I'm desperately in need of help here - seems like nobody as the answer for fixing issues with random windows updates problems. I work for a company that has 212 servers total.
Our 2016 servers are all over the place with updates - they don't install, sometimes they do install but don't reboot, sometimes they won't pull updates in - this is random on any given server - one month it will have the issue then the next it won't. We were made aware of a dual scan issue with 2016 and I've listed the GP updates below that we've changed to try and disable it but it didn't work.
Our 2012 servers also have the same issues but nowhere near as bad and there few and far between.
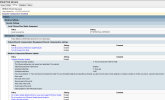
I have also included screenshots of our WSUS policy setup below - they are the same across all environments.
We use "PDQ Deploy" to deploy are updates (after they have been approved via WSUS) and I don't think anything is wrong with the script that it setup to handle the update schedules.
I've noticed that while the correct registry settings are in place for servers to communicate with their WSUS server (HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate - the keys "WUServer and WUStatusServer") have the correct entries, the servers WON'T pull into WSUS. I have tried running the wuauclt /detectnow no command it just completes with no result or error and the server still doesn't appear in WSUS.
I really thought this would be an easy thing to fix but it's driving me nuts - I need to fix the dual scan issue for 2016 servers and be able to make the servers show up in their assigned WSUS server console (all the 2012 servers show up mainly the 2016 servers don't) and of course overall, just have every server update properly every patching period.
Any help would be greatly appreciated.
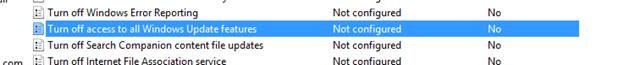
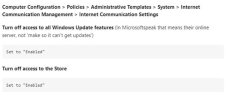
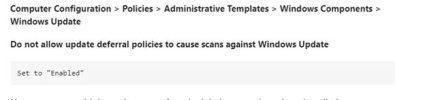
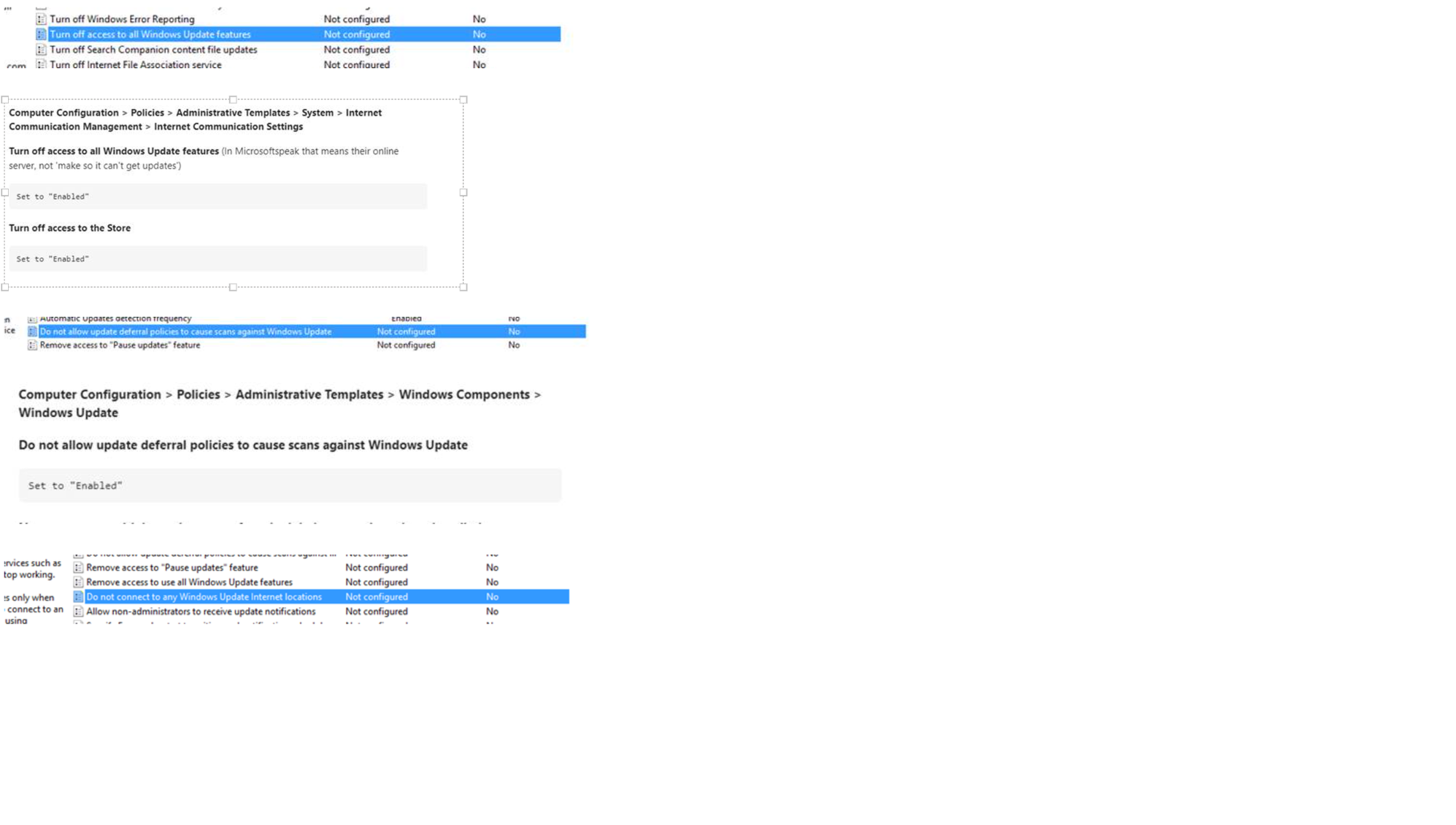
Please see the attached for Group policy settings and the policy settings that were used to fix dual scanning for our 2016 servers (don't think they worked). Please note, theie are only two images for the main group policy object settings then the rest are for the dual scan issue.
Our 2016 servers are all over the place with updates - they don't install, sometimes they do install but don't reboot, sometimes they won't pull updates in - this is random on any given server - one month it will have the issue then the next it won't. We were made aware of a dual scan issue with 2016 and I've listed the GP updates below that we've changed to try and disable it but it didn't work.
Our 2012 servers also have the same issues but nowhere near as bad and there few and far between.
I have also included screenshots of our WSUS policy setup below - they are the same across all environments.
We use "PDQ Deploy" to deploy are updates (after they have been approved via WSUS) and I don't think anything is wrong with the script that it setup to handle the update schedules.
I've noticed that while the correct registry settings are in place for servers to communicate with their WSUS server (HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate - the keys "WUServer and WUStatusServer") have the correct entries, the servers WON'T pull into WSUS. I have tried running the wuauclt /detectnow no command it just completes with no result or error and the server still doesn't appear in WSUS.
I really thought this would be an easy thing to fix but it's driving me nuts - I need to fix the dual scan issue for 2016 servers and be able to make the servers show up in their assigned WSUS server console (all the 2012 servers show up mainly the 2016 servers don't) and of course overall, just have every server update properly every patching period.
Any help would be greatly appreciated.
Please see the attached for Group policy settings and the policy settings that were used to fix dual scanning for our 2016 servers (don't think they worked). Please note, theie are only two images for the main group policy object settings then the rest are for the dual scan issue.