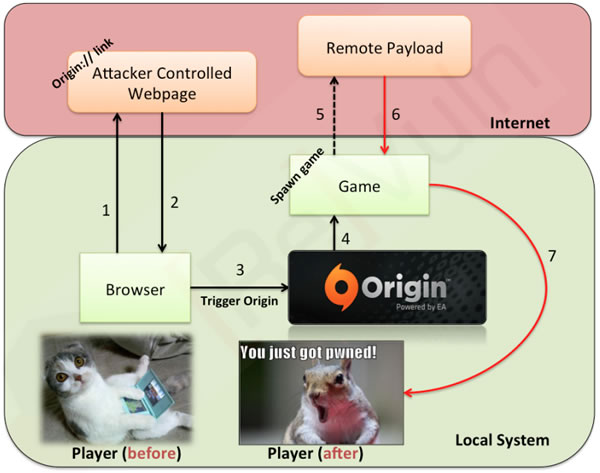
Upwards of 40 million users of EA's Origin game platform could be open to a vulnerability that allows an attacker to remotely execute malicious code. Demonstrated by ReVuln on Friday at the Black Hat security conference in Amsterdam, the process requires Origin's client to be installed on the victim's machine and it can be exploited when the user clicks a specially crafted link.
The issue stems from Origin's use of specific uniform resource identifiers (URIs) to communicate with games. When it launches a title, it sends an "origin://LaunchGame/
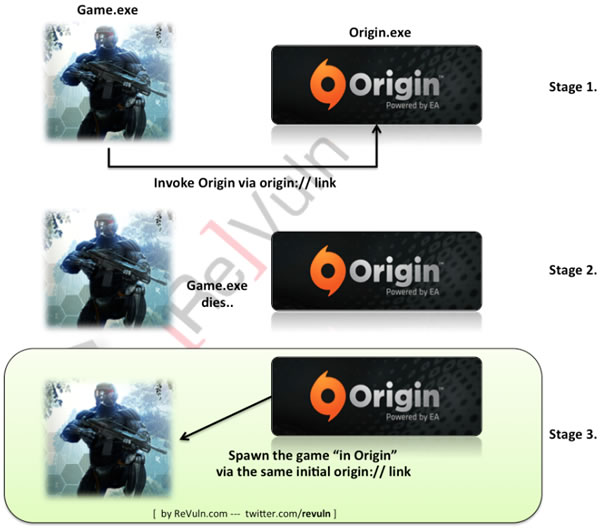
Because that link can contain CommandParams, an attacker could deliver a payload targeting software on your system with a couple of simple commands. For example, ReVuln says this would invoke the Nvidia benchmark framework and then download a tainted DLL: origin://LaunchGame/
What's more, as we understand it, Origin doesn't even have to be running – again, just installed – and it's possible that an attacker could exploit a system transparently, especially if the person has their system configured to handle origin:// links automatically. As such, at a minimum, folks are encouraged to make sure their browser is set to issue a prompt when handling those links.
If you're looking to clamp down a bit more than that, the researchers recommend that you disable the origin:// URI globally with a tool such as Nirsoft's URLProtocolView. This will prevent you – and anyone else – from running games via shortcuts with custom parameters on your system, but ReVuln says you'll still be able to play games by running them directly from Origin's client.
It's worth noting that this isn't a new problem. The same security group exposed a similar issue on Steam last year: maliciously crafted "steam://" links could be used for remote code execution. Valve plugged that hole roughly two days after ReVuln's report was released. It's unclear if or when EA will issue a fix, not least considering it's had five months to act since the Steam issue.