WTF?! A new report from the US Government Accountability Office (GAO) is highlighting how American diplomacy (still) doesn't know the meaning of "cyber-security practices." The State Department has a proper cybersecurity risk management program, but it's just on paper.
The GAO-23-107012 report from the US GAO investigated the sad state of cyber-affairs in the US State Department, the government body that carries out American diplomacy and helps shape US foreign policy. Securing the IT systems that support the State's mission should be a crucial goal, and it's a goal that the department has been exceptionally good at failing so far.
GAO's report says that the Department of State has already documented a cybersecurity risk management program that "meets federal requirements." The program identified risk management roles and responsibilities, with a proper risk management strategy. The plan, however, has not been "fully" implemented, and the State Department cannot even identify or monitor risks for its IT assets - or how many IT assets it really owns.
The full report says that the US State Department is "likely not fully aware" of the information security vulnerabilities and cyber-threats affecting its mission operations. The State has an adequate "Cyber Incident Response Team" for monitoring and identifying security issues 24/7, but it lacks "fully implemented processes" that support its incident response program.
The US State Department has "not adequately secured" its IT infrastructure, and this could be the understatement of the year as the government body is likely still using PCs based on Windows XP. Certain operating system installations had reached end-of-life "over 13 years ago," GAO confirms, which is almost exactly aligned with the end of XP's mainstream support on April 14, 2009. Microsoft provided extended support for its legendary PC OS up to April 8, 2014.
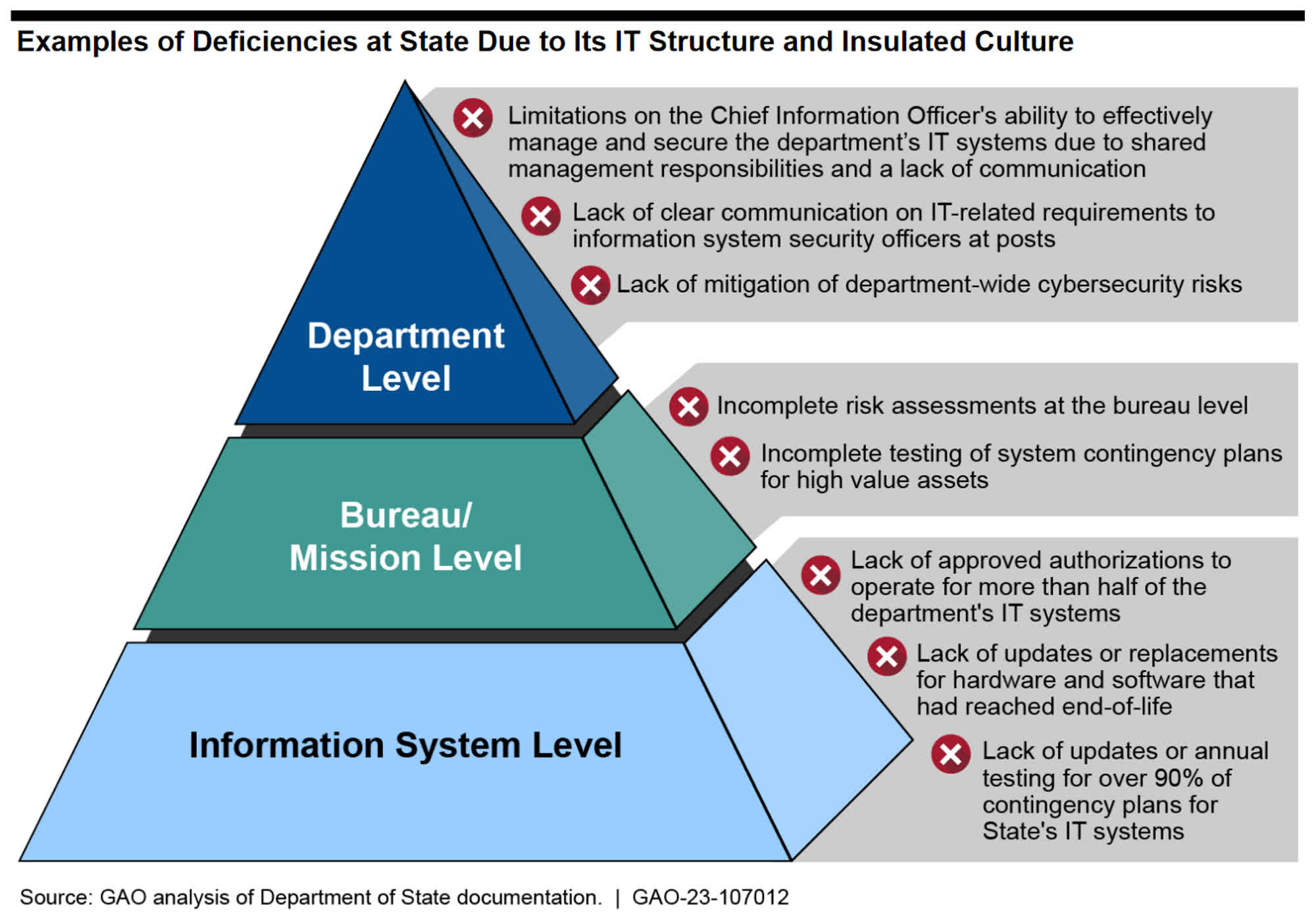
Other issues with the IT infrastructure include 23,689 "hardware systems" and 3,102 network and server operating system installations that have reached their end-of-life and are no longer supported. When IT security doesn't provide enough reasons for concern, GAO's report remarks, the US State Department is very successful in sabotaging itself thanks to its bureaucratic practices and federated structure.
The State has split IT management responsibilities between its CIO and sub-organizations, with an "insulated culture" that favors lack of communication and is ultimately responsible for many of the deficiencies identified in the report. Because of this communication issue, GAO says, the Department's enterprise configuration management (ECM) database cannot provide a full picture of all the hardware and software still in use. The ECM database seemingly has absolutely no data of IT assets used in 20 of the State's diplomatic outposts.
GAO has prepared 15 recommendations to address the many issues discovered in the US State Department IT infrastructure. Furthermore, the overseeing Office will later issue another report with "limited distribution" highlighting another 500 recommendations to remediate the sad State of affairs of America's diplomacy body.
