The latest quarterly report from the U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) reveals that control systems at two different power plants in the US were found infected with malware last year. The organization didn't name which plants were hit and there is no indication if any equipment damage or personal injuries occurred as a result of the infections.
The attacks were spread using traditional USB drives that were plugged into critical power generation equipment. In fact, one of the infections was discovered after an employee had trouble with a USB port and called IT for assistance. The IT employee ran an updated virus scan on the system and found three positive hits. One sample was reportedly linked to known sophisticated malware.
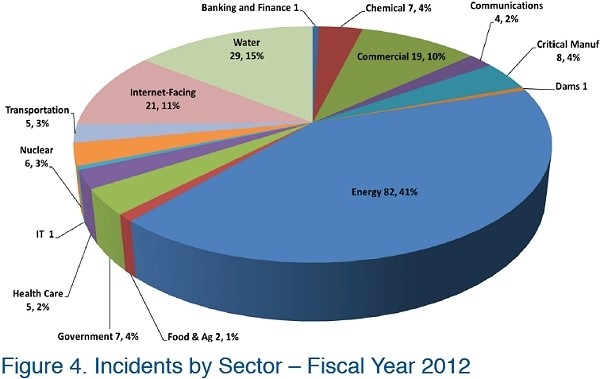
Judging by wording in the article, it doesn't sound like the control systems use any antivirus software at all. The ICS-CERT noted that while the implementation of an antivirus solution presents some challenges in a control system environment, it could have been effective in identifying both the common and the sophisticated malware.
Furthermore, the control workstation wasn't using any sort of backup solution which meant that if things had taken a turn for the worse, it would have taken a very long time to clean up the system and restore it to its intended state.
The newsletter says the other infection spread to 10 different computers responsible for controlling a turbine system. The report notes that the infection resulted in downtime for the impacted systems, which in turn delayed the plant restart by about three weeks.