What do Home Depot and Iran’s nuclear ambitions have in common? Both were on the receiving end of malicious code that infiltrated their systems via suppliers.
We’ve all heard the story about how Stuxnet was allegedly created as part of a joint effort by the United States and Israel to slow down Iran’s nuclear program. Because the Iranian targets were not connected to the Internet, most assumed that Stuxnet spread via USB drive but that’s no longer believed to be the case.
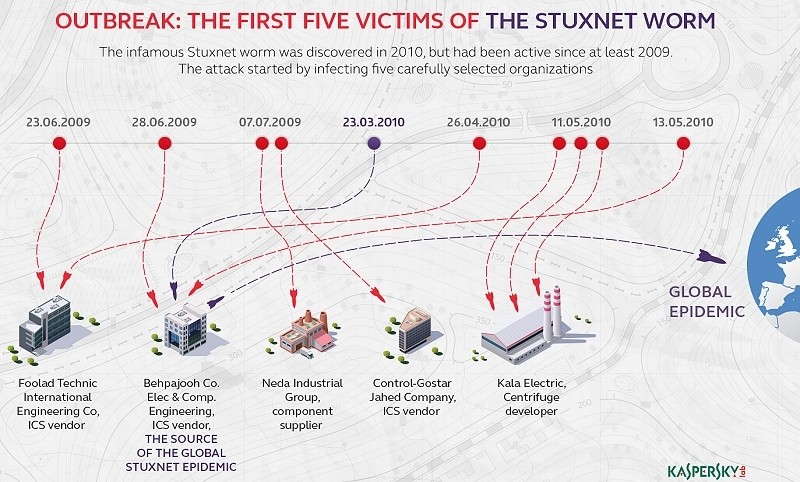
A new book on the matter, Countdown to Zero Day, claims the code first infected five vendors that supplied components used in Iran’s nuclear program. Those companies are believed to be Foolad Technic Engineering Co., Behpajooh Co. Elec & Comp. Engineering, Neda Industrial Group, Control-Gostar Jahed Company and Kala Electric.
The attackers expected these organizations would at some point supply components to Iran for its nuclear program and of courses, they were spot on.
What the coders didn’t count on, however, was the fact that Stuxnet would inadvertently infect other organizations and spread over the Internet due to specific design flaws.
As Kaspersky points out, one major question still remains – was Stuxnet a one-off project or are there other similar pieces of malware out in the wild that have yet to be discovered? Those answers will likely come over time.
https://www.techspot.com/news/58821-stuxnet-worm-found-way-iran-nuclear-facilities-five.html