Apple's OS X operating system has long been a relatively unpopular target for malware coders, but that's changing with the platform's rise in popularity. Today Russian security website Doctor Web is reporting on a new trojan targeting Mac users that silently installs a browser plug-in to inject ads into pages visited by users.
The threat, labeled "Trojan.Yontoo.1", is reportedly being distributed through movie trailer pages that prompt users to install a browser plugin, a media player, a video quality enhancement program, or a download accelerator. It cannot install itself and instead relies on tricking users into downloading and installing it.
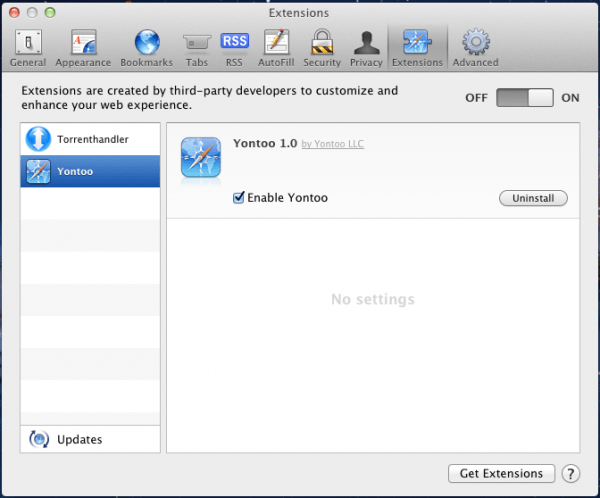
From there it's a similar situation as described late last year in what was believed to be the first fake-installer Trojan for OS X. Users see the usual installation screens but instead of loading the promised program – in this case something called "Free Twit Tube" – the Trojan will install plug-ins for Safari, Chrome and Firefox. These plug-ins transmits information about the loaded pages to a remote server as the user browsers the web, and with this information it's able to load third-party ads on any website – such as Apple.com as shown below.
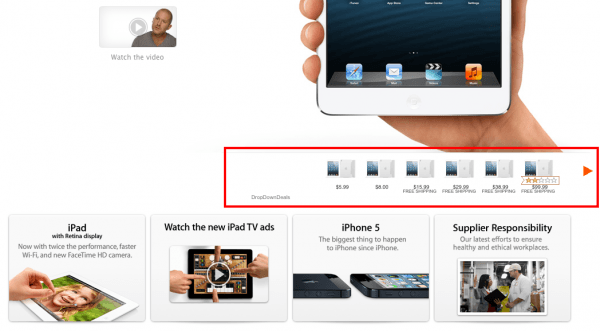
There's no mention of whether Lion and Mountain Lion's Gatekeeper is able stop the installer in its tracks, though it should be the case with the default setting preventing unsigned code from being executed.
According to Symantec, a variant targeting Windows PCs has been spotted in the wild as well, although in that case the Trojan doesn't seem to affect Windows 8 and is centered around Facebook ads.
Though it may be obvious to anyone who knows its way around a computer, the best defense from these types of scams is simple: always download software from trusted sources or from the developers themselves.