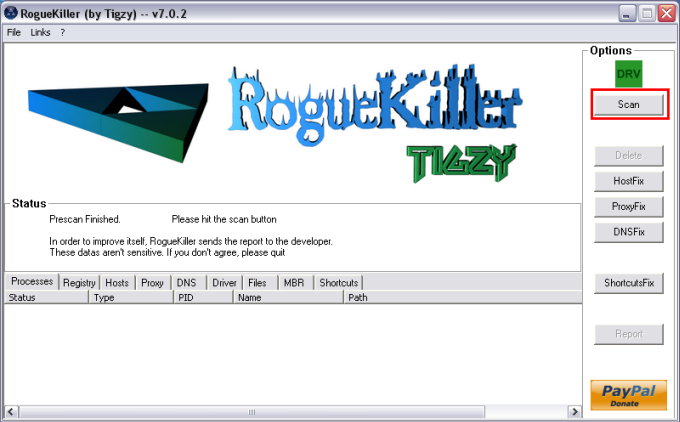
RogueKiller V8.1.1 [10/01/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback:
https://www.techspot.com/downloads/5562-roguekiller.html
Website:
http://tigzy.geekstogo.com/roguekiller.php
Blog:
http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7600 ) 32 bits version
Started in : Normal mode
User : Win7 [Admin rights]
Mode : Scan -- Date : 10/21/2012 07:08:10
¤¤¤ Bad processes : 32 ¤¤¤
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe -> KILLED [TermProc]
[SUSP PATH] doa2k8s.exe -- C:\Windows\System32\config\systemprofile\AppData\Roaming\doa2k8s.exe -> KILLED [TermProc]
[SUSP PATH] hotnomjyzoby.exe -- C:\ProgramData\hotnomjyzoby.exe -> KILLED [TermProc]
[SUSP PATH] beanifkeafal.exe -- C:\ProgramData\beanifkeafal.exe -> KILLED [TermProc]
[SUSP PATH] pibmyrpimqaq.exe -- C:\ProgramData\pibmyrpimqaq.exe -> KILLED [TermProc]
[SUSP PATH] qykopigturuq.exe -- C:\ProgramData\qykopigturuq.exe -> KILLED [TermProc]
[SUSP PATH] xadweffumdeq.exe -- C:\ProgramData\xadweffumdeq.exe -> KILLED [TermProc]
[SUSP PATH] jafatgortycx.exe -- C:\ProgramData\jafatgortycx.exe -> KILLED [TermProc]
[SUSP PATH] koxyfyvobnog.exe -- C:\ProgramData\koxyfyvobnog.exe -> KILLED [TermProc]
[SUSP PATH] vyfalperyfir.exe -- C:\ProgramData\vyfalperyfir.exe -> KILLED [TermProc]
[SUSP PATH] daxixreameam.exe -- C:\ProgramData\daxixreameam.exe -> KILLED [TermProc]
[SUSP PATH] qyftegoblari.exe -- C:\ProgramData\qyftegoblari.exe -> KILLED [TermProc]
[SUSP PATH] senamakaqjus.exe -- C:\ProgramData\senamakaqjus.exe -> KILLED [TermProc]
[SUSP PATH] hotnomjyzoby.exe -- C:\Users\Win7\hotnomjyzoby.exe -> KILLED [TermProc]
[SUSP PATH] beanifkeafal.exe -- C:\Users\Win7\beanifkeafal.exe -> KILLED [TermProc]
[SUSP PATH] pibmyrpimqaq.exe -- C:\Users\Win7\pibmyrpimqaq.exe -> KILLED [TermProc]
[SUSP PATH][DLL] rundll32.exe -- C:\Windows\System32\rundll32.exe : C:\Users\Win7\au48qsnx.dll -> KILLED [TermProc]
[SUSP PATH] qykopigturuq.exe -- C:\Users\Win7\qykopigturuq.exe -> KILLED [TermProc]
[SUSP PATH] Clients.exe -- C:\Users\Win7\AppData\Roaming\Clients.exe -> KILLED [TermProc]
[SUSP PATH] xadweffumdeq.exe -- C:\Users\Win7\xadweffumdeq.exe -> KILLED [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\svchost.exe -> KILLED [TermProc]
[SUSP PATH] jafatgortycx.exe -- C:\Users\Win7\jafatgortycx.exe -> KILLED [TermProc]
[SUSP PATH] koxyfyvobnog.exe -- C:\Users\Win7\koxyfyvobnog.exe -> KILLED [TermProc]
[SUSP PATH] vyfalperyfir.exe -- C:\Users\Win7\vyfalperyfir.exe -> KILLED [TermProc]
[SUSP PATH] daxixreameam.exe -- C:\Users\Win7\daxixreameam.exe -> KILLED [TermProc]
[SUSP PATH] qyftegoblari.exe -- C:\Users\Win7\qyftegoblari.exe -> KILLED [TermProc]
[SUSP PATH] senamakaqjus.exe -- C:\Users\Win7\senamakaqjus.exe -> KILLED [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe -> KILLED [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe -> KILLED [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe -> KILLED [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe -> KILLED [TermProc]
¤¤¤ Registry Entries : 151 ¤¤¤
[RUN][SUSP PATH] HKCU\[...]\Run : Fpwiwn (C:\Windows\system32\config\systemprofile\AppData\Roaming\Fpwiwn.scr) -> FOUND
[RUN][HJNAME] HKCU\[...]\Run : Windows Media Center (C:\Users\Win7\AppData\Roaming\smss.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : hotnomjyzoby (C:\Users\Win7\hotnomjyzoby.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : beanifkeafal (C:\Users\Win7\beanifkeafal.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : rrvrue (C:\Users\Win7\ehtpnd.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : pibmyrpimqaq (C:\Users\Win7\pibmyrpimqaq.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : Microsoft Antivirus Scanner (rundll32.exe C:\Users\Win7\au48qsnx.dll,Init) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : qykopigturuq (C:\Users\Win7\qykopigturuq.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : Clients (C:\Users\Win7\AppData\Roaming\Clients.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : xadweffumdeq (C:\Users\Win7\xadweffumdeq.exe) -> FOUND
[RUN][HJNAME] HKCU\[...]\Run : svchosta (C:\Windows\svchost.exe) -> FOUND
[RUN][HJNAME] HKCU\[...]\Run : svchost.exe (C:\Windows\svchost.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : jafatgortycx (C:\Users\Win7\jafatgortycx.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : koxyfyvobnog (C:\Users\Win7\koxyfyvobnog.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : vyfalperyfir (C:\Users\Win7\vyfalperyfir.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : daxixreameam (C:\Users\Win7\daxixreameam.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : qyftegoblari (C:\Users\Win7\qyftegoblari.exe) -> FOUND
[RUN][SUSP PATH] HKCU\[...]\Run : senamakaqjus (C:\Users\Win7\senamakaqjus.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : hotnomjyzoby (C:\ProgramData\hotnomjyzoby.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : beanifkeafal (C:\ProgramData\beanifkeafal.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : pibmyrpimqaq (C:\ProgramData\pibmyrpimqaq.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : qykopigturuq (C:\ProgramData\qykopigturuq.exe) -> FOUND
[RUN][HJNAME] HKLM\[...]\Run : Windows Media Center (C:\Windows\smss.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : xadweffumdeq (C:\ProgramData\xadweffumdeq.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : hwpfvisxt (C:\Users\Win7\nprtjb.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : conx (C:\Windows\System32\config\systemprofile\AppData\Roaming\wb2ek.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : jafatgortycx (C:\ProgramData\jafatgortycx.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : koxyfyvobnog (C:\ProgramData\koxyfyvobnog.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : vyfalperyfir (C:\ProgramData\vyfalperyfir.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : daxixreameam (C:\ProgramData\daxixreameam.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : qyftegoblari (C:\ProgramData\qyftegoblari.exe) -> FOUND
[RUN][SUSP PATH] HKLM\[...]\Run : senamakaqjus (C:\ProgramData\senamakaqjus.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : Fpwiwn (C:\Windows\system32\config\systemprofile\AppData\Roaming\Fpwiwn.scr) -> FOUND
[RUN][HJNAME] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : Windows Media Center (C:\Users\Win7\AppData\Roaming\smss.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : hotnomjyzoby (C:\Users\Win7\hotnomjyzoby.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : beanifkeafal (C:\Users\Win7\beanifkeafal.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : rrvrue (C:\Users\Win7\ehtpnd.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : pibmyrpimqaq (C:\Users\Win7\pibmyrpimqaq.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : Microsoft Antivirus Scanner (rundll32.exe C:\Users\Win7\au48qsnx.dll,Init) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : qykopigturuq (C:\Users\Win7\qykopigturuq.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : Clients (C:\Users\Win7\AppData\Roaming\Clients.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : xadweffumdeq (C:\Users\Win7\xadweffumdeq.exe) -> FOUND
[RUN][HJNAME] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : svchosta (C:\Windows\svchost.exe) -> FOUND
[RUN][HJNAME] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : svchost.exe (C:\Windows\svchost.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : jafatgortycx (C:\Users\Win7\jafatgortycx.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : koxyfyvobnog (C:\Users\Win7\koxyfyvobnog.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : vyfalperyfir (C:\Users\Win7\vyfalperyfir.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : daxixreameam (C:\Users\Win7\daxixreameam.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : qyftegoblari (C:\Users\Win7\qyftegoblari.exe) -> FOUND
[RUN][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Run : senamakaqjus (C:\Users\Win7\senamakaqjus.exe) -> FOUND
[RUN][ROGUE ST] HKLM\[...]\Policies\Explorer\\Run : 3289 (C:\PROGRA~2\LOCALS~1\Temp\msjkourh.scr) -> FOUND
[SHELL][SUSP PATH] HKCU\[...]\Windows : Load (C:\Users\Win7\LOCALS~1\Temp\msavfk.exe) -> FOUND
[SHELL][SUSP PATH] HKUS\S-1-5-21-1376724605-2322160143-2511619695-1000[...]\Windows : Load (C:\Users\Win7\LOCALS~1\Temp\msavfk.exe) -> FOUND
[Services][ROGUE ST] HKLM\[...]\ControlSet001\Services\{95808DC4-FA4A-4c74-92FE-5B863F82066B} (\??\C:\Program Files\CyberLink\PowerDVD\000.fcl) -> FOUND
[Services][ROGUE ST] HKLM\[...]\ControlSet002\Services\{95808DC4-FA4A-4c74-92FE-5B863F82066B} (\??\C:\Program Files\CyberLink\PowerDVD\000.fcl) -> FOUND
[STARTUP][SUSP PATH] 0llfv9q.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0llfv9q.exe -> FOUND
[STARTUP][SUSP PATH] 0qql1fa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0qql1fa.exe -> FOUND
[STARTUP][SUSP PATH] 0vq0k0k.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0vq0k0k.exe -> FOUND
[STARTUP][SUSP PATH] 1aqql1f.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\1aqql1f.exe -> FOUND
[STARTUP][SUSP PATH] 1fv9qql.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\1fv9qql.exe -> FOUND
[STARTUP][SUSP PATH] 1gaaaav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\1gaaaav.exe -> FOUND
[STARTUP][SUSP PATH] 1qkkfv9.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\1qkkfv9.exe -> FOUND
[STARTUP][SUSP PATH] 1qqlaav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\1qqlaav.exe -> FOUND
[STARTUP][SUSP PATH] 21aavvq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\21aavvq.exe -> FOUND
[STARTUP][SUSP PATH] 21lgwwq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\21lgwwq.exe -> FOUND
[STARTUP][SUSP PATH] 2kkfvvq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\2kkfvvq.exe -> FOUND
[STARTUP][SUSP PATH] 31faqq1.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\31faqq1.exe -> FOUND
[STARTUP][SUSP PATH] 31pkaa1.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\31pkaa1.exe -> FOUND
[STARTUP][SUSP PATH] 3kkfv98.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\3kkfv98.exe -> FOUND
[STARTUP][SUSP PATH] 4fvvqff.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\4fvvqff.exe -> FOUND
[STARTUP][SUSP PATH] 4v2qlaa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\4v2qlaa.exe -> FOUND
[STARTUP][SUSP PATH] 5faavqq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\5faavqq.exe -> FOUND
[STARTUP][SUSP PATH] 5kkfv9f.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\5kkfv9f.exe -> FOUND
[STARTUP][SUSP PATH] 5lvvqg0.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\5lvvqg0.exe -> FOUND
[STARTUP][SUSP PATH] 6g6avqq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\6g6avqq.exe -> FOUND
[STARTUP][SUSP PATH] 7vqllf5.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\7vqllf5.exe -> FOUND
[STARTUP][SUSP PATH] 9a0vq0k.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\9a0vq0k.exe -> FOUND
[STARTUP][SUSP PATH] 9q7lflq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\9q7lflq.exe -> FOUND
[STARTUP][SUSP PATH] a1vqggaav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\a1vqggaav.exe -> FOUND
[STARTUP][SUSP PATH] a2qlaa1llg.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\a2qlaa1llg.exe -> FOUND
[STARTUP][SUSP PATH] a8ql1faavla.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\a8ql1faavla.exe -> FOUND
[STARTUP][SUSP PATH] aa1llggbqql.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aa1llggbqql.exe -> FOUND
[STARTUP][SUSP PATH] aa1vqggaav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aa1vqggaav.exe -> FOUND
[STARTUP][SUSP PATH] aavk4fvvq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aavk4fvvq.exe -> FOUND
[STARTUP][SUSP PATH] aavllfv9q.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aavllfv9q.exe -> FOUND
[STARTUP][SUSP PATH] aavllfv9qqq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aavllfv9qqq.exe -> FOUND
[STARTUP][SUSP PATH] akaqffaav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\akaqffaav.exe -> FOUND
[STARTUP][SUSP PATH] aqffaavllf.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\aqffaavllf.exe -> FOUND
[STARTUP][SUSP PATH] av5q2ga2427.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\av5q2ga2427.exe -> FOUND
[STARTUP][SUSP PATH] av9q0lg0a.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\av9q0lg0a.exe -> FOUND
[STARTUP][SUSP PATH] avkkfv98.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\avkkfv98.exe -> FOUND
[STARTUP][SUSP PATH] avqq7lgaavv.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\avqq7lgaavv.exe -> FOUND
[STARTUP][SUSP PATH] fa2qlaa1.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fa2qlaa1.exe -> FOUND
[STARTUP][SUSP PATH] faa7vqll.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\faa7vqll.exe -> FOUND
[STARTUP][SUSP PATH] faavqq6kf.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\faavqq6kf.exe -> FOUND
[STARTUP][SUSP PATH] fappkkfvvp.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fappkkfvvp.exe -> FOUND
[STARTUP][SUSP PATH] faqqkkfkvq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\faqqkkfkvq.exe -> FOUND
[STARTUP][SUSP PATH] fav9faav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fav9faav.exe -> FOUND
[STARTUP][SUSP PATH] ffvvqf9a0.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ffvvqf9a0.exe -> FOUND
[STARTUP][SUSP PATH] fv9qqlf9a.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fv9qqlf9a.exe -> FOUND
[STARTUP][SUSP PATH] fvvqf9a0vq0.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fvvqf9a0vq0.exe -> FOUND
[STARTUP][SUSP PATH] fvvqf9a0vqq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\fvvqf9a0vqq.exe -> FOUND
[STARTUP][SUSP PATH] g6avqq7lg.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\g6avqq7lg.exe -> FOUND
[STARTUP][SUSP PATH] gbqqlb98wq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\gbqqlb98wq.exe -> FOUND
[STARTUP][SUSP PATH] gvvqg0a0.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\gvvqg0a0.exe -> FOUND
[STARTUP][SUSP PATH] kf5a2qkaa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kf5a2qkaa.exe -> FOUND
[STARTUP][SUSP PATH] kf9a0vq0k.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kf9a0vq0k.exe -> FOUND
[STARTUP][SUSP PATH] kff6ppk2.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kff6ppk2.exe -> FOUND
[STARTUP][SUSP PATH] kffaq0k0.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kffaq0k0.exe -> FOUND
[STARTUP][SUSP PATH] l5fvvqff.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\l5fvvqff.exe -> FOUND
[STARTUP][SUSP PATH] l98gav9q.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\l98gav9q.exe -> FOUND
[STARTUP][SUSP PATH] laa1llffa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\laa1llffa.exe -> FOUND
[STARTUP][SUSP PATH] lg1gaavl98.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\lg1gaavl98.exe -> FOUND
[STARTUP][SUSP PATH] lglg16v5.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\lglg16v5.exe -> FOUND
[STARTUP][SUSP PATH] llgaavvq7.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\llgaavvq7.exe -> FOUND
[STARTUP][SUSP PATH] llggbqqlb9.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\llggbqqlb9.exe -> FOUND
[STARTUP][SUSP PATH] lvvlaaf7vl.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\lvvlaaf7vl.exe -> FOUND
[STARTUP][SUSP PATH] pffap9k0ppp.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\pffap9k0ppp.exe -> FOUND
[STARTUP][SUSP PATH] pkaa1kkffaq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\pkaa1kkffaq.exe -> FOUND
[STARTUP][SUSP PATH] q6kfaa7vq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\q6kfaa7vq.exe -> FOUND
[STARTUP][SUSP PATH] q7lfaa7vq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\q7lfaa7vq.exe -> FOUND
[STARTUP][SUSP PATH] q80a0vqql1g.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\q80a0vqql1g.exe -> FOUND
[STARTUP][SUSP PATH] qf0a0vqql1g.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qf0a0vqql1g.exe -> FOUND
[STARTUP][SUSP PATH] qffaqql1.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qffaqql1.exe -> FOUND
[STARTUP][SUSP PATH] qk4fvvqf.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qk4fvvqf.exe -> FOUND
[STARTUP][SUSP PATH] ql1gaavl.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ql1gaavl.exe -> FOUND
[STARTUP][SUSP PATH] qlaaaav9vv.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qlaaaav9vv.exe -> FOUND
[STARTUP][SUSP PATH] qlaqlvq4vv.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qlaqlvq4vv.exe -> FOUND
[STARTUP][SUSP PATH] qlaqv2ql.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qlaqv2ql.exe -> FOUND
[STARTUP][SUSP PATH] qlaqv2qlaa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qlaqv2qlaa.exe -> FOUND
[STARTUP][SUSP PATH] qq1a0vvqf9.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qq1a0vvqf9.exe -> FOUND
[STARTUP][SUSP PATH] qq7lflqav.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qq7lflqav.exe -> FOUND
[STARTUP][SUSP PATH] qqfv5a3laql.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qqfv5a3laql.exe -> FOUND
[STARTUP][SUSP PATH] v2qkaa1k.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\v2qkaa1k.exe -> FOUND
[STARTUP][SUSP PATH] v8qkf9a0vq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\v8qkf9a0vq.exe -> FOUND
[STARTUP][SUSP PATH] vaaa1llg.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vaaa1llg.exe -> FOUND
[STARTUP][SUSP PATH] vkk1vvqqk.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vkk1vvqqk.exe -> FOUND
[STARTUP][SUSP PATH] vlgqvgqql.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vlgqvgqql.exe -> FOUND
[STARTUP][SUSP PATH] vllfv9qqlf9.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vllfv9qqlf9.exe -> FOUND
[STARTUP][SUSP PATH] vllggaqql1.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vllggaqql1.exe -> FOUND
[STARTUP][SUSP PATH] vppvvp5fa.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vppvvp5fa.exe -> FOUND
[STARTUP][SUSP PATH] vqgvqgq2gl.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vqgvqgq2gl.exe -> FOUND
[STARTUP][SUSP PATH] vqqlgg6av.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vqqlgg6av.exe -> FOUND
[STARTUP][SUSP PATH] vvqllggq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vvqllggq.exe -> FOUND
[STARTUP][SUSP PATH] vvqq6aavk4.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\vvqq6aavk4.exe -> FOUND
[STARTUP][SUSP PATH] wq0lggb1wqq.exe @Win7 : C:\Users\Win7\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wq0lggb1wqq.exe -> FOUND
[HJPOL] HKCU\[...]\System : disableregistrytools (0) -> FOUND
[HJ] HKLM\[...]\System : ConsentPromptBehaviorAdmin (0) -> FOUND
[HJ] HKLM\[...]\System : EnableLUA (0) -> FOUND
[HJ DESK] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ DESK] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [LOADED] ¤¤¤
IRP[IRP_MJ_CREATE] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_CLOSE] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_DEVICE_CONTROL] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_POWER] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_SYSTEM_CONTROL] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
IRP[IRP_MJ_PNP] : \SystemRoot\system32\DRIVERS\atapi.sys -> HOOKED ([MAJOR] Unknown @ 0x84FCB1F8)
¤¤¤ Extern Hives: ¤¤¤
-> E:\windows\system32\config\SOFTWARE
-> E:\Users\Alfi\NTUSER.DAT
-> E:\Users\Default\NTUSER.DAT
-> G:\windows\system32\config\SOFTWARE
-> G:\Users\Default\NTUSER.DAT
-> G:\Users\Default User\NTUSER.DAT
-> G:\Users\WIN7\NTUSER.DAT
-> G:\Documents and Settings\Default\NTUSER.DAT
-> G:\Documents and Settings\Default User\NTUSER.DAT
-> G:\Documents and Settings\WIN7\NTUSER.DAT
¤¤¤ HOSTS File: ¤¤¤
--> C:\Windows\system32\drivers\etc\hosts
127.0.0.1 jL.chura.pl
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: ST3500413AS ATA Device +++++
--- User ---
[MBR] ec9ed4657f9d0f42d4c335f0205aac08
[BSP] 1756590a13b3bb1a236217cdb4feec0c : Windows 7 MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 100 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 206848 | Size: 99899 Mo
2 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 204800000 | Size: 376938 Mo
User = LL1 ... OK!
User = LL2 ... OK!
+++++ PhysicalDrive1: ST3160212AS ATA Device +++++
--- User ---
[MBR] f6d7a2fa25a9b6433786e133ae7d5b75
[BSP] 8b1a12dec96d8a7657aeb604cfdbf253 : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 74998 Mo
1 - [XXXXXX] EXTEN-LBA (0x0f) [VISIBLE] Offset (sectors): 153597465 | Size: 77618 Mo
User = LL1 ... OK!
User = LL2 ... OK!
+++++ PhysicalDrive2: SanDisk Cruzer Slice USB Device +++++
--- User ---
[MBR] 570422272ced4fad5f334efc4b25fae9
[BSP] df4f83c1f72e36823a12b0dfc7617313 : MBR Code unknown
Partition table:
0 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 32 | Size: 15266 Mo
User = LL1 ... OK!
Error reading LL2 MBR!
Finished : << RKreport[1].txt >>
RKreport[1].txt