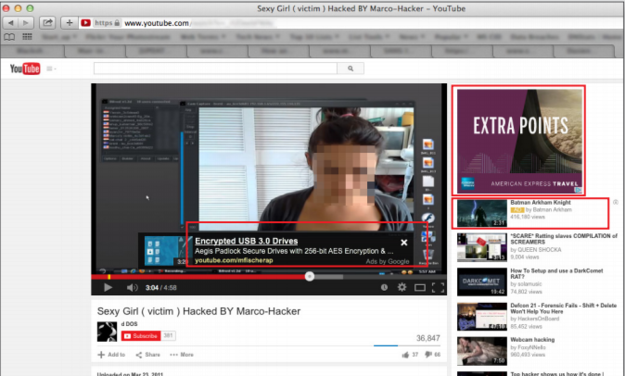
The same research from Digital Citizen's Alliance estimates you can sell access to a female's computer for $5, five times more than a male's.
According to YouTube's advertising guidelines every video must be approved to run ads, however the report details that four out of ten hacking tutorials feature Google AdSense, raising alarming concerns about YouTube's vetting process. The YouTube ads included common Google sponsors like American Express, The Wall Street Journal, Acura and even Batman: Arkham Knight.
TechSpot has reached out to YouTube and Google for comment, we'll update the post with their response.
https://www.techspot.com/news/61588-hackers-uploading-illegal-youtube-how-tos-approved-google.html