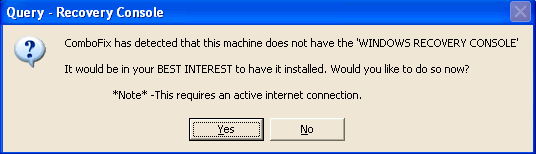
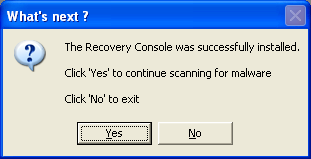
Oh, my, goodness.
Go to add remove programs and unistall sweetim if present, it may be bundled with Macrogaming.
This next step is purely optional however viewpoint is considered foistware and is not needed on your computer,
'To provide a satisfying consumer experience and to operate effectively, the Viewpoint Media Player periodically sends information to servers at Viewpoint. Each installation of the Viewpoint Media Player is identifiable to Viewpoint via a Customer Unique Identifier (CUID), an alphanumeric identifier embedded in the Viewpoint Media Player. The Viewpoint Media Player randomly generates the CUID during installation and uses it to indicate a unique installation of the product. A CUID is never connected to a user's name, email address, or other personal contact information. CUIDs are used for the sole purpose of filtering redundant information. Each of these information exchanges occurs anonymously.'
Go to Start > Run and copy/paste or type: taskmgr
- Under the Processes tab find the following tasks or processes:
ViewpointService.exe
ViewMgr.exe
- Highlight and click "End Process".
- Exit Task Manager.
Click on Start > Run and type: services.msc
- Press "OK".
- Click the "Extended tab".
- Scroll down the list and find the service called "Viewpoint Manager Service"
- When you find the service, double-click on it.
- In the Properties Window > General Tab that opens, click the "Stop" button.
- From the drop-down menu next to "Startup Type", click on "Disabled".
- Now click "Apply", then "OK" and close any open windows.
Click on Start > Settings > Control Panel > Add/Remove Programs > highlight and remove all references to Viewpoint - i.e.
Viewpoint, Viewpoint Manager, Viewpoint Media Player.
Finally, delete the following folders if they still exist:
C:\Program Files\ViewManager\ <-- and delete this folder
C:\Program Files\Viewpoint\ <-- and delete this folder
Run CFScript
Open
notepad and copy/paste the text in the code box below into it:
NOTE* make sure to only highlight and copy what is inside the quote box nothing out side of it.
Also ..
Pay particular attention to this :-
Make sure the word File:: is on the first line of the text file you save (no blank line above it, & no space in front of it)
File::
c:\windows\system32\dodedeva.dll
c:\windows\instsp2.exe
c:\windows\system32\fugafizu.dll
c:\windows\instsp1.exe
c:\windows\system32\juhijudu.dll.vir
c:\windows\system32\sepajimo.dll
c:\windows\system32\rajuguke.dll
c:\windows\system32\miperuwo.dll
c:\windows\system32\lofuvika.dll
c:\windows\system32\zopiwahe.dll
c:\windows\system32\wopilawu.dll
c:\windows\system32\zizaduvu.dll
c:\windows\system32\nefuwipi.dll
c:\windows\system32\nahilifo.dll
c:\windows\system32\mivojova.dll
c:\windows\system32\wolugeri.dll
c:\windows\system32\wehebopa.dll
c:\windows\system32\yelosuso.dll
c:\windows\system32\pavogare.dll
c:\windows\system32\feyajute.dll
c:\windows\system32\vufosesa.dll
c:\windows\system32\dunulaju.dll
c:\windows\system32\yivoboki.dll
c:\windows\system32\kiyajeru.dll
c:\windows\system32\zopeyuhi.dll
c:\windows\system32\luveteyo.dll
c:\windows\system32\ziniguhe.dll
c:\windows\system32\fonaneki.dll
c:\windows\system32\nezogeju.dll
c:\windows\system32\nisinupo.dll
c:\windows\system32\redivipo.dll
c:\windows\system32\virinida.dll
c:\windows\system32\zadowebi.dll
c:\windows\system32\bevukeyo.dll
c:\windows\system32\refobaju.dll
c:\windows\system32\jigefuwi.dll
c:\windows\system32\tebudati.dll
c:\windows\system32\gavulowe.dll
c:\windows\system32\newuwiyo.dll
c:\windows\system32\gerogije.dll
c:\windows\system32\lewiyidi.dll
c:\windows\system32\bonafanu.dll
c:\windows\system32\yosineku.dll
c:\windows\system32\hilafija.dll
c:\windows\system32\jepazeje.dll
c:\windows\system32\gizisuyo.dll
c:\windows\system32\veyevida.dll
c:\windows\system32\tiwedihu.dll
c:\windows\system32\zebelivu.dll
c:\windows\system32\risumega.dll
c:\windows\system32\pajazeba.dll
c:\windows\system32\wumugaka.dll
c:\windows\system32\nalusihe.dll
c:\windows\system32\hiwipafi.dll
c:\windows\system32\hizohunu.dll
c:\windows\system32\gidahumu.dll
c:\windows\system32\ruyopaku.dll
c:\windows\system32\kidoyera.dll
c:\windows\system32\hetuyevo.dll
c:\windows\system32\fifugiku.dll
c:\windows\system32\gitisowe.dll
c:\windows\system32\fupipivo.dll
c:\windows\system32\zasulege.dll
c:\windows\system32\tojowebo.dll
c:\windows\system32\muwevola.dll
c:\windows\system32\zibibozi.dll
c:\windows\system32\fimohinu.dll
c:\windows\system32\jifopufo.dll
c:\windows\system32\vodewenu.dll
c:\windows\system32\wokoguri.dll
c:\windows\system32\zerarapo.dll
c:\windows\system32\dezuzara.dll
c:\windows\system32\bodalene.dll
c:\windows\system32\gemidesu.dll.vir
c:\windows\system32\zogovaro.dll
c:\windows\system32\hajigira.dll
c:\windows\system32\tuhemasa.dll
c:\windows\system32\joludune.dll
c:\windows\system32\telezeva.dll
c:\windows\system32\gidobedi.dll
c:\windows\system32\lehelojo.dll
c:\windows\system32\waduzaga.dll
c:\windows\system32\gevimasi.dll
c:\windows\system32\kosuyapu.dll
c:\windows\system32\jowuhese.dll
c:\windows\system32\veseyusi.dll
c:\windows\system32\niyihifi.dll
c:\windows\system32\nevihezu.dll
c:\windows\system32\jituwuwa.dll
c:\windows\system32\jiremeye.dll
c:\windows\system32\zitakihu.dll
c:\windows\system32\binatoko.dll
c:\windows\system32\juposeno.dll
c:\windows\system32\komabagi.dll
c:\windows\system32\dukotibe.dll
c:\windows\system32\defarewo.dll
c:\windows\system32\dedovewu.dll
c:\windows\system32\dojiralo.dll
c:\windows\system32\F5DD7F3EA3.sys
c:\windows\system32\farakive.dll
c:\windows\system32\fiyahena.dll
c:\windows\system32\heyakiko.dll
c:\windows\system32\KGyGaAvL.sys
c:\windows\system32\knjemr.dll
c:\windows\system32\ldjtkp.dll
c:\windows\system32\masekaba.dll
c:\windows\system32\numitopi.dll
c:\windows\system32\pamukuhu.dll
c:\windows\system32\royotago.dll
c:\windows\system32\swzzkm.dll
c:\windows\system32\yadebene.dll
c:\windows\system32\zakawuli.dll
Folder::
C:\KEWGZXJVDERAPVAD
c:\program files\Viewpoint
Registry::
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SweetIM"=-
"dikowasobe"=-
"CPM73d31624"=-
"70e025b8"=-
Save this as
CFScript.txt
Then drag the CFScript.txt into ComboFix.exe as you see in the screenshot below.
This will start ComboFix again. After reboot, (in case it asks to reboot), post the contents of Combofix.txt in your next reply together with a fresh HJT log.
Please download
ATF Cleaner by Atribune.
Double-click ATF-Cleaner.exe to run the program.
Under Main choose: Select All
Click the Empty Selected button.
If you use Firefox browser
- Click Firefox at the top and choose: Select All
Click the Empty Selected button.
NOTE: If you would like to keep your saved passwords, please click No at the prompt.
If you use Opera browser
- Click Opera at the top and choose: Select All
Click the Empty Selected button.
NOTE: If you would like to keep your saved passwords, please click No at the prompt.
Click
Exit on the Main menu to close the program.
For
Technical Support, double-click the e-mail address located at the bottom of each menu.
- Open a folder window (for example, double-click My Computer).
- From the Explorer menu select Tools | Folder Options | View. Make sure that you have checked the box next to "Show hidden files and folders" and uncheck "Hide protected operating system files".
- Start Internet Explorer and click Tools | Internet Options | General tab | Settings | View Files.
- IE should have opened up a folder window, typically viewing a folder with the name of C:\Windows\Temporary Internet Files. Put your cursor in the Address area of the folder window and add the name \content.ie5 to the name, so in our example the Address bar would now read c:\Windows\Temporary Internet Files\content.ie5.
- You should see a series of folders with random eight-character names like ADOZMZS1. Delete each of these randomly named folders. You may get an error that some files are in use, this is normal if you are currently at a web site since those files are in the cache. Hold down the Shift key when deleting the files so they do not go to the Recycle Bin.
FindAWF
Download
FindAWF.exe and save it to your desktop.
- Double-click on the FindAWF.exe file to run it.
- It will open a command prompt and ask you to Press any key to continue.
- Press 1 and then Enter, and the FindAWF tool will begin scanning your computer for the infected AWF files and the backups the trojan created.
- It may take a few minutes to complete so be patient.
- When it is complete, it will open a text file in notepad called AWF.txt which will automatically be saved to your desktop or to the same location as FindAWF.exe.
- Attach the AWF.txt file in your next reply.
After this run a fresh HijackThis log for me.
In your responce you should have,
1)ComboFix log
2)AWF log
3)HijackThis log