Researchers earlier this week uncovered malware actively targeting more than a dozen Cisco routers across four different countries. Dubbed SYNful Knock, the malware introduces a backdoor that grants attackers access to a targeted network.
The attacks, as it turns out, are much more widespread than previously thought.
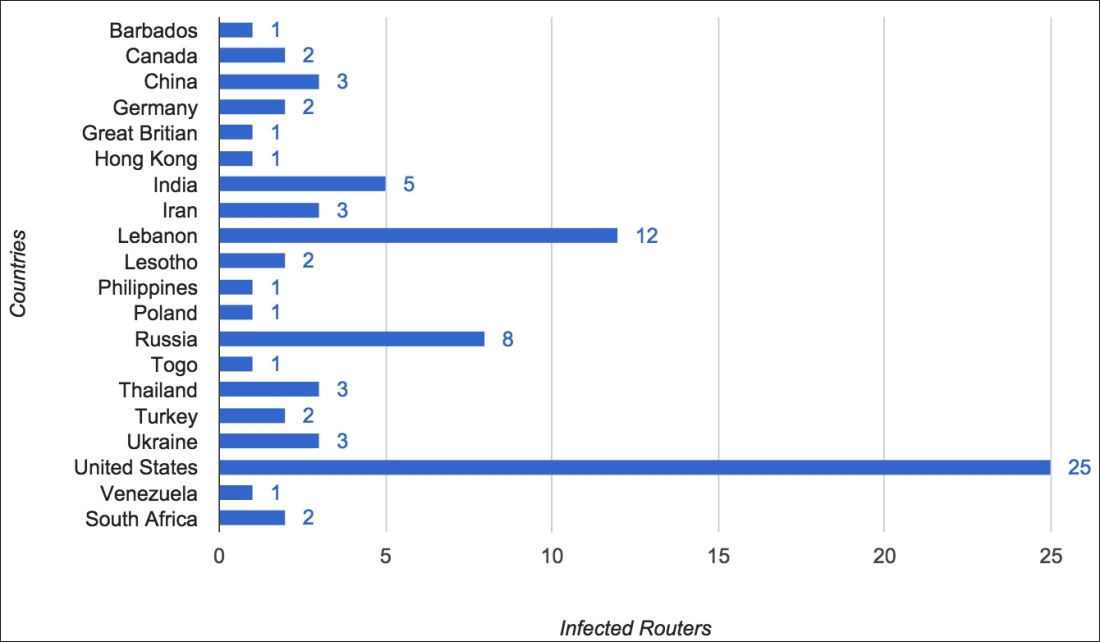
As Ars Technica notes, a team of computer scientists from ZMap recently scanned the entire IPv4 address space in search of infected devices. They did this by sending out-of-sequence TCP packets to every Internet address, part of the method used to activate SYNful Knock. By doing this, the team found 79 devices across 19 countries were infected including an ISP in the US hosting 25 infected boxes.
Security firm FireEye detailed SYNful Knock on September 15. It's characterized by the fact that it loads each time the router is restarted and supports up to 100 modules that can be tailored to each target.
It's worth clarifying that SYNful Knock isn't exploiting a vulnerability in Cisco devices. Instead, attackers appear to be taking advantage of routers that are using default passwords (or perhaps the attackers are using some other method to get passwords).
Ars points out that it's now clear that SYNful Knock is a professionally-developed, full-feature backdoor that's likely state-sponsored. While it's not outside the realm of possibility that some of the 79 infected devices in the recent scans are honeypots, odds are, not all of them are.
Graph courtesy ZMap