Mozilla has warned Firefox users to disable Oracle's Java software framework plugin after researchers discovered that cybercriminals are actively exploiting yet another zero-day vulnerability in the cross-platform software. Atif Mushtaq, a security researcher for FireEye, first discovered the flaw in the wild (CVE-2012-4681) on Sunday and successfully used it to breach his test machine running Firefox with JRE 1.7 update 6 installed. It remains unpatched by Oracle and currently poses a risk to all 1.7x versions of Java.
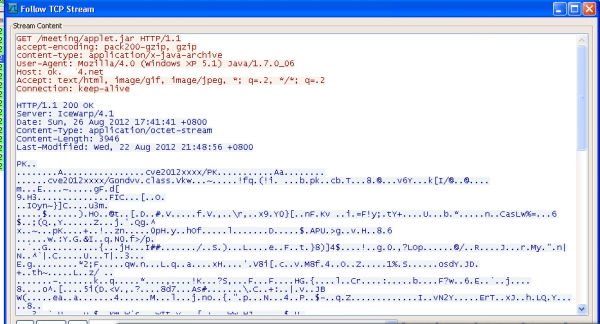
Mushtaq said the exploit is hosted on the domain ok.xxx4.net which resolved to Taiwan at the time of writing. If it compromises your computer, it can install Dropper.Ms.PMs with data sent back to separate command and control servers using the IP 223.25.233.244, which resolves to Singapore.
On Monday, researchers Andre DiMino and Mila Parkour posted that the exploit appears to install the Poison Ivy remote access Trojan, although the number of infections are currently low. That said, Oracle typically sticks to a quarterly update cycle, so a patch could be weeks or months away and with the exploit code becoming more readily available on underground sites, we could witness a dramatic increase in infections.
"As a user, you should take this problem seriously, because there is currently no patch from Oracle," a Rapid7 exploit developer said. "For now, our recommendation is to completely disable Java until a fix is available."
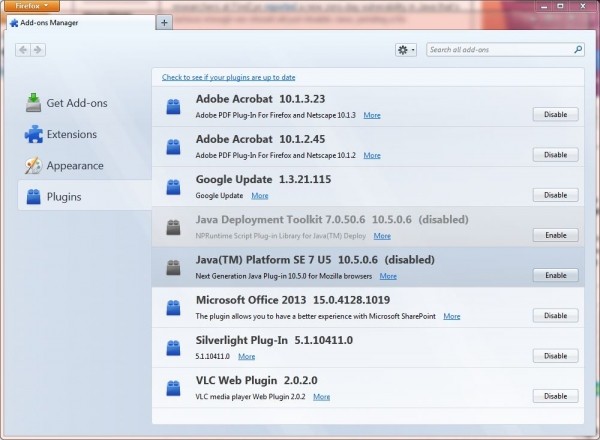
In the meantime, those that don't require Java for essential use should consider disabling it to reduce the risk of infection. This can be achieved in the plugin section of most browsers, though IE users can use this blog post for guidance. To ensure it has been disabled, you can test whether Java is running by heading to Oracle's Java test page.