TL;DR: A new study analyzing more than 19 billion passwords from relatively recent data breaches between April 2024 and 2025 has found that the vast majority are weak. Alarmingly, only six percent of the leaked passwords were unique, leading researchers to describe a widespread epidemic of weak password reuse.

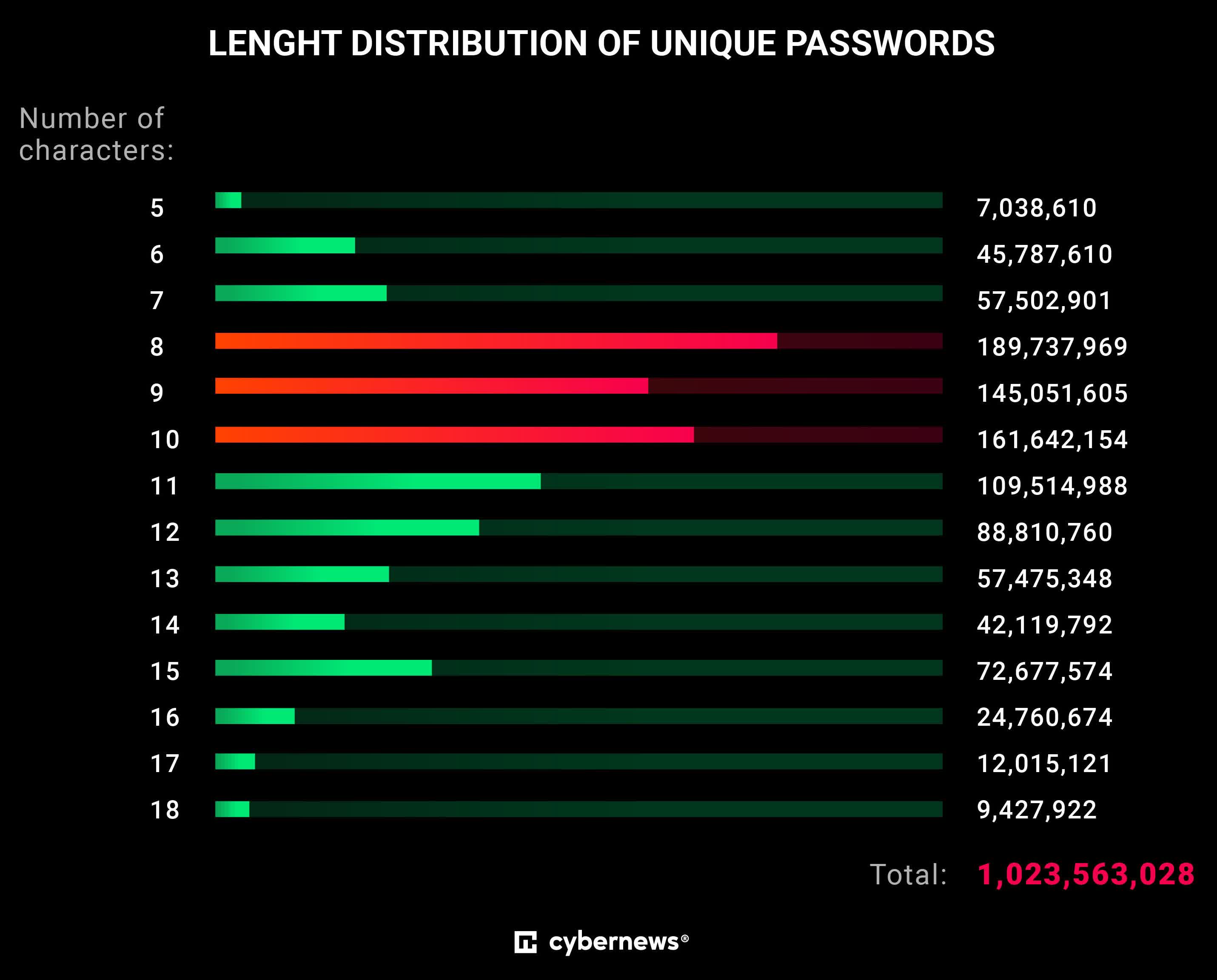
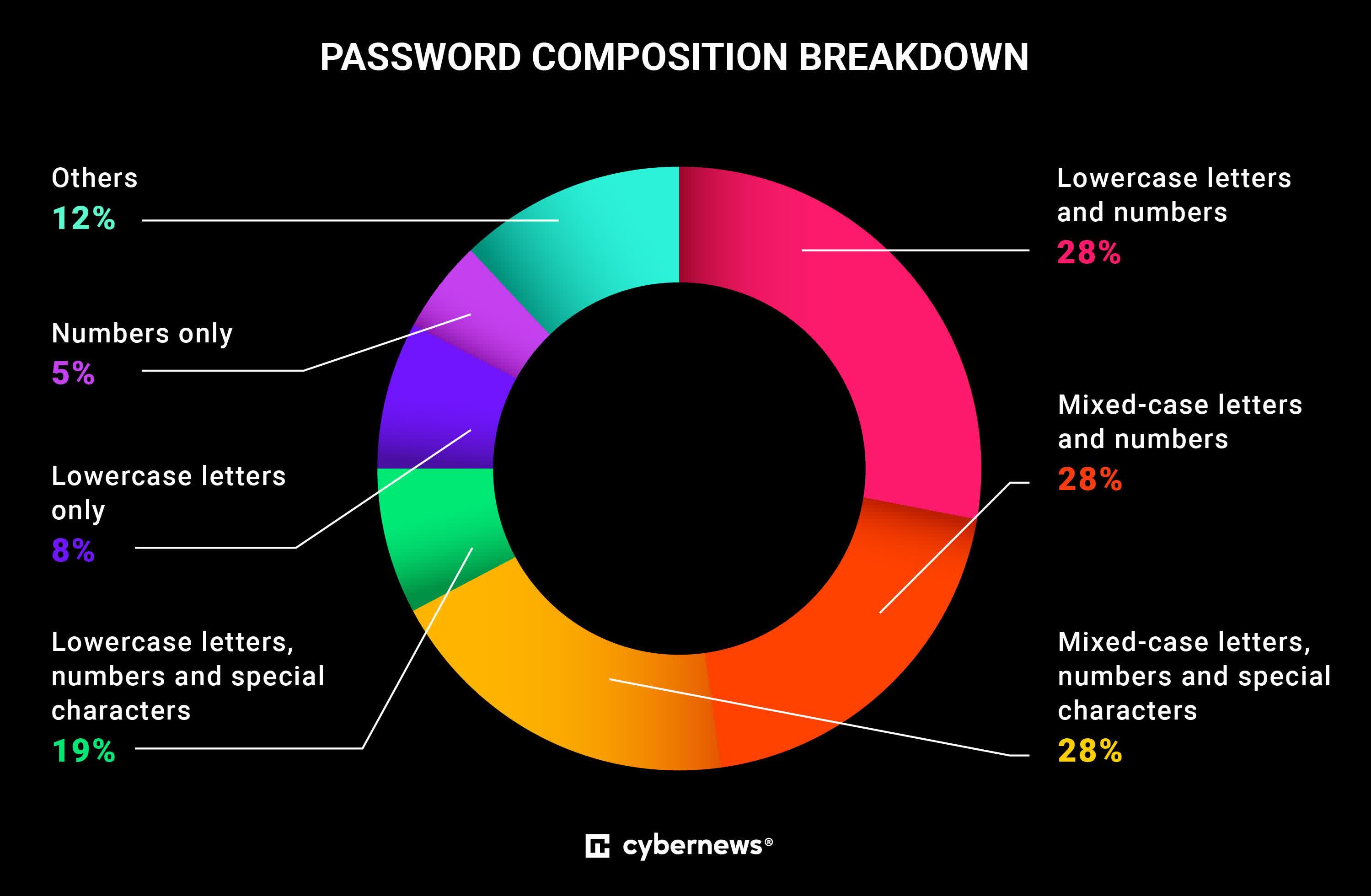
Researchers with Cybernews found that most people (42 percent) use passwords that are eight to 10 characters in length, and that close to a third of those analyzed (27 percent) consist of only numbers and lowercase letters. Most online systems require passwords be at least eight characters in length – if not for this requirement, many would no doubt opt for even shorter passwords.
Other popular trends include the use of common names, curse words, cities, countries foods, and animals in passwords.
Despite decades of education on the topic, password security is clearly still a major issue that largely boils down to laziness. Creating a unique and strong password isn't difficult at all, but remembering it is. Unless you physically write them down, it can be next to impossible to remember unique, strong passwords for every account you own.
Instead, many rely on "default" passwords to help secure online accounts. For example, the sequence "1234" was detected in more than 727 million passwords the team analyzed. "Password" was found in 56 million entries and "admin" was used in 53 million. The problem, of course, is that attackers also priorities these common character strings when building word lists to crack a password.
Are Passwords Dead? What Are Passkeys, and Why Everyone's Talking About Them
There are several viable solutions to strengthen online accounts, including password managers and two-factor authentication, but using them takes extra work which goes back to the laziness problem.
The study looked at 19,030,305,929 passwords – 213 GB worth – gathered from around 200 cybersecurity incidents dating back to April 2024. The data was then filtered and anonymized to ensure no personally identifiable information could be gleaned.
After studying 19 billion passwords, one big problem: Over 90% are terrible