Android has become an increasingly popular target for malware authors, a recent report (pdf) by NQ Mobile indicates. The security firm claims that it discovered over 65,000 types of malware – more than double the amount from 2011 – and bills Android as the number one mobile platform targeted by malware attacks.
Forms of social engineering (i.e. phishing) remain a favored way to attack Android owners for profit. Smishing, a SMS-based phishing technique, is one such tactic popular in the mobile world. Meanwhile, repackaged apps from third-party app stores and malicious websites were also common vectors of infection exploited by malware authors.
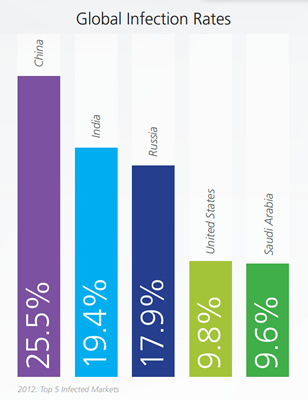
While the number of infected packages effectively doubled, the quantity of infected Android devices tripled between 2011 and 2012 from 24,794 to 65,227. In 2009, that number was only 1,649.
The most noteworthy Android-based badware was "Bill Shocker", a prolific mobile malware which NQ Mobile labeled as the most infectious and costly in history. Largely only an issue in China, the aptly named Bill Shocker would take control of an Android smartphone and silently send texts from the device to premium rate numbers. Premium SMS messages are billed to the owner's account without their explicit consent – this is also known as toll fraud.
Other honorable mentions include VDloader, DDSpy, DyPusher and FireLeaker – each with their own distinct attack vectors and payloads.

Although most malware is ostensibly incentivized by financial motives, as many as 7 percent of payload-carrying packages were designed to brick a user's smartphone. Meanwhile, 28 percent were designed to collect information for profit while 65 percent fell into the often less-hazardous category of PUP (a potentially unwanted program).