A hot potato: QNAP issued a security statement urging their NAS users to take immediate action and secure their data against ongoing ransomware and brute force attacks. While the responsible parties have not been identified, the widespread attacks appear to target any vulnerable network devices. The company has provided security setting instructions and mitigation actions that any QNAP NAS users should implement immediately.

A security statement released by the storage appliance provider on Friday issued very clear instruction to QNAP NAS users: take immediate action to secure your network appliances or take them offline. The attacks, which appear to indiscriminately target any network device exposed to the Internet, pose the most risk to devices with internet connectivity but little to no protection in place.
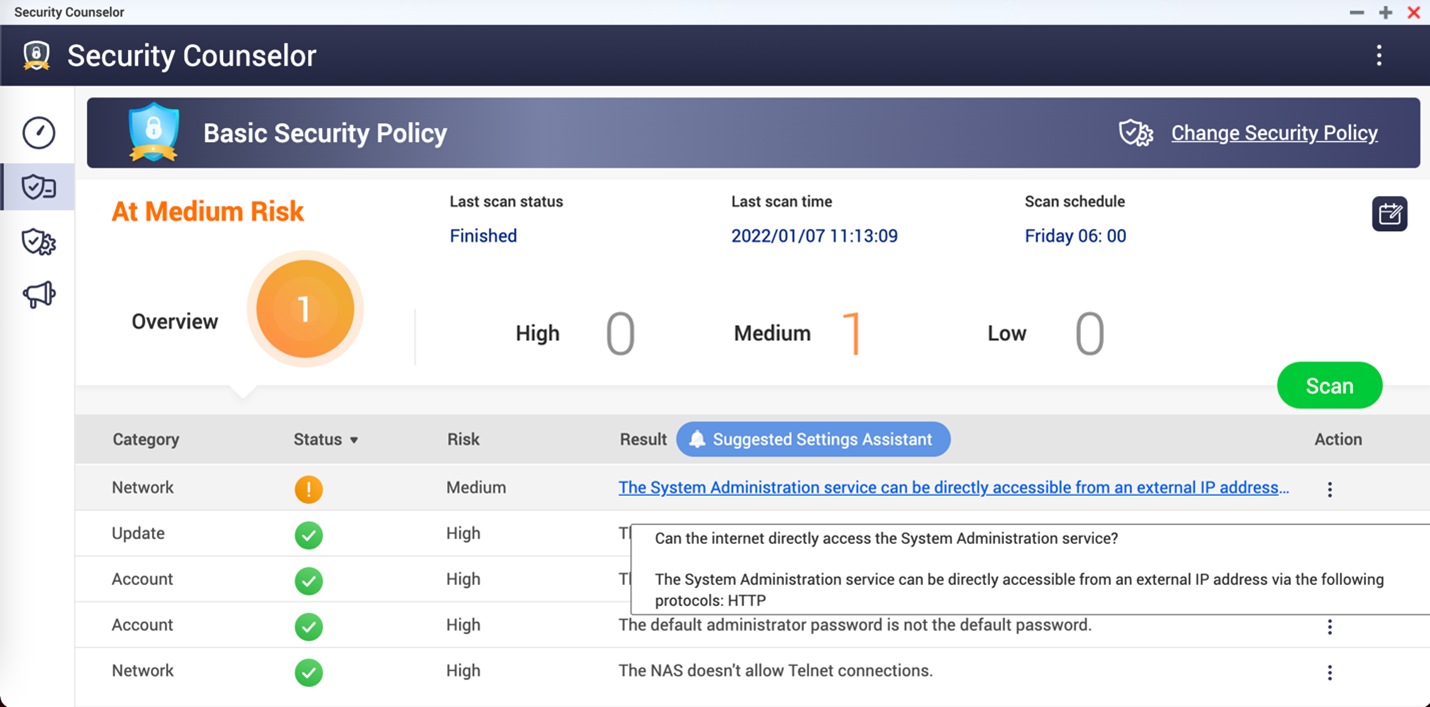
QNAP users with the ability to access and secure their devices can verify whether their device is exposed to the internet using the QNAP Security Counselor. According to the company's statement, the user's NAS is exposed and at high risk if the Security Counselor console displays a result stating, "The System Administration service can be directly accessible from an external IP address..."
In the event that a user's NAS is exposed to the Internet, QNAP's security statement provides instructions to determine which ports are exposed as well as how to disable port forwarding on the user's router and UPnP on the NAS device.
Port forwarding, also known as port mapping, redirects requests from the original address and port to another address and port. Some users and administrators no longer view port forwarding as a major risk, as software firewalls packaged with most modern operating systems are capable of providing adequate protection when properly configured.
However, QNAP has specifically stated that enabling port forwarding, UPnP, or demilitarized zone (DMZ) functionality can result in the NAS connecting directly to the internet, making the device vulnerable to attack. The recommended preference is for the NAS to remain behind a user's router and firewall with no public IP address.
NAS users without access to or familiarity with the Security Counselor console still have one last nuclear option--simply disconnect the device, terminating any potential connectivity to the outside world. While it may seem drastic, the fact remains that attackers scanning for vulnerable targets can't hit what they can't see.
Image credit: Michael Geiger
https://www.techspot.com/news/92909-qnap-issues-warning-users-secure-or-disconnect-unprotected.html