In brief: Most security researchers focus on finding low level vulnerabilities and fixing them before they're exploited by hackers, but a team of Israeli academics have taken the task of finding the most peculiar methods of eavesdropping on a PC that wouldn't typically cross your mind.

Hackers who want to steal sensitive data from computers can sometimes get very creative with their methods, but most of the time they exploit bad security practices and software vulnerabilities to achieve their goals. Sometimes, hackers use popular tools of the trade to hack other hackers, but that skill level is relatively rare.
Researchers at the Ben Gurion University in Israel aren't leaving any stones unturned however. They've built a reputation of finding peculiar but feasible techniques for stealing data from so-called air-gapped PCs -- systems that are physically isolated with no Internet access -- without being detected.
Their newest technique called AiR-ViBeR started as an idea that you could theoretically use vibrations produced by electromechanical components like a CPU, GPU, or case fans in combination with special malware that is able to encode the data to be transmitted through direct manipulation of the fan speed.
In their proof-of-concept, the researchers used a smartphone placed on the same table as the PC to record the changes in vibration using the accelerometer, which is sufficiently precise in high-end devices like the Galaxy S10, which has a sensor with a resolution of 0.0023956299 meters per second squared.
One of the advantages of this method is that both Android and iOS don't request user permissions to read the output of the accelerometer in your phone, meaning there's no visual indication that something is going on in the background.
Furthermore, the attacker doesn't need to compromise the mobile device in any way, since this can achieved more elegantly via your favorite web browser using JavaScript. We know that this is feasible since it's happened in the recent past, when minorities in China were targeted on both mobile platforms through legitimate-looking websites that can fool the unsuspecting eye of the average user.
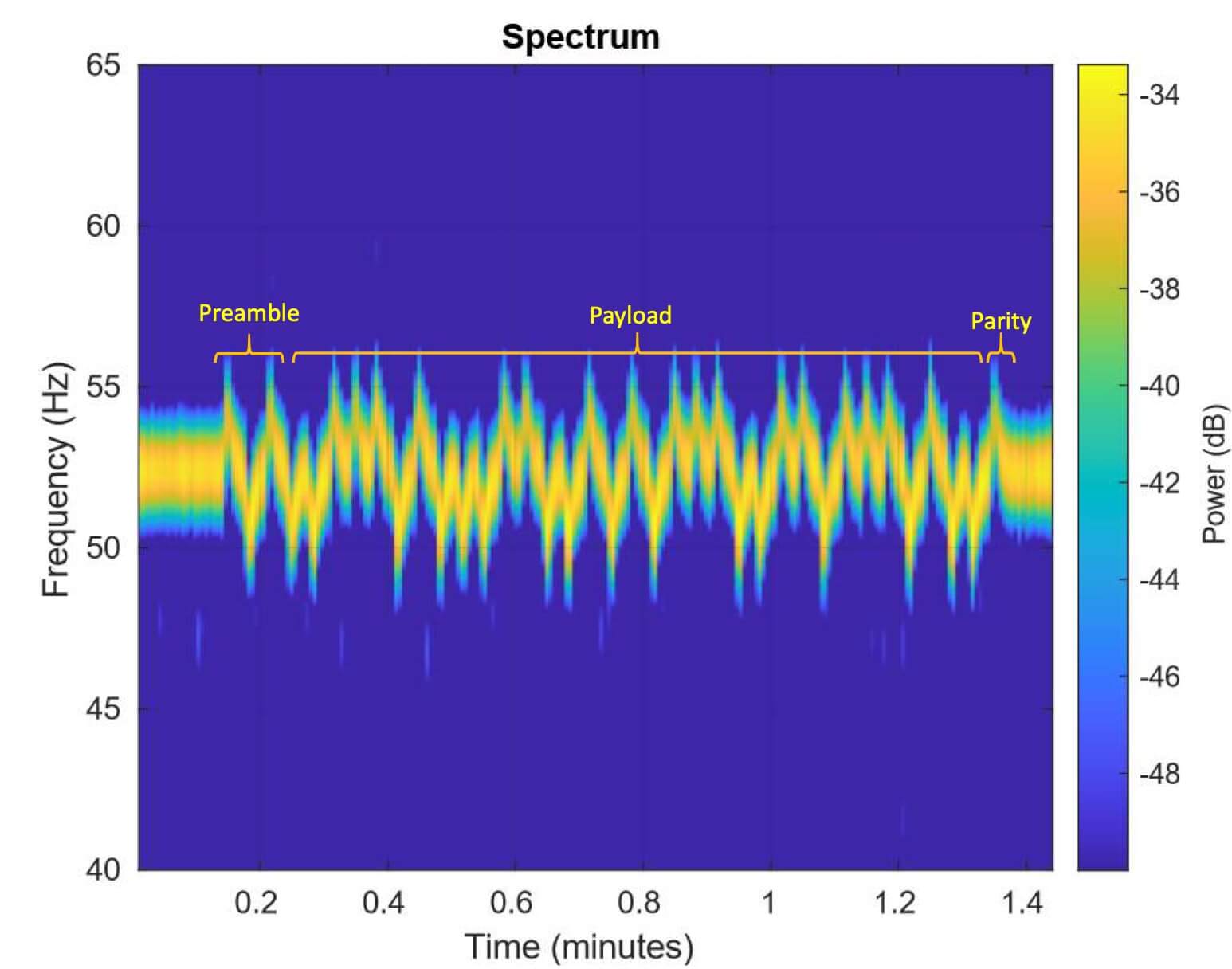
The researchers noted that while the method does result in reliable transmission of small packets of data to a phone that's up to 1.5 meters away from the PC, the speed is painfully slow. The case fan seemed to be the most effective source of vibrations, while the CPU fan was the least effective.
Real-life hackers may never consider using this technique due to its speed limitations, however the Israeli researchers headed by Dr. Mordechai Guri have tested several other attack methods that are significantly more effective. Examples include siphoning data from a computer using magnetic fields, listening for the sounds of a mechanical hard drive, and manipulating the screen brightness of a PC to achieve data transfer speeds that are orders of magnitude faster than AiR-ViBeR.
The most impressive effort so far is a variation of the classic LCD TEMPEST attack that can essentially reveal a grayscale image of what's on your screen.
https://www.techspot.com/news/84874-israeli-researchers-show-you-can-steal-data-pc.html