The iCloud security incident that made headlines early this month could possibly have been prevented. That's because London-based software developer Ibrahim Balic claims to have reported a brute-force iCloud password attack to the Cupertino-based company nearly six months ago.
The Daily Dot obtained e-mails between Balic and Apple showing the developer informed them of a brute-force attack that shares a stark resemblance to the exploit believed to have been used to leak hundreds of photos of celebrities in the buff a few weeks ago.
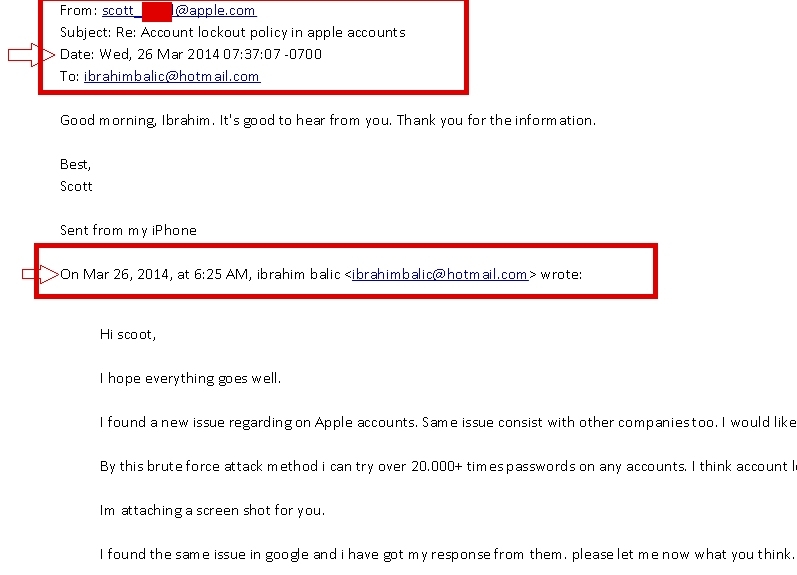
In one exchange dated March 26, 2014, Balic explains he was able to try more than 20,000 different passwords on any account which highlighted the fact that there wasn't any sort of lockout policy in place. The screenshot shows he did receive a reply from someone named Scott at Apple.
The developer also reported the vulnerability through Apple's official online submission platform.
Typically, a login will only allow for so many failed password attempts before locking the account down to protect against brute-force attacks that use trial-and-error to successfully hack an account.
Balic said Apple repeatedly asked him for more information on the matter and at one point, an Apple Product Security member seemingly dismissed the attack as taking too long to find a valid authentication token for an account.
Apple addressed the matter shortly after, basically admitting that celebrities' iCloud accounts were compromised although iCloud and Find my iPhone weren't to blame. Instead, Apple said hackers correctly answered security questions to obtain their passwords or they may have been victimized by a phishing scam to obtain user IDs and passwords.
Moving forward, Apple promised to notify users via e-mail and push notification if someone tries to change an account password. The company also enabled two-factor authentication when accessing iCloud accounts from a mobile device.