Microsoft announced on Wednesday that malware writers are creating malicious applications with a similar name, look and feel to the company's legitimate security software (Microsoft Security Essentials) – a popular and long-used method of preying on inexperienced users. The fake antivirus is called "Security Essentials 2010" and contains the Trojan Win32/Fakeinit.

Once installed, the malware downloads and installs a fake scanner that monitors processes and terminates ones it doesn't like, claiming they are infected. It also lowers some security settings in the registry, and changes the desktop background to display the warning seen below while modifying the registry to prevent the wallpaper from being altered.
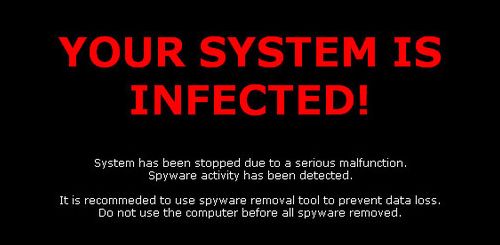
Furthermore, it downloads and installs Win32/Alureon and another Layered Service Provider component, which monitors TCP traffic sent by Web browsers and blocks certain domains, instead displaying this message. Naturally, the malware also requests that users pay for a subscription to use a "full version" of the software.
If you've been duped by "Security Essentials 2010," Microsoft's legitimate antivirus is available for free and can clean your system. Grab your download: Windows XP 32-bit, Windows Vista/7 32-bit, Windows Vista/7 64-bit. If you need further assistance, feel free to swing by TechSpot's Virus and Malware Removal forum.