The big picture: Months after Kaspersky's initial report on an extremely sophisticated spyware affecting iPhones, the security company revealed new details that could indicate the full breadth of its reach. The latest Apple firmware is no longer vulnerable to this attack, but a significant mystery remains regarding its development.

A new report from Kaspersky's security team outlines all the currently known details of "Triangulation," arguably the most sophisticated iOS spyware ever discovered. The most intriguing detail is that it relies on exploits hidden so deeply that virtually no one outside of Apple could have known about them.
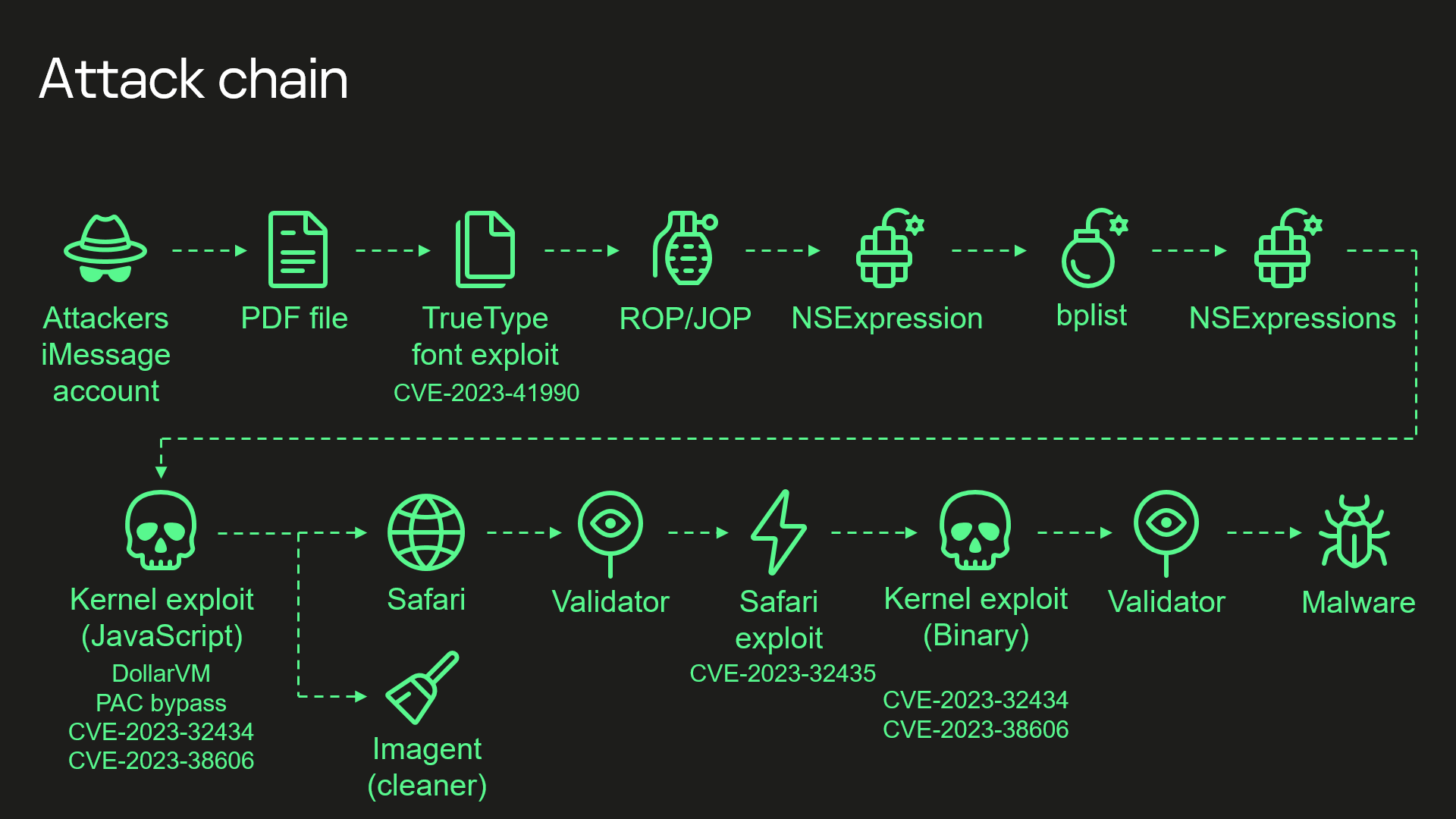
Triangulation is the name the Russian security company gave to the spyware it found on iPhones used by its employees earlier this year. The malware, affecting iOS versions 15.7 and earlier, leaked microphone recordings, location data, and more.
More concerning is that the spyware is "zero-click." It activates when a phone receives a text message with a malicious attachment, without requiring the user to open or read the message. It bypasses Apple's hardware protections and can access a device's entire physical memory. Furthermore, the malware remains active even after the message is deleted.
Initial research suggested that the spyware campaign has been ongoing since at least 2019. However, Kaspersky's latest findings indicate support for iOS versions older than 8.0, released in 2014.
The big mystery is how Triangulation came to rely on undocumented Apple hardware features, never mentioned in the company's firmware. This functionality and related exploits should be known only to developers inside Apple and possibly Arm.
The revelations might strengthen accusations from Russia's FSB that Apple and the NSA have been collaborating to plant spyware on iPhones used by diplomats from Russia and various other countries. Apple has denied the claims, and Kaspersky has not ruled out any possibilities. The company suggests that the secret functions were intended for internal debugging and that extremely skilled hackers could have discovered them while reverse engineering the system.
Triangulation also exploited four zero-day vulnerabilities affecting iPhones, iPads, Macs, Apple Watches, and Apple TVs. However, Kaspersky has not found evidence of the spyware on products other than iPhones. Apple fixed the security flaws with updates including iOS 16.6, iPadOS 16.6, tvOS 16.6, watchOS 9.5.3, and macOS Ventura 13.5.