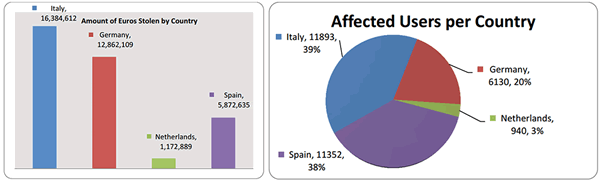
A sophisticated, multi-layered trojan dubbed "Eurograbber" is estimated to be responsible for siphoning over €36 million -- or about $46.5 million -- from the bank accounts of unsuspecting Europeans. In a case study (pdf) performed by Versafe and Check Point Software Technologies, researchers reveal how the trojan works.
Eurograbber was the latest take on the infamous ZeuS trojan horse, a malware capable of monitoring online bank sessions and besting two-factor authentication through what amounts to clever programming and social engineering.
For a user to fall prey to Eurograbber, he or she must first be using a computer infected with the trojan. This was typically done by luring the user onto a malicious web page via a round of unfortunate web surfing or email phishing attempts. Once infected, the trojan would monitor that computer's web browser for banking sessions. When a user visited a banking site, Eurograbber would inject JavaScript and HTML markup into their browser, prompting the user for their phone number under the guise of a "banking software security upgrade". This is also the key to Eurograbber's ability to bypass two-factor authentication.
Since the source of the request would appear to be the banking website, unsuspecting users would unwittingly enter their phone number. Next, smartphone users would receive a bogus SMS text asking them to install what was supposedly a "free encryption software" app. Unfortunately, the .apk (Android) or .jad (BlackBerry) files the texts would link to were apps capable of intercepting texts from banks containing transaction authorization numbers. TANs are one-time authorization codes used by some banks to authorize financial transactions and, ironically, increase security.
Next, the user would be presented with instructions to complete the process, ensuring both their PC and mobile device were compromised. Once complete, the next time that user logged on to their bank's website, the trojan would automatically initiate a money transfer into a shell account under their banking session. These transactions would usually range anywhere from 500 to 250,000 Euros. Normally, the user would receive a SMS alert containing a one-time use TAN in order to authorize the transfer, but the smartphone's trojan would silently intercept the SMS, collect its TAN and authorize the transaction itself -- the owner wouldn't have a clue until they noticed money missing from their account.
Readers interested in learning more about Eurograbber should check out this detailed report. (pdf).