Why it matters: Apple and other companies have enacted numerous measures to ensure that AirTags and similar tracking fobs aren't used for stalking. Still, a group of researchers is disappointed with the latest official methods. A recent paper outlines a solution that could solve the compromise between privacy and security.

Researchers from Johns Hopkins University and the University of California have suggested a set of cryptographic tools that could counteract AirTag stalking better than Apple's current measures. The researchers believe that Apple's default anti-stalking features can compromise legitimate users' privacy.
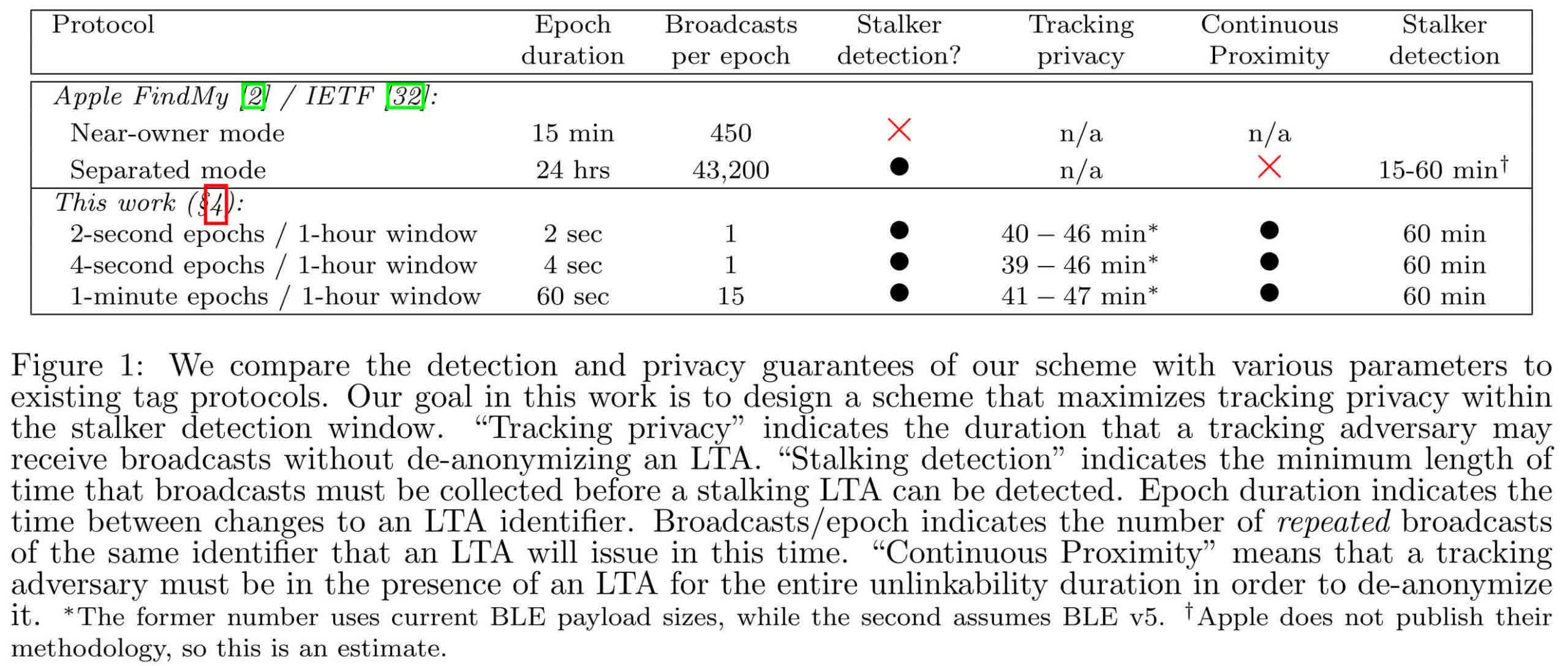
The central problem is determining when an AirTag is used for illicit purposes. Smartphones can alert users when foreign AirTags follow them across long distances, but the warning system struggles to differentiate between stalkers and friends or family members who also own AirTags.
Click to enlarge
Apple's response to the problem switches the fobs between two modes depending on their proximity to their paired devices. When an AirTag remains close to the owner's device, such as their iPhone, it switches between identification keys every 15 minutes to ensure only the owner can detect the AirTag. However, if the fob is away from its paired device for an extended period, the key only changes once daily, allowing potential stalking victims to more easily identify foreign AirTags. As Apple coordinates with other companies to homogenize security protocols across platforms, the company's method could become the standard, which worries the researchers.
The "away" mode effectively de-anonymizes an AirTag, but the researchers found that many users frequently carry them away from their paired devices, thus constantly broadcasting their locations and movements. One possible cause is that families sharing fobs can't easily pair them to multiple devices. Furthermore, a friendly visitor carrying their AirTag could confuse the system.
Under the researchers' proposal, fobs would always constantly change their key signals, but devices could only identify them after receiving a certain number of signals at close range, indicating that an AirTag is following someone. Meanwhile, a malicious actor would likely spend significant time away from the fob and wouldn't gather enough signals to identify it. A second component of the system would help each device differentiate between signals if many AirTags or other Apple devices in the "Find My" mode are nearby.
The researchers have submitted their study to Apple and the consortium of companies cooperating on tracking fobs, but manufacturers haven't indicated any interest in the findings so far.