A sophisticated piece of malware known as "Regin" has been spying on government organizations, infrastructure operators, businesses, researchers and private individuals since at least 2008. The backdoor-type Trojan is said to display a degree of technical competence rarely seen and would have required a significant investment of time and resources to create according to Symantec.
The design of the malware makes it suitable for long-term surveillance operations against a range of international targets and can even be customized with a range of capabilities depending on the target. The customization uses a modular approach similar to what has been seen in other sophisticated malware including Flamer and Weevil (The Mask).
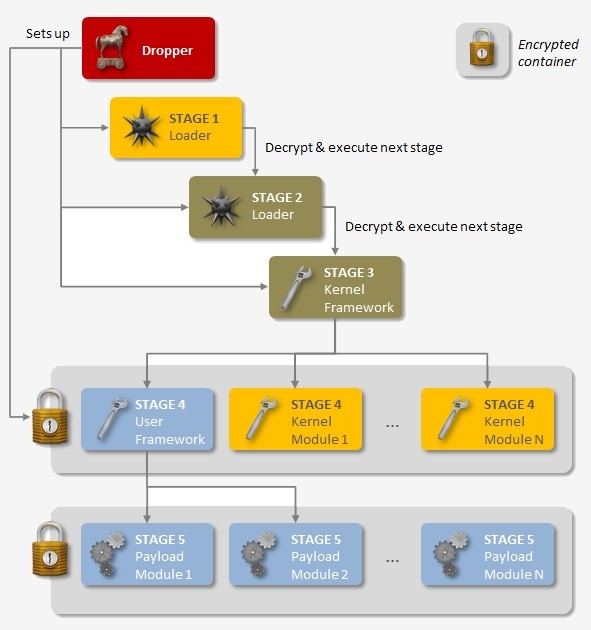
Regin is said to be a multi-staged thread with all but the first stage hidden and encrypted. The first stage sets off a domino effect that decrypts and loads the next stage, ultimately going five levels deep.
This tiered structure makes it incredibly difficult to gather much of any information on the complete package. Only when someone has access to all five stages do things start to come together.
Symantec estimates its development took months, if not years, to complete. Based on analysis of its structure, its authors - likely a nation state - clearly went to great lengths to cover their tracks.
Symantec further notes that infections have been observed between 2008 and 2011. At some point in 2011, use of Regin was abruptly halted. In 2013, however, a revised version resurfaced and has been active ever since. There are likely many components of the malware that remain undiscovered and additional functionality and versions may exist.
