You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
[Closed] Possible fake AVG and Security Shield virus
- Thread starter dover1982
- Start date
- Status
- Not open for further replies.
Jay Pfoutz
Posts: 4,279 +49
Jay Pfoutz
Posts: 4,279 +49
Back to Normal Mode, if you can....
Kaspersky Security Scan (KSS)
The Kaspersky Security Scan is a scanning only tool, that searches for active infections such as rootkits, trojans, viruses, etc.
Please download the Kaspersky Security Scan from Kaspersky's Official Link and save it to your Desktop.
Kaspersky Security Scan (KSS)
The Kaspersky Security Scan is a scanning only tool, that searches for active infections such as rootkits, trojans, viruses, etc.
Please download the Kaspersky Security Scan from Kaspersky's Official Link and save it to your Desktop.
- Double-click on the downloaded item. It will quickly download the latest version of KSS and then launch the installer. Please navigate through the installer.
- After it finishes install, it will place an icon on your Desktop and launch itself.
- In the Kaspersky Security Scan interface, choose full scan at the bottom:

- Once it finishes, it will show the report. Click on the Details button, and it will launch a HTML page.
- You have two options - either A. Upload the HTML report here, file located at { C:/ProgramData/Kaspersky%20Lab/KSS2/DataRoot/HtmlReport/index.html } (Copy and paste the file path into the Address box in the Upload window), or B. Copy and paste all of the results in your next reply.
Computer protection (0)
Information about anti-virus software and firewalls installed on the computer.
Malware (0)
Information about malware detected on the computer.
Vulnerabilities (4)
Information about applications and operating system components in which vulnerabilities have been detected.
Other issues (12)
Information about vulnerabilities associated with the settings of installed applications and the operating system.
Information about anti-virus software and firewalls installed on the computer.
Malware (0)
Information about malware detected on the computer.
Vulnerabilities (4)
Information about applications and operating system components in which vulnerabilities have been detected.
- C:\Program Files (x86)\iTunes\iTunes.exe
- C:\Program Files (x86)\Java\jre7\bin\java.exe
- C:\Program Files (x86)\QuickTime\QuickTimePlayer.exe
- C:\Windows\SysWOW64\Macromed\Flash\NPSWF32.dll
Other issues (12)
Information about vulnerabilities associated with the settings of installed applications and the operating system.
- "Autorun from hard drives is allowed"
- "Autorun from network drives is enabled"
- "CD/DVD autorun is enabled"
- "Removable media autorun is enabled"
- "Microsoft Internet Explorer: clear history of typed URLs"
- "Microsoft Internet Explorer - disable caching data received via protected channel"
- "Microsoft Internet Explorer: disable sending error reports"
- "Microsoft Internet Explorer: delete cookies"
- "Microsoft Internet Explorer: clear list of pop-up blocker exceptions"
- "Microsoft Internet Explorer: enable cache autocleanup on browser closing"
- "Windows Explorer: display of known file types extensions is disabled"
- "Microsoft Internet Explorer: start page reset"
Jay Pfoutz
Posts: 4,279 +49
Any more issues?
We need to know any other issues that are plaguing your computer. Kindly give a summary so we know how to continue from here.
Many of the things to note for us would be:
We need to know any other issues that are plaguing your computer. Kindly give a summary so we know how to continue from here.
Many of the things to note for us would be:
- Slow computer
- Error messages
- Fake antivirus alerts or the icon in the system tray
- svchost.exe running at 100%
- System crashes or blue screen of death
1) Since the Kaspersky scan came up clean, can I now suspect the AVG Identity Protection is legit and not a virus?
2) I mentioned in the original post that I had a warning that said my User Account Control was turned off. The pop up in the lower right hand corner is not there anymore however I did go into the Control Panel and it is showed as off still. I honestly don't know how it got turned off and whether or not it should be or shouldn't be off, so I'd like to know what to do about that?
3) I also mentioned in the OP that one of the Resident Shield findings, that seemed to have been cleaned or removed successfully but reads "May be infected by unkown virus Win32/DH{LgMPNg}". It makes it sound like I still have a virus and don't know what to think about that object. I'll attach a photo....

2) I mentioned in the original post that I had a warning that said my User Account Control was turned off. The pop up in the lower right hand corner is not there anymore however I did go into the Control Panel and it is showed as off still. I honestly don't know how it got turned off and whether or not it should be or shouldn't be off, so I'd like to know what to do about that?
3) I also mentioned in the OP that one of the Resident Shield findings, that seemed to have been cleaned or removed successfully but reads "May be infected by unkown virus Win32/DH{LgMPNg}". It makes it sound like I still have a virus and don't know what to think about that object. I'll attach a photo....
Jay Pfoutz
Posts: 4,279 +49
Was that just recently infected?
Read this for AVG Identity Protection: http://www.avg.com/us-en/faq.pnuid-faq_v3_avg_identity_protection
Read this for AVG Identity Protection: http://www.avg.com/us-en/faq.pnuid-faq_v3_avg_identity_protection
Was that just recently infected?
If your referring to the objects found by Resident Shield, those all were found with the initial problems I had and which I described in the OP.
Today I've had a ton of problems with the computer and new alerts. It was doing pretty good until today. The Security Shield problems were gone, and one good thing today was that the AVG ID Pro alert was legit so I moved the file to the vault. Immediately after I did that ID Pro said it found malware which I guess might've had to do with file ID Pro just moved to the vault? Anyways I moved that too to the vault.
But as for the new problems that have occurred today...
- I've had a bunch of detections from Resident Shield. Most of them, except one, are an object that it repeatedly detects for some reason. I cleaned the first couple it found and each detection alert after that popped up as it they were already cleaned anyways. It also says that that file is "white-listed (critical/system file that should not be removed)". The other file that Resident Shield found was an object that was already found and cleaned and is listed in the photo I uploaded in post #32. I'll post a photo below...
- Immediately after those detections I noticed that AVG had a alert symbol on it and once I was opened it up it said that AVG's Firewall was "off" and that ID Pro was "disabled". I don't know how that happened but I thought I should let you know, I simply clicked "fix all" and that problem was solved.
- I've had a couple redirects to some random search page when using Internet Explorer. Doesn't seem to effect FireFox.
- ID Pro found another malware object and I moved that to the vault. I'll post a photo of pop up after I removed and in case it helps I'll also post a photo of the details.

Jay Pfoutz
Posts: 4,279 +49
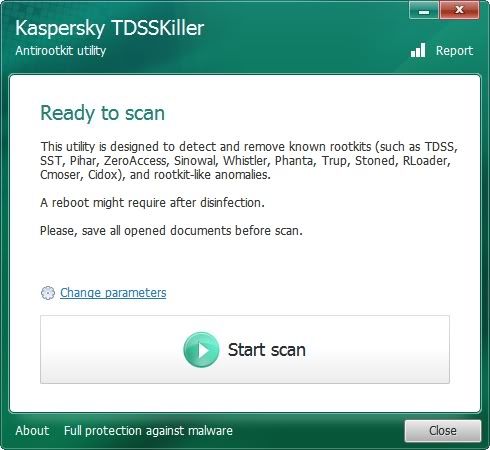
Please download and run TDSSKiller to your desktop as outlined below:
Doubleclick on TDSSKiller.exe to run the application, then click on Change parameters.
For Windows XP, double-click to start.
For Vista or Windows 7, do a right-click on the program, select Run as Administrator to start, & when prompted Allow to run.
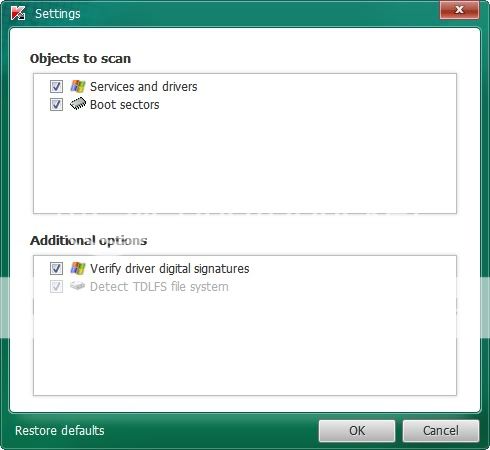
-------------------------
Check the boxes beside Verify Driver Digital Signature and Detect TDLFS file system, then click OK.
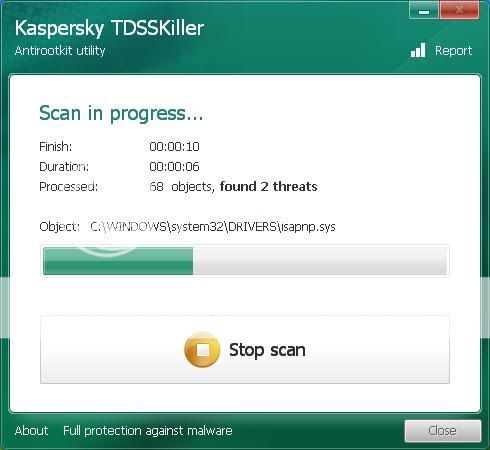
------------------------
Click the Start Scan button.
-----------------------
If a suspicious object is detected, the default action will be Skip, click on Continue
If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose
Skip and click on Continue
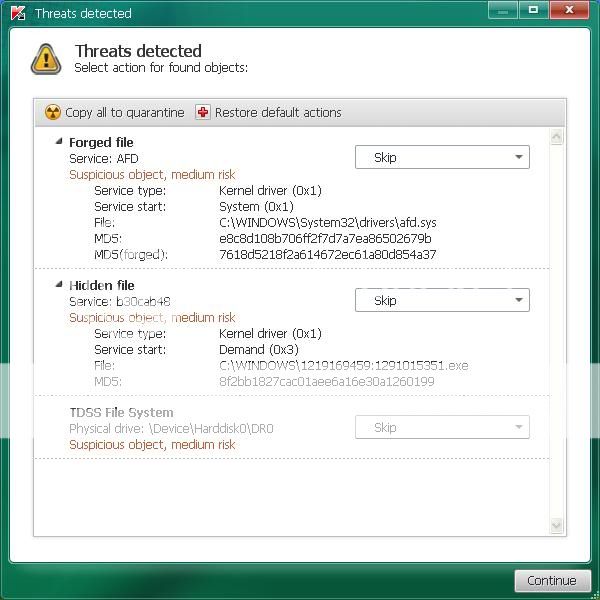
----------------------
If malicious objects are found, they will show in the Scan results and offer three (3) options.
Ensure Cure is selected, then click Continue => Reboot now to finish the cleaning process.
Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed.
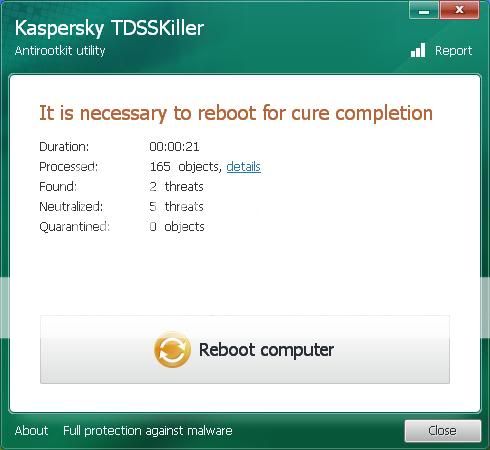
--------------------
A report will be created in your root directory, (usually C:\ folder) in the form of "TDSSKiller.[Version]_[Date]_[Time]_log.txt". Please copy and paste its contents on your next reply.
Sometimes these logs can be very large, in that case please attach it or zip it up and attach it.
-------------------
Here's a summary of what to do if you would like to print it out:
If a suspicious object is detected, the default action will be Skip, click on Continue
If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose
Skip and click on Continue
If malicious objects are found, they will show in the Scan results and offer three (3) options.
Ensure Cure is selected, then click Continue => Reboot now to finish the cleaning process.
Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed.
aswMBR scan
Please download aswMBR from here
Note: Do not take action against any **Rootkit** entries until I have reviewed the log. Often there are false positives
Doubleclick on TDSSKiller.exe to run the application, then click on Change parameters.
For Windows XP, double-click to start.
For Vista or Windows 7, do a right-click on the program, select Run as Administrator to start, & when prompted Allow to run.

-------------------------
Check the boxes beside Verify Driver Digital Signature and Detect TDLFS file system, then click OK.

------------------------
Click the Start Scan button.

-----------------------
If a suspicious object is detected, the default action will be Skip, click on Continue
If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose
Skip and click on Continue

----------------------
If malicious objects are found, they will show in the Scan results and offer three (3) options.
Ensure Cure is selected, then click Continue => Reboot now to finish the cleaning process.
Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed.

--------------------
A report will be created in your root directory, (usually C:\ folder) in the form of "TDSSKiller.[Version]_[Date]_[Time]_log.txt". Please copy and paste its contents on your next reply.
Sometimes these logs can be very large, in that case please attach it or zip it up and attach it.
-------------------
Here's a summary of what to do if you would like to print it out:
If a suspicious object is detected, the default action will be Skip, click on Continue
If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose
Skip and click on Continue
If malicious objects are found, they will show in the Scan results and offer three (3) options.
Ensure Cure is selected, then click Continue => Reboot now to finish the cleaning process.
Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed.
aswMBR scan
Please download aswMBR from here
- Save aswMBR.exe to your Desktop
- Double click aswMBR.exe to run it
- Click the Scan button to start the scan as illustrated below

Note: Do not take action against any **Rootkit** entries until I have reviewed the log. Often there are false positives
- Once the scan finishes click Save log to save the log to your Desktop
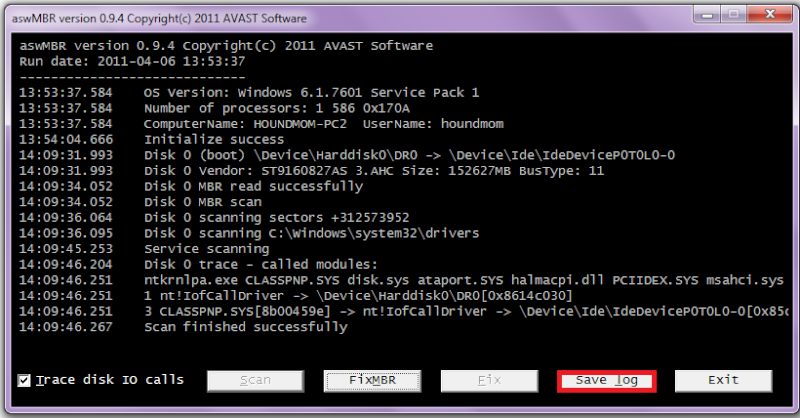
- Copy and paste the contents of aswMBR.txt back here for review
Jay Pfoutz
Posts: 4,279 +49
Try again after trying out this tool:
RKill by Grinler
Version 1
Version 2
RKill by Grinler
Version 1
Version 2
- Download Version 1.
- Save it to your Desktop.
- Double click the RKill desktop icon.
If you are using Vista please right click and run as Admin! - A black screen will briefly flash indicating a successful run.
- If this does not occur please delete that application and download Version 2.
- Continue process until the tool runs.
- If the tool does not run from any of the links tell me about it.
I know you didn't say anything about a report but it did produce one and I'll post it below...
Rkill 2.3.1 by Lawrence Abrams (Grinler)
http://www.bleepingcomputer.com/
Copyright 2008-2012 BleepingComputer.com
More Information about Rkill can be found at this link:
http://www.bleepingcomputer.com/forums/topic308364.html
Program started at: 08/22/2012 05:07:49 PM in x64 mode.
Windows Version: Windows Vista Service Pack 2
Checking for Windows services to stop.
* No malware services found to stop.
Checking for processes to terminate.
* C:\Windows\MHotKey.exe (PID: 3704) [WD-HEUR]
* C:\Windows\ChiFuncExt.exe (PID: 3552) [WD-HEUR]
* C:\Windows\CNYHKey.exe (PID: 4260) [WD-HEUR]
* C:\Windows\ModLedKey.exe (PID: 4616) [WD-HEUR]
4 proccesses terminated!
Possibly Patched Files.
* C:\Windows\system32\services.exe
Checking Registry for malware related settings.
* No issues found in the Registry.
Resetting .EXE, .COM, & .BAT associations in the Windows Registry.
* HKLM\Software\Classes\exefile\shell\open\command\\IsolatedCommand was changed. It was reset to "%1" %*!
* HKLM\Software\Classes\exefile\shell\runas\command\\IsolatedCommand was changed. It was reset to "%1" %*!
* HKLM\Software\Classes\.com "@" has been changed to ComFile!
* HKLM\Software\Classes\.com "@" was reset to comfile!
Performing miscellaneous checks.
* Windows Defender Disabled
[HKLM\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware" = dword:00000001
* ALERT: ZEROACCESS rootkit symptoms found!
* HKEY_CLASSES_ROOT\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32 [ZA Reg Hijack]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\ [ZA Dir]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\@ [ZA File]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\ [ZA Dir]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\00000004.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\201d3dde [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\n [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\00000004.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\00000008.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\000000cb.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000000.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000032.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000064.@ [ZA File]
* C:\Windows\assembly\GAC_32\Desktop.ini [ZA File]
* C:\Windows\assembly\GAC_64\Desktop.ini [ZA File]
Checking Windows Service Integrity:
* No issues found.
Searching for Missing Digital Signatures:
* C:\Windows\System32\services.exe [NoSig]
+-> C:\Windows\ERDNT\cache64\services.exe : 384,512 : 04/11/2009 00:10 AM : 934e0b7d77ff78c18d9f8891221b6de3 [Pos Repl]
+-> C:\Windows\SysWOW64\services.exe : 279,552 : 04/11/2009 00:27 AM : d4e6d91c1349b7bfb3599a6ada56851b [Pos Repl]
+-> C:\Windows\winsxs\amd64_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_2b7e5beb85a67240\services.exe : 384,512 : 01/20/2008 09:49 PM : dfac660f0f139276cc9299812de42719 [Pos Repl]
+-> C:\Windows\winsxs\amd64_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_2d69d4f782c83d8c\services.exe : 384,512 : 04/11/2009 09:10 AM : 934e0b7d77ff78c18d9f8891221b6de3 [Pos Repl]
+-> C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_cf5fc067cd49010a\services.exe : 279,040 : 01/20/2008 09:50 PM : 2b336ab6286d6c81fa02cbab914e3c6c [Pos Repl]
+-> C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_d14b3973ca6acc56\services.exe : 279,552 : 04/11/2009 09:27 AM : d4e6d91c1349b7bfb3599a6ada56851b [Pos Repl]
Program finished at: 08/22/2012 05:09:03 PM
Execution time: 0 hours(s), 1 minute(s), and 13 seconds(s)
Rkill 2.3.1 by Lawrence Abrams (Grinler)
http://www.bleepingcomputer.com/
Copyright 2008-2012 BleepingComputer.com
More Information about Rkill can be found at this link:
http://www.bleepingcomputer.com/forums/topic308364.html
Program started at: 08/22/2012 05:07:49 PM in x64 mode.
Windows Version: Windows Vista Service Pack 2
Checking for Windows services to stop.
* No malware services found to stop.
Checking for processes to terminate.
* C:\Windows\MHotKey.exe (PID: 3704) [WD-HEUR]
* C:\Windows\ChiFuncExt.exe (PID: 3552) [WD-HEUR]
* C:\Windows\CNYHKey.exe (PID: 4260) [WD-HEUR]
* C:\Windows\ModLedKey.exe (PID: 4616) [WD-HEUR]
4 proccesses terminated!
Possibly Patched Files.
* C:\Windows\system32\services.exe
Checking Registry for malware related settings.
* No issues found in the Registry.
Resetting .EXE, .COM, & .BAT associations in the Windows Registry.
* HKLM\Software\Classes\exefile\shell\open\command\\IsolatedCommand was changed. It was reset to "%1" %*!
* HKLM\Software\Classes\exefile\shell\runas\command\\IsolatedCommand was changed. It was reset to "%1" %*!
* HKLM\Software\Classes\.com "@" has been changed to ComFile!
* HKLM\Software\Classes\.com "@" was reset to comfile!
Performing miscellaneous checks.
* Windows Defender Disabled
[HKLM\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware" = dword:00000001
* ALERT: ZEROACCESS rootkit symptoms found!
* HKEY_CLASSES_ROOT\CLSID\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InprocServer32 [ZA Reg Hijack]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\ [ZA Dir]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\@ [ZA File]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\ [ZA Dir]
* C:\Users\Mary\AppData\Local\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\00000004.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\L\201d3dde [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\n [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\ [ZA Dir]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\00000004.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\00000008.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\000000cb.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000000.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000032.@ [ZA File]
* C:\Windows\installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\80000064.@ [ZA File]
* C:\Windows\assembly\GAC_32\Desktop.ini [ZA File]
* C:\Windows\assembly\GAC_64\Desktop.ini [ZA File]
Checking Windows Service Integrity:
* No issues found.
Searching for Missing Digital Signatures:
* C:\Windows\System32\services.exe [NoSig]
+-> C:\Windows\ERDNT\cache64\services.exe : 384,512 : 04/11/2009 00:10 AM : 934e0b7d77ff78c18d9f8891221b6de3 [Pos Repl]
+-> C:\Windows\SysWOW64\services.exe : 279,552 : 04/11/2009 00:27 AM : d4e6d91c1349b7bfb3599a6ada56851b [Pos Repl]
+-> C:\Windows\winsxs\amd64_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_2b7e5beb85a67240\services.exe : 384,512 : 01/20/2008 09:49 PM : dfac660f0f139276cc9299812de42719 [Pos Repl]
+-> C:\Windows\winsxs\amd64_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_2d69d4f782c83d8c\services.exe : 384,512 : 04/11/2009 09:10 AM : 934e0b7d77ff78c18d9f8891221b6de3 [Pos Repl]
+-> C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_cf5fc067cd49010a\services.exe : 279,040 : 01/20/2008 09:50 PM : 2b336ab6286d6c81fa02cbab914e3c6c [Pos Repl]
+-> C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_d14b3973ca6acc56\services.exe : 279,552 : 04/11/2009 09:27 AM : d4e6d91c1349b7bfb3599a6ada56851b [Pos Repl]
Program finished at: 08/22/2012 05:09:03 PM
Execution time: 0 hours(s), 1 minute(s), and 13 seconds(s)
Jay Pfoutz
Posts: 4,279 +49
Download Farbar Recovery Scan Tool and save it to a flash drive.
Please make sure to download the 64-bit version.
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
Please make sure to download the 64-bit version.
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
- Restart the computer.
- As soon as the BIOS is loaded begin tapping the F8 key until Advanced Boot Options appears.
- Use the arrow keys to select the Repair your computer menu item.
- Choose your language settings, and then click Next.
- Select the operating system you want to repair, and then click Next.
- Select your user account and click Next.
- Insert the installation disc.
- Restart your computer.
- If prompted, press any key to start Windows from the installation disc. If your computer is not configured to start from a CD or DVD, check your BIOS settings.
- Click Repair your computer.
- Choose your language settings, and then click Next.
- Select the operating system you want to repair, and then click Next.
- Select your user account an click Next.
- Startup Repair
System Restore
Windows Complete PC Restore
Windows Memory Diagnostic Tool
Command Prompt
- Startup Repair
- Select Command Prompt
- In the command window type in notepad and press Enter.
- The notepad opens. Under File menu select Open.
- Select "Computer" and find your flash drive letter and close the notepad.
- In the command window type e:\frst64 and press Enter
Note: Replace letter e with the drive letter of your flash drive. - The tool will start to run.
- When the tool opens click Yes to the disclaimer.
- Place a check next to List Drivers MD5 as well as the default check marks that are already there (if necessary)
- Press Scan button. It will do its scan and save a log on your flash drive.
- Close out of the message after that, then type in the text services.exe in to the "Search:" text box. Then, press the Search file(s) button, just as below:

When done searching, FRST makes a log, Search.txt, on the C:\ drive or on your flash drive. - Type exit in the Command Prompt window and reboot the computer normally
- FRST will make a log (FRST.txt) on the flash drive and also the search.txt logfile, please copy and paste the logs in your reply.
Download Farbar Recovery Scan Tool and save it to a flash drive.
Please make sure to download the 64-bit version.
Plug the flashdrive into the infected PC.
Can I download Farbar to the flash drive from my infected PC or do I need to find another computer?
Jay Pfoutz
Posts: 4,279 +49
I cannot find an installation disc.
I have a problem accessing the Advanced Boot Options upon startup. I've tried pressing F8 a number of times, whether holding it down or pressing it repeatedly and neither works. I know that this particular issue is not a new problem because I tried this same thing a long time ago but pressing F8 failed to work. I also attempted pressing Delete to Enter Setup and F12 for Boot Menu which both of those failed to work also upon startup. Maybe it's a problem with my keyboard?
I have a problem accessing the Advanced Boot Options upon startup. I've tried pressing F8 a number of times, whether holding it down or pressing it repeatedly and neither works. I know that this particular issue is not a new problem because I tried this same thing a long time ago but pressing F8 failed to work. I also attempted pressing Delete to Enter Setup and F12 for Boot Menu which both of those failed to work also upon startup. Maybe it's a problem with my keyboard?
Jay Pfoutz
Posts: 4,279 +49
Possibly. Looks like you will need to create a system repair disc: http://windows.microsoft.com/is-IS/windows7/Create-a-system-repair-disc?SignedIn=1
By doing this, it will give us access to the Windows Recovery Environment. Let me know once done, please.
By doing this, it will give us access to the Windows Recovery Environment. Let me know once done, please.
Jay Pfoutz
Posts: 4,279 +49
I did not run Kaspersky but it popped up after apparently doing a scan and I figured I might as well post the results.
Computer protection (0)
Information about anti-virus software and firewalls installed on the computer.
Malware (7)
Information about malware detected on the computer.
Kaspersky recommends
Vulnerabilities (4)
Information about applications and operating system components in which vulnerabilities have been detected.
Other issues (12)
Information about vulnerabilities associated with the settings of installed applications and the operating system.
Computer protection (0)
Information about anti-virus software and firewalls installed on the computer.
Malware (7)
Information about malware detected on the computer.
Kaspersky recommends
- HEUR:Trojan.Win32.Generic
wmsng.dll
c:\Users\Mary\AppData\Roaming - HEUR:Backdoor.Win64.Generic
80000000.@
C:\Windows\Installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U - Trojan.Win32.Miner.dw
data0000.res
C:\Windows\Installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U\00000008.@/ - Backdoor.Win32.ZAccess.ycs
80000032.@
C:\Windows\Installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U - Backdoor.Win32.ZAccess.mbs
000000cb.@
C:\Windows\Installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U - Backdoor.Win32.ZAccess.ycu
80000064.@
C:\Windows\Installer\{8bf7e6e5-22a7-2d02-9ec4-ee60b2f264cd}\U - Virus.Win64.ZAccess.b
services.exe
C:\Windows\system32
Vulnerabilities (4)
Information about applications and operating system components in which vulnerabilities have been detected.
- C:\Program Files (x86)\iTunes\iTunes.exe
- C:\Program Files (x86)\Java\jre7\bin\java.exe
- C:\Program Files (x86)\QuickTime\QuickTimePlayer.exe
- C:\Windows\SysWOW64\Macromed\Flash\NPSWF32.dll
Other issues (12)
Information about vulnerabilities associated with the settings of installed applications and the operating system.
- "Autorun from hard drives is allowed"
- "Autorun from network drives is enabled"
- "CD/DVD autorun is enabled"
- "Removable media autorun is enabled"
- "Windows Explorer - show extensions of known file types"
- "Microsoft Internet Explorer - disable caching data received via protected channel"
- "Microsoft Internet Explorer: disable sending error reports"
- "Microsoft Internet Explorer: delete cookies"
- "Microsoft Internet Explorer: clear list of pop-up blocker exceptions"
- "Microsoft Internet Explorer: enable cache autocleanup on browser closing"
- "Windows Explorer: display of known file types extensions is disabled"
- "Microsoft Internet Explorer: start page reset"
Jay Pfoutz
Posts: 4,279 +49
Kaspersky Virus Removal Tool
The Kaspersky Virus Removal Tool is a scan-and-remove solution from Kaspersky that searches out the most common malware and attempts to remove it from your computer.
Please download the Kaspersky Virus Removal Tool from Kaspersky's Official Link and save it to your Desktop.
The Kaspersky Virus Removal Tool is a scan-and-remove solution from Kaspersky that searches out the most common malware and attempts to remove it from your computer.
Please download the Kaspersky Virus Removal Tool from Kaspersky's Official Link and save it to your Desktop.
- Double-click the Setup file to install it on your computer.
- Once it has installed, review and accept the agreement and press the Start button.
- You will presented with the main interface, but don't scan yet, click the options tab (gear icon):

- On the Scan Scope tab, make sure to checkmark all the options, except for the CD/DVD drive:

- On the Security Level tab, make sure to move the slider up denoting "Current Security Level: High":

- Now, go back to the Automatic Scan tab, and choose "Start Scanning". It may take several hours to complete. Please allow it to do so.
- Once done scanning, choose the Report tab (page icon), select Detected Threats tab on left, and choose Disinfect All:

- Then, choose Save. Also, in the Automatic Report tab, select Save:

- Please post the reports in your next reply.
- Once you exit, the tool should uninstall automatically.
Kaspersky has found some objects and has asked whether I want to "delete" or "skip" one in particular. The object is "Backdoor.Win32.ZAccess.xps". The option to quarantine is disabled. I tried to take a screenshot but apparently the snipping tool won't work with Kaspersky running. The scan has slowed down significantly after initially running quickly. I don't know if it's waiting for me to select an option for the object it found or not but it's estimated remaining time is 18 hours. It also seems stuck on one object which doesn't appear to be the apparent malicious one it found.
- Status
- Not open for further replies.
Similar threads
- Replies
- 1
- Views
- 354
- Replies
- 10
- Views
- 335
Latest posts
-
-
Researchers have unlocked the "Holy Grail" of memory technology
- user556 replied
-
Request to delete my account and data
- Alicization replied
-
TechSpot is dedicated to computer enthusiasts and power users.
Ask a question and give support.
Join the community here, it only takes a minute.