What just happened? As ransomware gangs go, none are as well-known or notorious as LockBit. But the most prolific ransomware group in the world has just had its website taken over and operations disrupted by law enforcement agencies from 12 countries in a joint operation.

LockBit's website is currently showing a banner that states it is under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force named Operation Cronos.
In addition to the Europol logo and the US and UK flags, the banner shows the other law enforcement agencies involved are from Australia, Canada, Germany, Sweden, Finland, the Netherlands, Japan, France, and Switzerland.
An NCA spokesperson and a US Department of Justice spokesperson confirmed that the agencies had disrupted the gang and said the operation was "ongoing and developing."
LockBit has been behind over 1,700 attacks on organizations in the United States from virtually every sector, from government and financial to transport, healthcare, and education. LockBit even claimed responsibility for an attack on a Chicago children's hospital earlier this month, demanding an $800,000 ransom from the nonprofit.
Internationally, LockBit has caused chaos by hitting the Port of Lisbon, the UK's Royal Mail service, Foxconn's Mexico facility, and the Italian Revenue Service in recent years. There was also the case of the ransomware being used against a UK fencing company last year (that still ran Windows 7), compromising sensitive military data.
LockBit was one of the first to offer ransomware-as-a-service (RaaS) to other criminals, who must send the gang part of the ransomware payments taken from victims. Since resurfacing in late 2019, researchers at Recorded Future have attributed nearly 2,300 attacks to the group, writes The Record. The second most prolific group, Conti, has been linked to 883 attacks.
A security advisory issued by an international coalition last year revealed that organizations had paid around $91 million to LockBit criminals since January 5, 2020. It said LockBit was one of the most prominent and dangerous ransomware threats in the world today.
BleepingComputer writes that LockBitSupp, the threat actor who runs the LockBit operation, has updated his account on the Tox messaging service to show a message stating that the FBI breached the ransomware operation's servers using a PHP exploit.
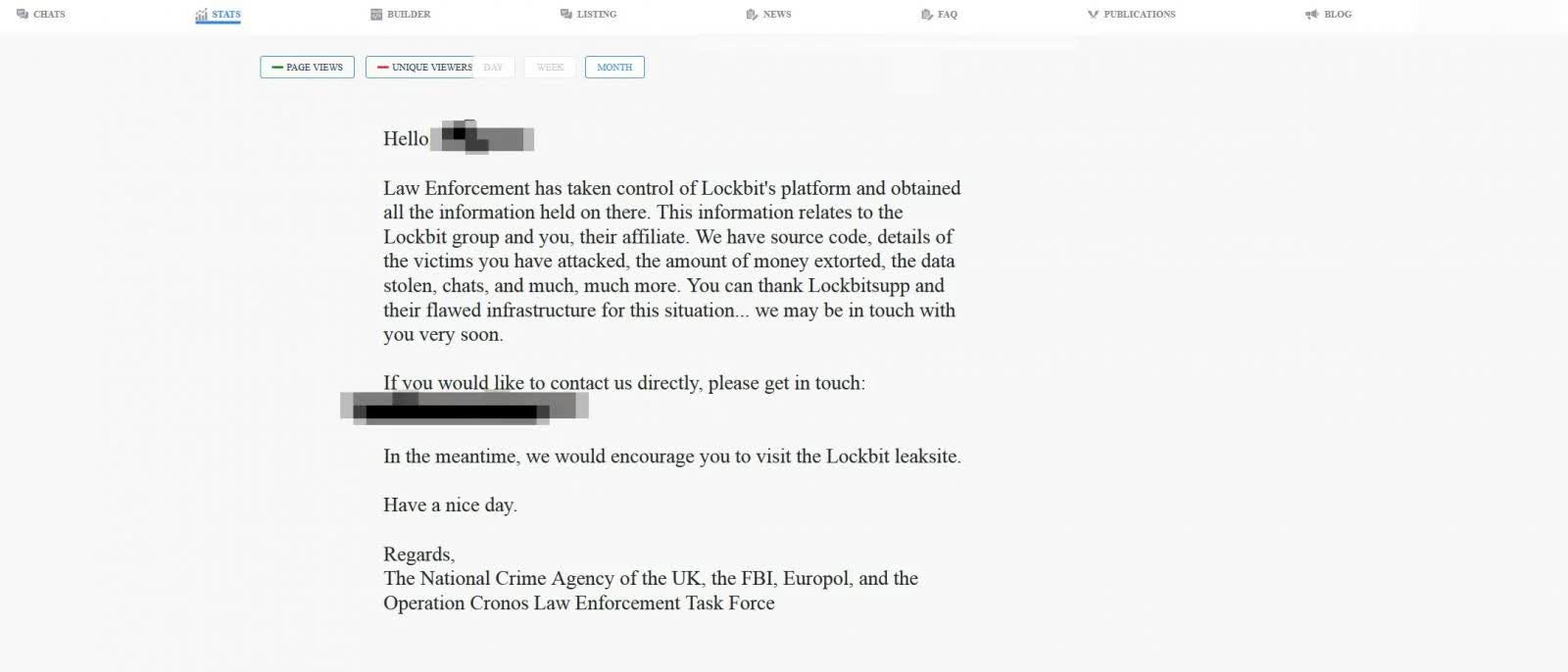
LockBit's affiliate panel has also been taken down. It shows a message from law enforcement stating that LockBit's source code, chats, and victim information were also seized.
"Law Enforcement has taken control of Lockbit's platform and obtained all the information held on there. This information relates to the Lockbit group and you, their affiliate. We have source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much, much more," the message states.
"You can thank Lockbitsupp and their flawed infrastructure for this situation [...] we may be in touch with you very soon. Have a nice day. Regards, The National Crime Agency of the UK, the FBI, Europol, and the Operation Cronos Law Enforcement Task Force."