Cutting corners: Past auto theft attempts have involved anything from smashing windows to relaying FOB code sequences. But a rash of bumper and headlight damage has led researchers to a new approach that relies on the vehicle's controller area network (CAN) and using what looks like nothing more than a simple speaker to gain access. And to make matters worse, it takes about two minutes from start to finish.

Sometimes criminals inadvertently pick the wrong target when planning a crime. In this case, car thieves leveraging a new tactic for keyless access and stealing vehicles happened to pick the Toyota SUV of a cybersecurity analyst who specializes in automotive security. And what he found was a tactic that went beyond both simple smash and grab and more complex signal hijacking methods.
Ian Tabor, a cybersecurity and car hacking expert, identified CVE-2023-29389, which says Toyota RAV4 vehicles are capable of automatically trusting messages from other electronic control units (ECUs). By pulling away the bumper to expose the headlight connector, the thief can gain access to the CAN bus, allowing them to send a forged key validation message. Once validated, the thief can start the car and drive off without issue.
After researching the data and communication behavior across the RAV4's CAN bus, Tabor discovered that other ECUs were failing at the same time as the CAN bus errors. The discovery drove Tabor to conduct additional research via YouTube, the dark web, and other sources. Tabor's research resulted in buying and analyzing an emergency start device, which is intended for use by owners or locksmiths when a key is lost, stolen, or otherwise unavailable. Working with another automotive security expert, Ken Tindell, Tabor successfully reverse engineered the emergency start device, developing an understanding of how the device communicated with the Toyota's CAN bus.
Despite being advertised as an emergency start device, the item that Tabor purchased and used was designed to look like a simple JBL portable speaker. According to Tindell, a fake play button on the speaker case is wired into a PIC18F chip. When pressed, a CAN message burst instructs the door ECU to unlock the vehicle's doors. Once unlocked, the thieves unhook the CAN Injector, get into the car, and drive away. Full details of the device, how it works, and how easily (and cheaply) it can be fabricated are available on the Canis Automotive Labs website.
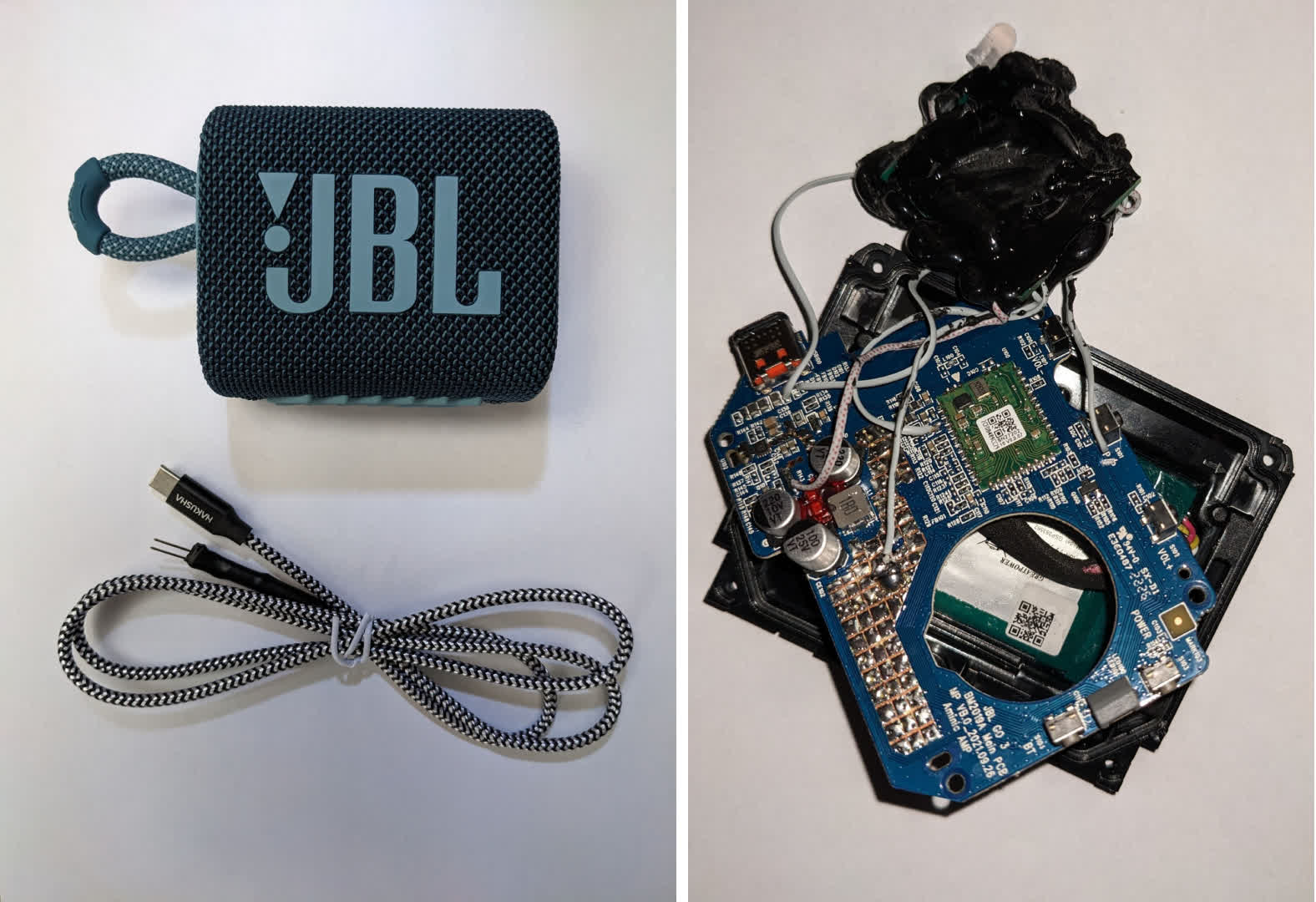
While the attack was successfully replicated on a Toyota RAV4, it's reasonable to believe that a similar attack could occur on other vehicles using the same technology and architecture. Tabor and Tindell have alerted Toyota to the vulnerability in hopes that it can be hardened and no longer exploited. Unfortunately, they have not yet received any acknowledgement or response.
https://www.techspot.com/news/98245-car-thieves-using-fake-jbl-speakers-not-keys.html