Why it matters: With the Pluton processor, Microsoft and chip makers AMD, Intel, and Qualcomm appear to be laying the groundwork for bringing a higher-level of PC security to all Windows 10-based PCs, both consumer and commercial. Technically, Pluton is IP -- the structure, design, and software of a processor block -- that will be embedded into future versions of CPUs from each of the three major PC chip vendors.
In the device world, one of the most popular celebrities out there is the Windows 10-based PC. It’s seeing shipment levels it hasn’t enjoyed in over a decade and, earlier this year, surpassed the one billion milestone in its installed base of monthly active users. While that’s great on one hand, it has also created its fair share of unwanted attention from bad guys -- hackers and other malfeasants who want access to the treasure trove of data, security certificates, passwords, digital identity tokens, and other valuable information either stored within or accessed from a PC.
Cognizant of these concerns, there have been numerous attempts over the years from hardware system makers, chipmakers, software companies, OS creators, and utility vendors to better secure PCs and their content. While some of these initiatives have been targeted across all types of PC users, most of the best and strongest efforts have been specifically targeted at enterprise PCs used in privacy-sensitive or regulated industries such as finance, health care, and manufacturing, as well as government and military applications.
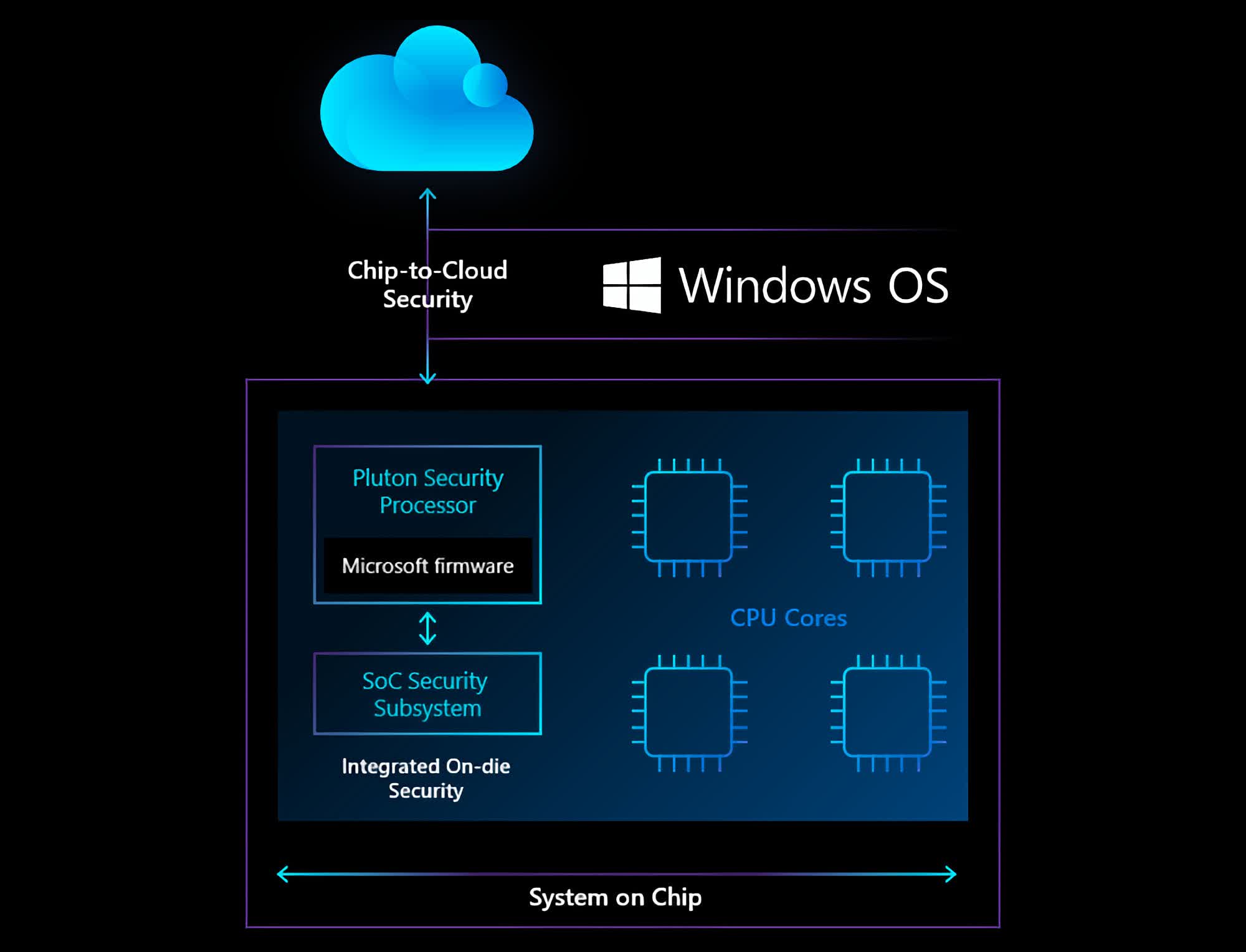
With this latest project, Pluton will bring the functionality of a separate TPM (Trusted Platform Module) chip directly into the CPU. TPMs, which are a type of hardware root of trust, are used to store security keys and to prevent unwanted firmware and other BIOS-related changes on a PC. TPMs are also used to enable system-level technology, like Windows Hello and BitLocker encryption.
Previous iterations of TPMs have existed on the same SoC package as the CPU, but the Pluton Processor effort is the first to put the capabilities directly into the CPU core. This is important because it helps solve a few potential security problems that have become more apparent as malware attacks, such as CPU-focused side channel efforts, have grown more sophisticated. First, it closes off the possibility of intercepting messages between the TPM and the CPU (which, up until now, have occurred over a system bus) in the event of a physical attack -- such as when someone steals or has direct in-person access to a computer.
Pluton will also store critical security data in encrypted form on the chip in a manner that is isolated from the rest of the system, thereby avoiding potential exploitation from new hacking techniques, such as those based on speculative execution, that attempt to move otherwise secure material into memory.
Finally, because Pluton is expected to be a single standard that will be deployed consistently across all three major PC CPU makers, it provides a new standard mechanism for doing updates down to the firmware level. This means that firmware and BIOS updates, which many people skip or simply don’t know exist, can be integrated into the normal Windows Update process, thus ensuring that more PCs stay completely up-to-date with all the latest security patches.
Interestingly, Microsoft developed some of the original functionality behind Pluton when it created the Xbox 360 game console CPU in conjunction with AMD back in 2013. It turns out that game consoles are one of the few devices where the users are the actual hackers -- in efforts to avoid paying for games, cheating in-game, etc. -- which forced Microsoft to take a zero-trust approach from within its own hardware. Many of those same principles are being used in Pluton, as well as a chip-to-cloud architecture Microsoft created for making highly secure cloud-based connections to update the console’s firmware (along with its Azure Sphere IoT devices).

Last year’s secured-core PCs were an important step forward in blocking the increasingly sophisticated and numerous attacks that business PCs are facing. Similarly, recent secure BIOS offerings from Dell, HP, and Lenovo, as well as individual endeavors from Intel and AMD, also helped deter some of these challenges. Truthfully, though, it was and still remains difficult to track all of the security efforts and to understand how they all fit together. At first glance, it appears that with Pluton, Microsoft is making an attempt to standardize around a single, even stronger, zero trust-based, hardware security paradigm that leverages these earlier efforts and extends them to an even broader range of PC users, a critically needed exercise.
Exactly when we’ll all be able to enjoy the security benefits that Pluton seems to offer is unknown, because details of when it will show up in future AMD, Intel, and Qualcomm CPUs (and in which models) have yet to be released. However, it’s clear even now that the core PC ecosystem partners are working together to improve the security of PCs across the board, and that’s something we can all appreciate.
Bob O’Donnell is the founder and chief analyst of TECHnalysis Research, LLC a technology consulting firm that provides strategic consulting and market research services to the technology industry and professional financial community. You can follow him on Twitter @bobodtech.
https://www.techspot.com/news/87634-microsoft-partners-intel-amd-qualcomm-pluton-processor.html