In context: Since the first computer virus, malware has been a cat-and-mouse game between hackers and security researchers. It's to the point where most malware is known, at least in type and delivery method. However, bad actors occasionally conceive a new trick to hide their footprints and fool the white hats.

Security analytics firm Mandiant recently uncovered a "never-before-seen" attack chain that used Base 64 encoding on at least two different websites to deliver the second-stage payload of a three-stage malware. The two sites were tech publication Ars Technica and video hosting site Vimeo.
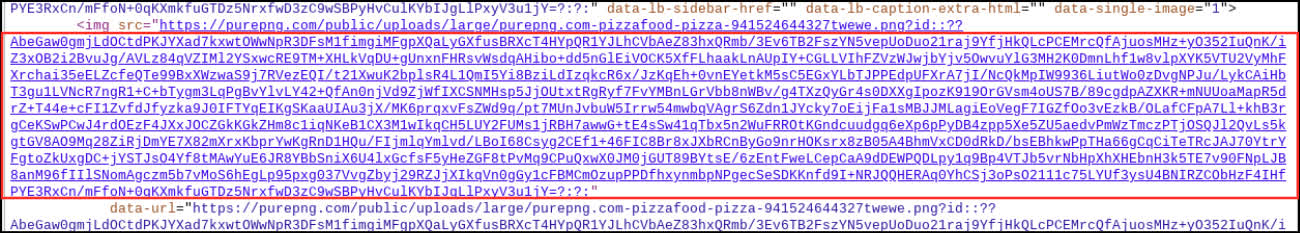
A user posted a picture of a pizza on the Ars Technica forum with the caption, "I like pizza." There was nothing inherently wrong with the image or text. However, the photo, hosted on a third-party website, had a URL containing with a Base 64 string. Base 64 converted to ASCII looks like random characters, but in this case, it obfuscated binary instructions to download and install the second stage of a malware package. In another instance, an identical string appeared in the description of an otherwise harmless video on Vimeo.
An Ars Technica spokesperson said it removed the account – created last November – after an anonymous user tipped off the website about the strange link for the image (below).
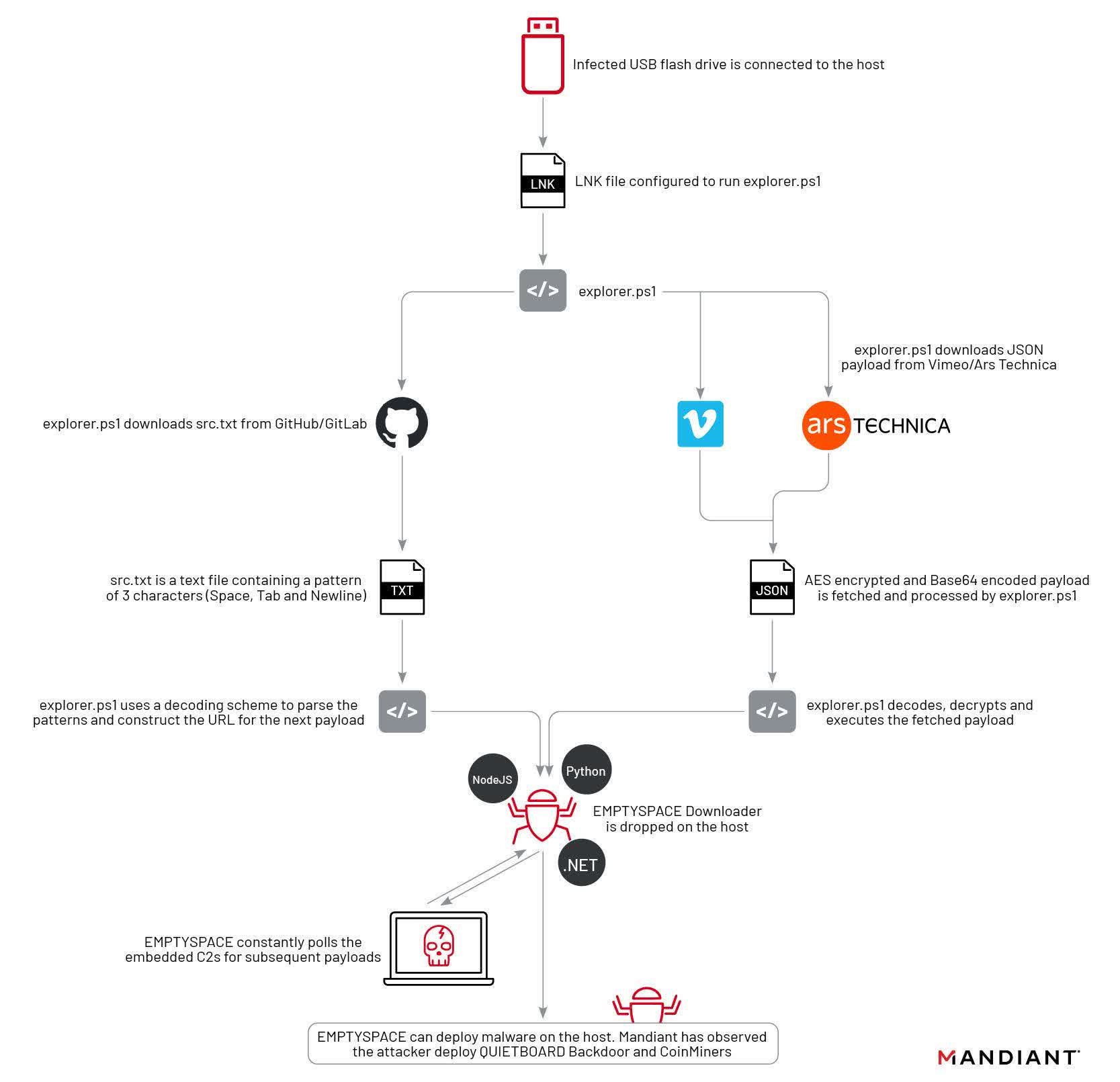
Mandiant said it identified the code as belonging to a threat actor named UNC4990, which it has tracked since 2020. For most users, the instructions had no effect. It only operates on devices that already contain the first stage of the malware (explorer.ps1). UNC4990 distributed stage one through infected flash drives configured to link to the file hosted on GitHub and GitLab.
The second stage, dubbed "Emptyspace," is a text file that appears blank to browsers and text editors. However, opening it with a hex editor reveals a binary file that uses a clever encoding scheme of spaces, tabs, and new lines to create executable binary code. Mandiant admits it has never seen this technique used before.
"This is a different and novel way we're seeing abuse that can be pretty hard to detect," Mandiant researcher Yash Gupta said told Ars. "This is something in malware we have not typically seen. It's pretty interesting for us and something we wanted to call out."
Upon execution, Emptyspace continuously polls a command and control server and downloads a backdoor dubbed "Quietboard" on command. UNC4990 uses the backdoor to install cryptocurrency miners on the infected machines. However, Mandiant says it has only tracked a single instance of a Quietboard installation.
Given the rarity of Quietboard, UNC4990's attack poses a minimal threat. However, explorer.ps1 and Emptyspace instances could be much higher, leaving users vulnerable. Mandiant explains how to detect the infection in its blog.
https://www.techspot.com/news/101713-hackers-used-ars-technica-vimeo-deliver-malware-using.html