Why it matters: Due to the critical information they hold and process, air-gapped computers – usually found in government, banking, enterprise, industrial and military setups – operate in tightly controlled environments, cut-off from the internet and under strict supervision. While such security measures make them more difficult to hack, several covert channels have been explored in the past that use the computer's sound, heat, and even HDD activity indicators to siphon encoded data. The latest attempt involves sneakily changing a monitor's brightness which is then captured via video stream with a surveillance camera and then decoded through image processing.
Researchers have been able to extract data from a computer by simply changing its screen brightness levels as part of a new optical covert channel that relies on the limitations of human vision. Dr. Mordechai Guri, head of the cybersecurity research center at Israel's Ben Gurion University, conducted the research along with two fellow academics, reports The Hacker News.
Although the target machine doesn't need network connectivity or physical access for communicating the data, it does need to be infected with malware first, which encodes the sensitive information as "a stream of bytes" and then modulates it on the screen by making small changes in its brightness, invisible to the human eye.
The compromised monitor is then recorded by a video camera, which attackers can access and decode through image processing techniques. "This covert channel is invisible and it works even while the user is working on the computer." noted the researchers.
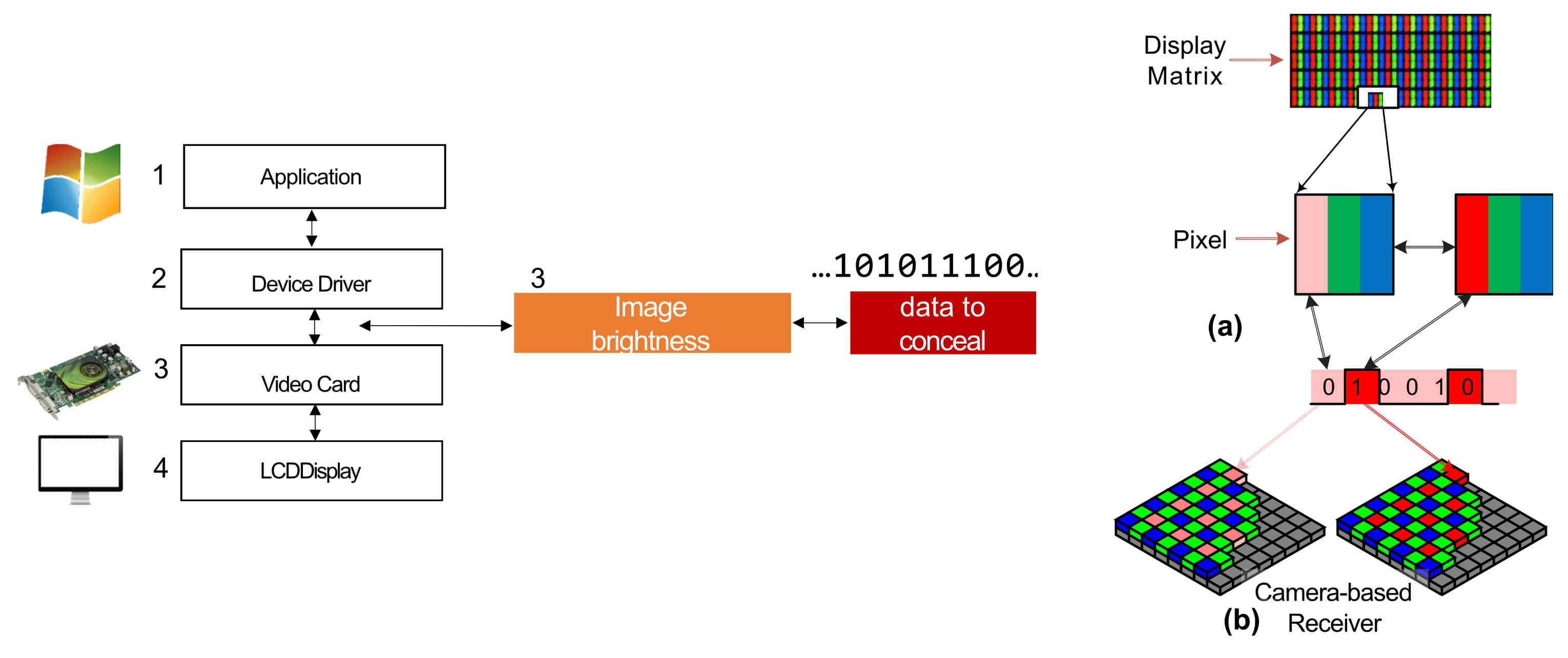
Using display-to-camera communication, the screen is modulated with a series of 1s and 0s, which the researchers were able to reconstruct with a 0% error rate. For their experiment, they used a security camera, webcam and a smartphone at varying distances from the target PC and were able to achieve a maximum speed of 10 bits/second.
In the video above, a PC display transmits the text of "Winnie-the-Pooh" story as nothing unusual seems to happen in the side of the user since the changes are "relatively small and occur fast, up to the screen refresh rate," with the overall color change being invisible to the naked eye.
As countermeasures for this type of attack, the researchers suggest implementing a strict policy on using cameras within the premises of air-gapped systems. Given that similar security measures are already taken at such places, they also suggest using a polarized film on the screen that would present a clear view to users but cameras at a distance would see a darkened display.
"Detection countermeasures may include monitoring of the sensitive computer for the presence of suspicious display anomalies at runtime," they add, but since such measures can be evaded by rootkits, a trusted alternative can be achieved by "taking videos of the computers display and searching for hidden brightness change patterns."
