Remember when Macs were touted as virtually inmune to viruses? More than a testament to the platform's security, there was a time Apple was such a small player in terms of market share that the devious minds that created this stuff just didn't bother. Those times have changed.
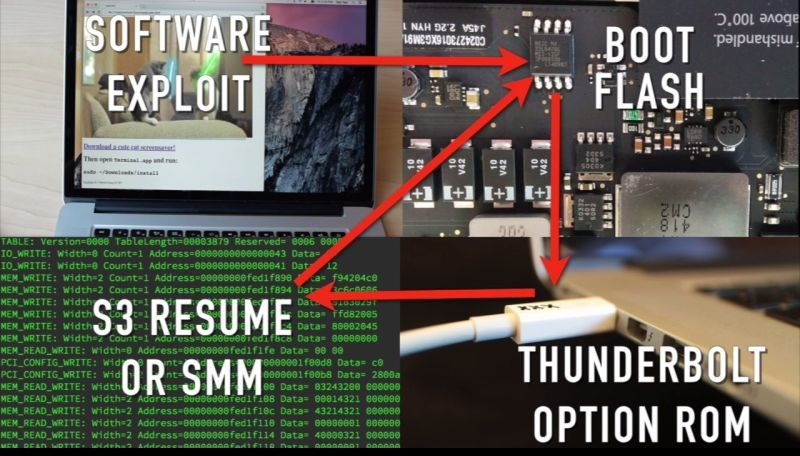
Researchers at LegbaCore, a firmware security consultancy company, and Two Sigma Investments have found that several known vulnerabilities affecting the firmware of all the top PC makers are also present in Macs. Their proof of concept code can't be detected by any current security scanner and can travel between machines by infecting what's known as the option ROM on peripheral devices. They used an Apple Thunderbolt to Gigabit Ethernet adapter to demonstrate how the malware can spread undetected, but an attacker could also infect the option ROM on an external SSD or on a RAID controller.
No security products currently check the option ROM on adapters and other peripherals, making it easy for attackers to spread their malware past the initial infection, which could be delivered via a phishing email and malicious web site. Moreover, most standard computer security programs don't check the machine's firmware, which makes it an attractive place to hide malware like this. Once it's in, the only way to remove it is to re-flash the chip that contains the firmware.
The researchers will be discussing other details about the attack, which they dubbed Thunderstrike 2, on August 6 at the Black Hat security conference in Las Vegas.The team has already notified Apple of the five vulnerabilities they discovered. One of them has now been patched, another partially so, but three are still open to potential attack.