What just happened? Months after researchers discovered the dangerous, "invisible" threat posed by BlackLotus, Microsoft is now giving investigators and sysadmins a detailed guidance over the telltale signs of an ongoing infection.
BlackLotus is an all-powerful UEFI bootkit recently discovered "in the wild," a security threat equipped with very advanced capabilities and designed to turn itself into an invisible ghost within a fully updated Windows machine. Even though the infection is effectively transparent to normal usage, researchers and analysts have now enough knowledge about the system changes brought by the malware.
Microsoft has put together a guidance for investigating (and, of course, detecting) the BlackLotus campaign, which is first designed to exploit the CVE-2022-21894 security flaw ("Secure Boot Security Feature Bypass Vulnerability") fixed by Redmond in January 2022. UEFI bootkits are particularly dangerous as they run at computer startup before the operating system is loaded, Microsoft explains, therefore they can interfere with or deactivate various OS security mechanisms.
According to Microsoft's guide, researchers and administrators must search specific (hidden) parts of a Windows installation to identify the clues of a BlackLotus infection. The telltale signs of the bootkit presence include recently created and locked boot files, a staging directory used during the BlackLotus installation, Registry key changes to disable the Hypervisor-protected Code Integrity (HVCI) feature, and network and boot logs.
To investigate the potential modifications to the boot process, Microsoft says, "threat hunters" first need to mount the EFI system partition that is usually hidden from everyday Windows use. Then they have to check the modification date of the EFI files protected by the BlackLotus kernel driver, searching for mismatches between earlier and the most recent files. The recent ones would likely be associated with the bootkit infection.
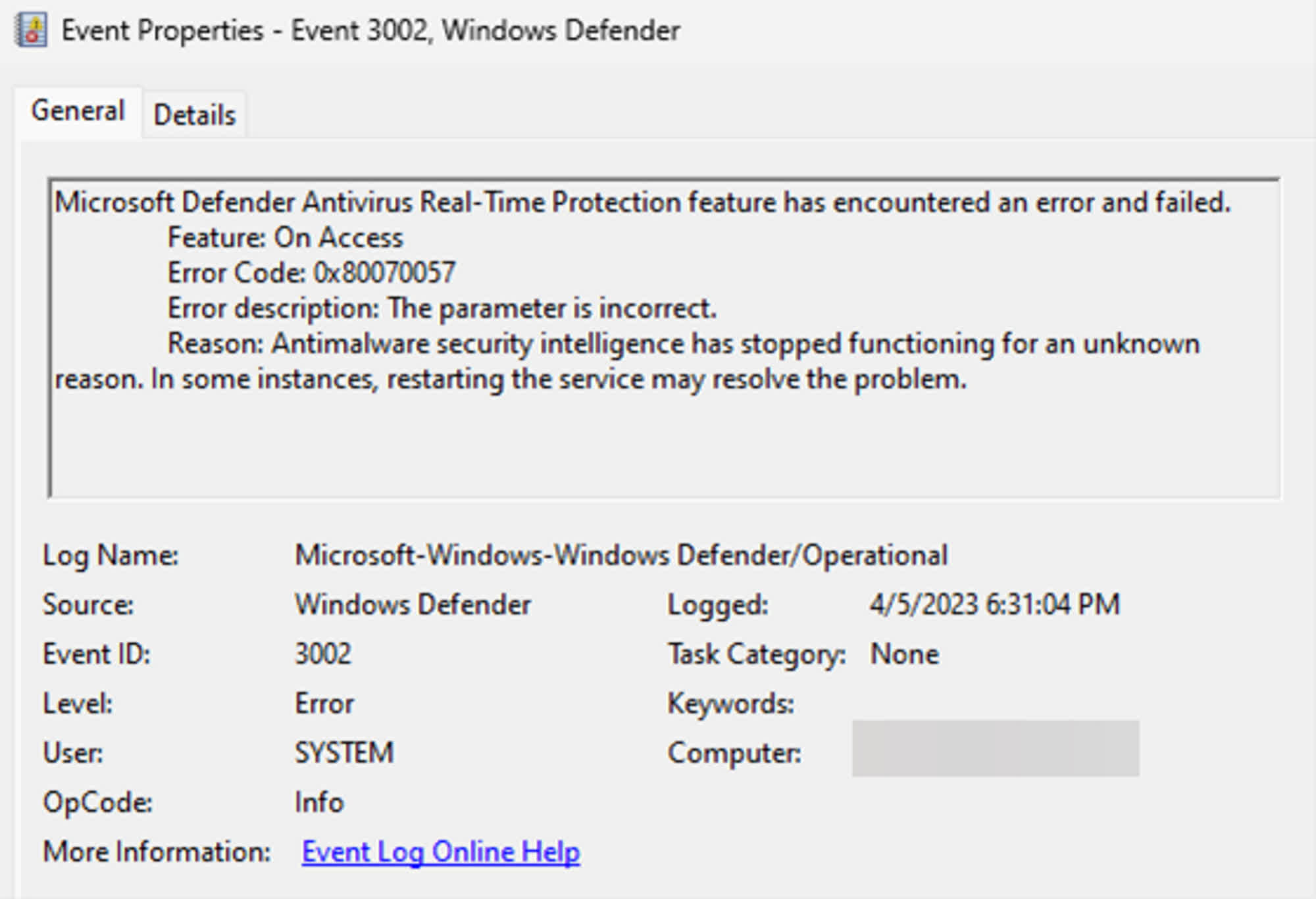
A BlackLotus infection can also be detected by searching for a "system32" folder within the EFI partition, which is the location where the malware installation is started. BlackLotus also modifies the Windows Registry to disable HVCI, while the Defender antivirus doesn't start anymore. Investigators can search for traces in the Windows Event Logs, including an "ID 7023" event generated when the Defender real-time protection service gets stopped "for an unknown reason."
Logs of outbound connections from winlogon.exe on port 80 can also reveal BlackLotus presence on the machine, as the bootkit's injected HTTP loader tries to reach the command&control server or perform "network configuration discovery." When the bootkit becomes active, Microsoft explains, two new boot drivers ("grubx64.efi," "winload.efi") can be seen by comparing logs.
Microsoft also provides instructions on how to prevent and remove a BlackLotus infection. Prevention is the best solution against traditional and invisible threats, Microsoft suggests, and system administrators should first avoid the use of domain-wide, admin-level service accounts by restricting local administrative privileges. Implementing multiple layers of security controls is the only strategy that can reduce risks, while disinfection can be done but requires a careful reinstallation of a clean operating system, EFI partition and UEFI firmware.