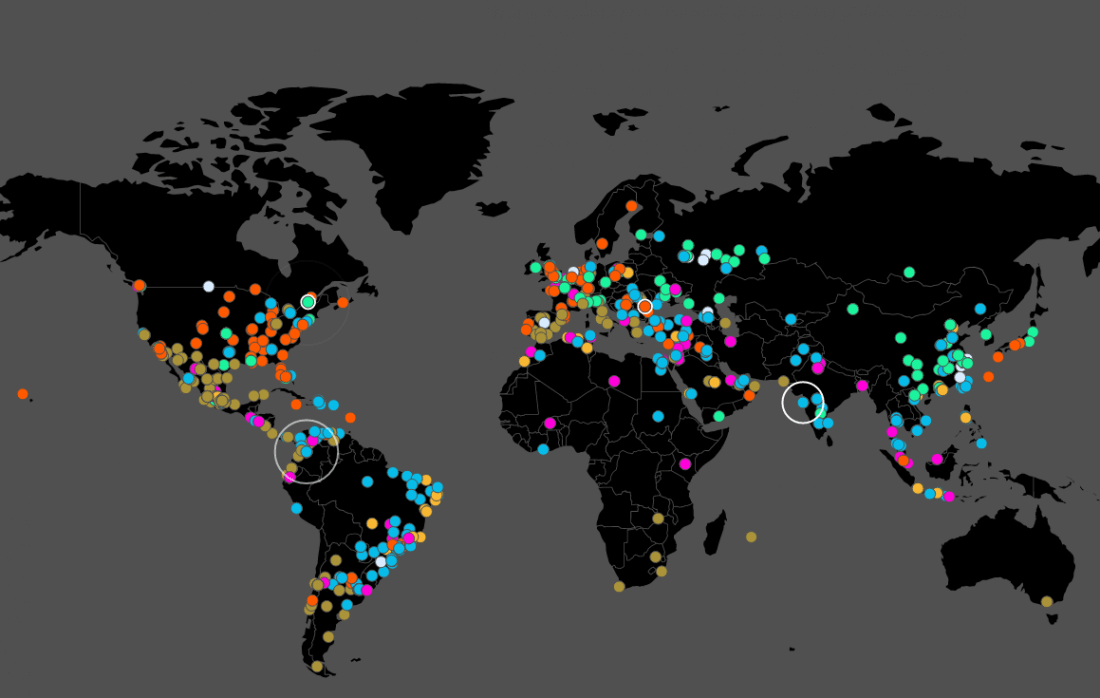
A new strain of ransomware is wrecking havoc all over the world, with hospitals across England and major companies in several countries reportedly affected. Security experts have identified the ransomware as a new strain of the WannaCry (also known as WanaCrypt0r and WCry) malware, and apparently its reach extends beyond the UK and Spain, into Russia, Taiwan, France, Japan, and more.
The malware leverages a Windows vulnerability known as EternalBlue that leaked last month when a group known as Shadow Brokers posted a bunch of hacking tools that allegedly belonged to the NSA. Microsoft issued a patch for the flaw in March, but apparently many organizations have failed to keep up.
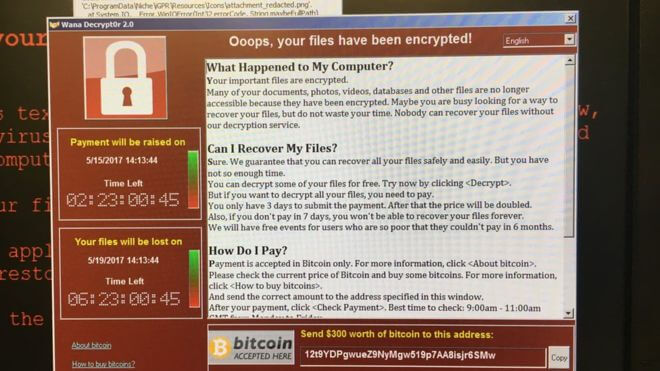
Among the first reported cases are the National Health Service hospitals and facilities around England, which experienced system failures and locked machines showing a ransom message demanding $300 worth of bitcoin. The NHS says said no private patient data has been stolen but some of its hospitals have postponed all non-urgent activity and new patients are being diverted to nearby healthcare facilities.
The malware has also hobbled the large telecom company Telefonica in Spain, as well as the natural gas company Gas Natural, and the electrical company Iberdrola.
Over in the US, FedEx has also confirmed it is experiencing “interference” with some of their Windows-based systems caused by malware. The company is reportedly shutting down its PCs and taking its ESX servers offline while it tries to deal with the ransomware.
"The impact of this global ransomware outbreak using NSA leaked tools demonstrates how susceptible our physical world is, not a country or a region but ALL OF US individually and collectively," Ralph Echemendia, a cyber security specialist known as the "The Ethical Hacker" told TechSpot. "This incident is just one of many that will continue to shape the way we evolve. The opposite of Physical is Virtual, but most don’t realize that virtual still means real. This is a very real and substantial attack on trust. Can we trust companies and governments to keep us safe. The answer is no."
It’s still unclear who is behind the attack but we’ll report when more information comes up.
Ransomware image credit: BBC
https://www.techspot.com/news/69300-massive-ransomware-attack-spreads-across-globe.html