Bottom line: The most alarming aspect of FakeCall is its ability to simulate incoming calls from bank employees. This feature is designed to reassure victims that nothing is amiss and to trick them into divulging account credentials through social engineering tactics.

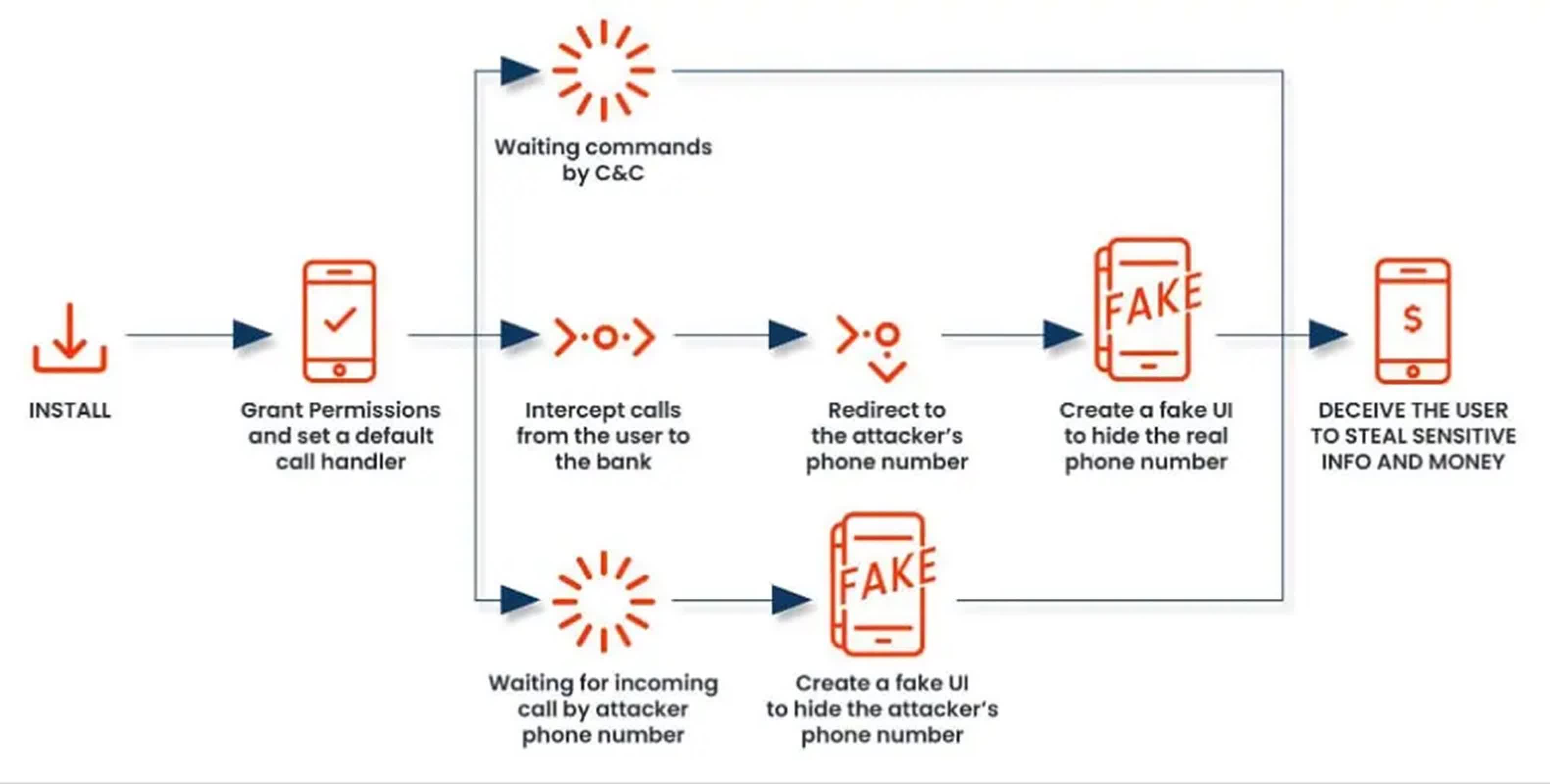
First identified in 2022, FakeCall is a malicious piece of software that was developed to hijack bank accounts. It does this by intercepting calls made to financial institutions and then redirecting them to cybercriminals who impersonate bank representatives to extract sensitive information and gain unauthorized access to victims' funds – a con called voice phishing, or "vishing" for short. In the years since, it has undergone significant evolution and reemerged with alarming new capabilities, presenting an even greater danger to Android users around the world.
A total of 13 new variants of FakeCall have been discovered by researchers at mobile security firm Zimperium. They showcase a range of new and enhanced capabilities that indicate a substantial investment by the attackers.
One of the most significant advancements is the increased level of obfuscation employed by the malware. The new variants utilize a dynamically decrypted and loaded .dex file to conceal their malicious code, making detection and analysis more challenging.
FakeCall's primary method of infection is similar to the earlier versions. The malware typically enters a victim's device through a phishing attack, tricking users into downloading an APK file that acts as a dropper. Once installed, this dropper deploys the malicious payload, establishing communication with a Command and Control (C2) server.
The malware's core functionality revolves around its ability to intercept and manipulate phone calls. When installed, FakeCall prompts the user to set it as the device's default call handler. This seemingly innocuous request grants the malware extensive control over all incoming and outgoing calls.
FakeCall's sophisticated call interception system allows it to monitor outgoing calls and transmit this information to its C2 server. When a victim attempts to contact their bank, the malware can redirect the call to a number controlled by the attackers. To maintain the deception, FakeCall displays a convincing fake user interface that mimics the legitimate Android call interface, complete with the real bank's phone number.
The latest variants of FakeCall introduce several new components, some of which appear to be still in development. A Bluetooth Receiver monitors Bluetooth status and changes, though its exact purpose remains unclear. Similarly, a Screen Receiver monitors the screen's state without any apparent malicious activity in the source code.
A new Accessibility Service, inherited from the Android Accessibility Service, grants the malware significant control over the user interface and the ability to capture information displayed on the screen; this demonstrates the malware's increased sophistication. Based on analysis of earlier versions, it could potentially monitor dialer activity, automatically grant permissions to the malware, and even allow remote attackers to take full control of the victim's device UI.
Additionally, a Phone Listener Service acts as a bridge between the malware and its command and control server, enabling attackers to issue commands and execute actions on the infected device.
Android malware intercepts calls to banks, redirecting victims to fraudulent numbers