The big picture: Computers with a password-locked BIOS can be a bit of a hassle. While the intention of the feature is to ensure the privacy and security of the device, passwords can be easily forgotten or maliciously enabled. What can you do in this situation? Reach for a screwdriver, perhaps.

Experts at cybersecurity firm CyberCX unintentionally put themselves in this exact situation. Old Lenovo L440 laptops the company used in the past had their BIOS "conveniently locked" once the devices were decommissioned. The experts decided to use the computers as test subjects to learn how to break through BIOS passwords.
While the initial thought was to remove the CMOS battery, in recent years, manufacturers have begun keeping BIOS passwords on non-volatile storage, meaning a reset would do nothing. The experts then decided to target a specific chip on the motherboard, the Electrically Erasable Programmable Read-Only Memory (EEPROM) chip. Bypassing this module could result in skipping the password prompt entirely.
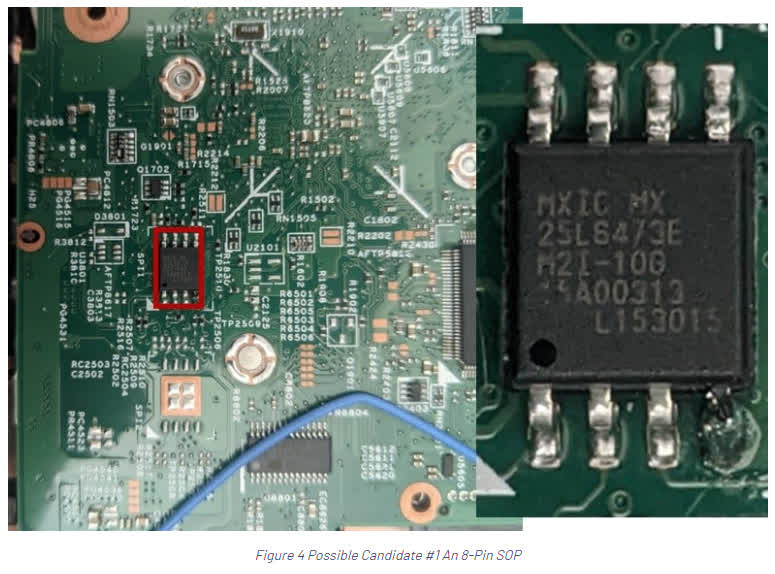
They quickly ran into an issue with this: finding the correct chip. The laptops had two other chips that looked similar to the specific EEPROM they were searching for. Once a user identifies the correct chip, the steps to bypass the BIOS password are rather simple, with the hardest part being locating the specific pins that need to be shorted:
- 1. Locate the correct EEPROM chip.
- 2. Locate the SCL and SDA pins.
- 3. Short the SCL and SDA pins at the correct time.
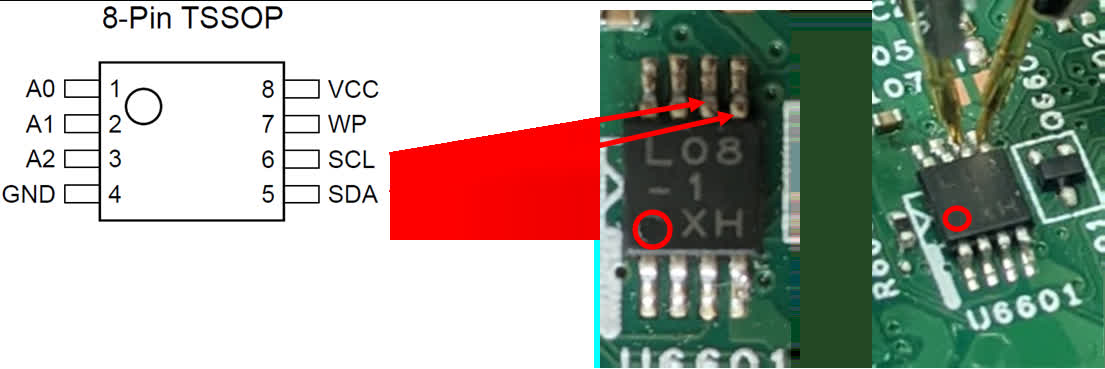
It is worth noting that the timing is not very strict; in fact, it is rather lenient. In the embedded video within the original post, the expert performing the bypass simply shorts the pins after powering the laptop. If you perform the trick correctly, you should load right into the BIOS with no password prompt, enabling you to disable said password.
Unfortunately, this trick will likely only work on older laptops, as manufacturers have recently begun merging the BIOS and EEPROM chips together in a Surface Mount Device (SMD). This change means a bypass on a modern laptop would require an "off-chip attack," which is significantly more difficult to pull off, especially for ordinary users.