Hard disk drives (HDD) have not yet gone the way of the horse and buggy, but with the rise in popularity of the solid-state drive (SSD), it could only be a matter of time before SSDs become the standard and HDDs are phased out. This shift is entirely understandable considering the speed and reliability advantages that solid-state drives offer, not to mention the recent reductions in price.
However, researchers at Carnegie Mellon University have discovered a flaw in SSD design that makes them vulnerable to a particular type of attack that can cause premature failure and data corruption. The details of the flaw are highly technical, but I will attempt to make some sense of it here without getting too convoluted.
Apparently, the problem only applies to multi-level cell (MLC) drives. Single-level cells (SLC) are not vulnerable, but since MLC SSDs have become more popular because of their speed, the risk applies to many more devices. While the study did not address triple-level cell (TLC) SSDs, ExtremeTech points out that TLCs are likely vulnerable since they use the same type of multi-stage programming cycle as MLCs.
The vulnerability comes from how MLCs are programmed. Unlike single-level cell SSDs, MLC drives write data into a buffer from the flash cell rather than from the SSD's flash controller. By intercepting this process, an attacker can corrupt the data being written. The obvious result is data corruption in stored memory, but it can also cause damage to the SDD, reducing its lifespan.
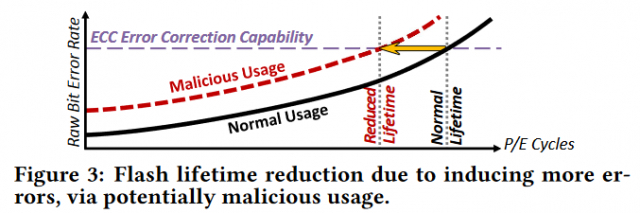
This explanation is highly simplified, but if you are fluent in technical jargon, you can read the researchers' full paper titled "Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques" at Semantic Scholar.
Resolving the problem is a more straightforward affair. Manufacturers would simply have to run data through the flash controller instead, just like with SLC. However, this increases latency by about 5 percent, which somewhat defeats one of the main advantages MLC has over SLC drives.
If Carnegie Mellon has figured this out, hackers assuredly have as well. If they had not already known about this flaw, they do now. We have yet to see a reported attack that has exploited this vulnerability, and certainly, SSD manufacturers are already at work trying to find a way to plug the hole without compromising speed.
Even if they do figure out how to fix the flaw in new drives, what of the drives already in consumer devices? Is there a software fix for this issue? Are there virus definitions that can be written to detect if a program or app is written to exploit this vulnerability? If you are a security expert, please share your thoughts in the comments.
