The latest trend in malware doesn't just flood your computer with annoying advertising or attempt to steal your banking information. Instead, it quite literally locks a system down and prevents the user from doing anything on it unless a ransom is paid.
The most recent "ransomware" was detected by abuse.ch and uses a drive-by exploit kit called "Blackhole." This cheap malware can be purchased via underground forums and infects systems through one or more security vulnerabilities in a web browser or plug-in like Adobe Flash Player, Adobe Reader or Java.
Once infected, the target system becomes locked and users are presented with a bogus region-specific message about why the system is locked and how they can regain control. The ransomware is currently targeting systems in Austria, France, Germany, the Netherlands, Switzerland and the UK.
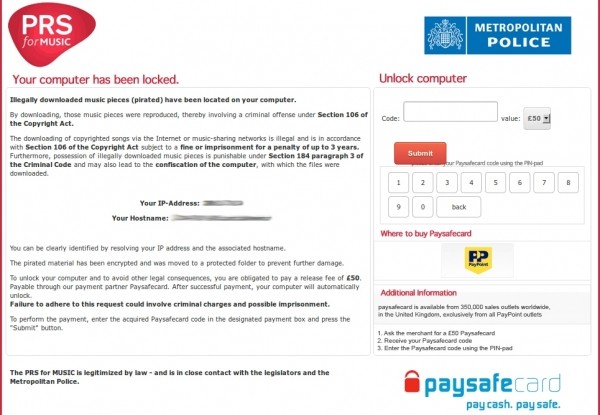
The UK variety tells the user that illegally downloaded music has been detected on their machine and attempts to incite fear by highlighting penalties that could result from such material. In this example, users are urged to use PaySafe to transfer £50 ($80) to unlock the computer.
Once complete, the system is "unlocked" and unsuspecting users are none the wiser. But in addition to the ransom, this kit installs another piece of malware called Aldi Bot that is used to steal login credentials as well as initiate DDoS attacks.
The malware author is suspected to be of Russian descent since all of the domain names point to a Russian web provider.
As always, the best defense against drive-by attacks is to keep your browser, plug-ins and anti-virus protection up to date.
Briefcase image from Shutterstock.