The big picture: Encryption is a feature that is typically only used on higher performing devices because of the delays it can cause. Google's new Adiantum adaptation of existing encryption methods make secure encryption methods faster, and thus viable for use on even the cheapest hardware used today.
Since the debut of Android 6.0, most phones have been using AES encryption as the standard means of protecting user data. Google has made disk encryption support a requirement, but there are still a handful of budget devices that are not using encryption at all due to performance concerns. Exceptions allow devices with encryption performance of less than 50MiB/s to disable the feature by default.
Android as an operating system has valid reasons why encryption cannot be forced on at all times. Extremely inexpensive Android Go phones, smartwatches, and TVs do not necessarily have hardware support for AES encryption due to the use of less costly processors. Performance would be abysmal on some of these devices if encryption operations had to happen without hardware acceleration.
Now that hardware is good enough on budget devices to handle more than just the basic operating requirements, Google has developed a new encryption mode called Adiantum that has drastically better performance than AES when used on budget hardware. Adiantum uses the ChaCha stream cipher that is part of TLS for HTTPS traffic and borrowed a few ideas from AES to keep file sizes the same before and after encryption.
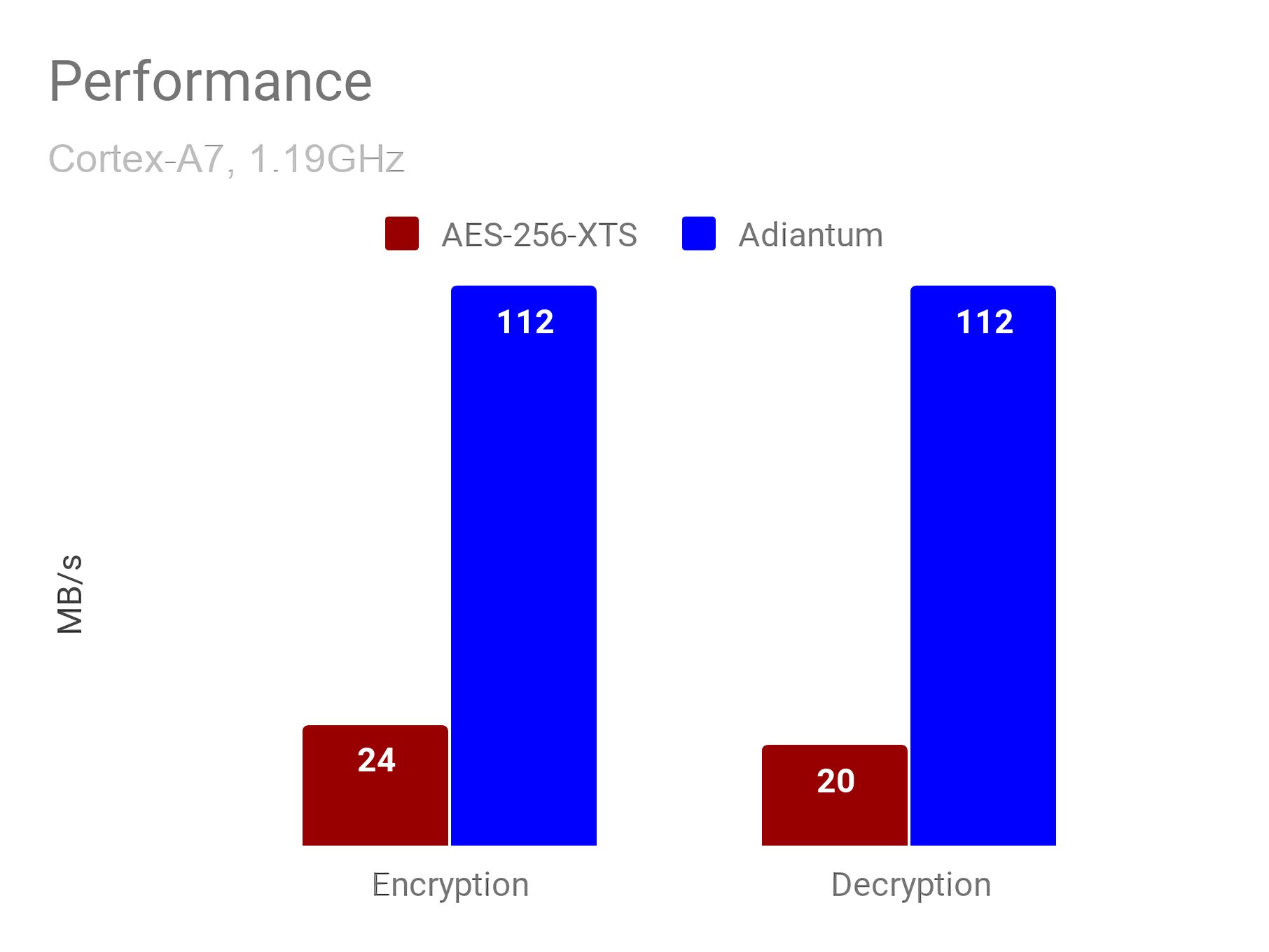
Google's benchmark shows that Adiantum is nearly five times faster than AES on a Cortex-A7 processor. Working with 4096-byte sectors, it takes approximately 10.6 clock cycles per byte to encrypt or decrypt data. Full disk encryption using Adiantum is now a reasonable option for devices using even the cheapest of processors.
One of the secrets to getting Adiantum to run so quickly on budget hardware is the fact that it mainly uses additions, rotations, and XOR operations that are supported on all common microprocessors. Despite the use of simple operations, Google states that they, "are in a position to have high confidence in its security."
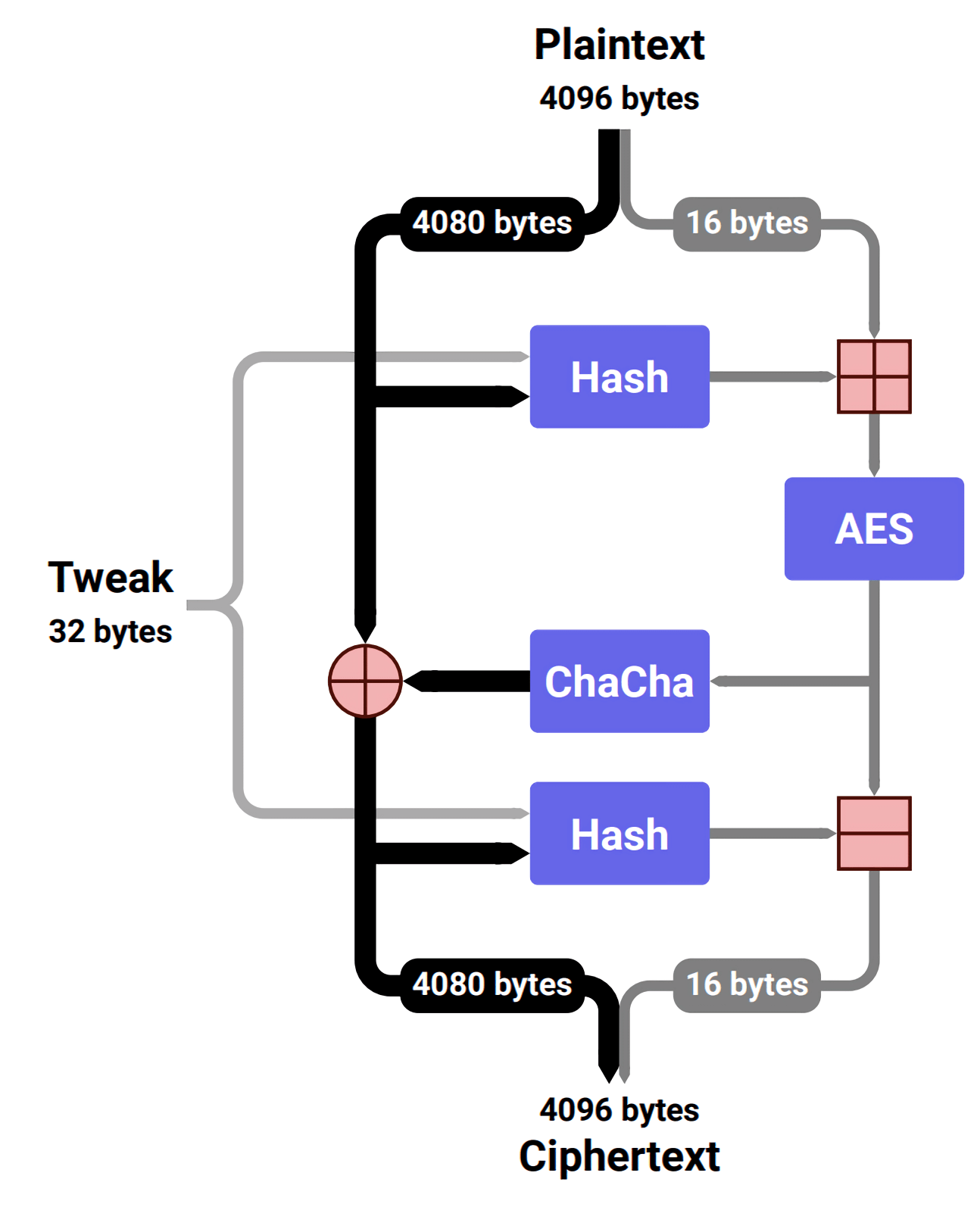
All of the components that make up Adiantum are elements borrowed from other algorithms that are believed to be secure. Google does note that up to seven rounds of ChaCha have been broken dating back to 2008, but nobody has been able to crack eight rounds over a decade later even with all the hardware improvements that have come along. Adiantum makes use of 12 rounds, indicating that it is safe for the foreseeable future.
The full details of Adiantum are available in a paper published by Google through the International Association for Cryptologic Research.